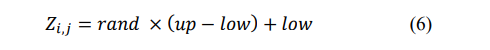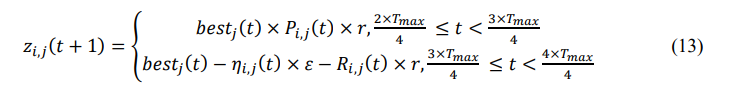IJCNC 03
IoT Resource Allocation and Optimization Using Improved Reptile Search Algorithm
Prabhakar Narasappa Kota1, Pravin Balaso Chopade1, Bhagvat D. Jadhav2, PravinMarotrao Ghate2
and Shankar Dattatray Chavan3
1Department of Electronics &Telecommunications, MES’s College of
Engineering, Pune, India
2Department of Electronics and Telecommunication, JSPM’s Rajarshi Shahu College of
Engineering, Pune, India
3Department of Electronics and Telecommunication Engineering, Dr. D. Y. Patil Institute
of Technology, Pimpri
ABSTRACT
The Internet of Things (IoT) is a dispersed network system that connects the world through the Internet. The architecture of IoT consists of more gateways and resources which cannot be allocated in a manual process. The allocation of resources in IoT is a challenging process due to the higher consumption of energy and high latency rate. To overcome the challenges in existing works, this research introduced an Improved Reptile Search Algorithm (IRSA) to solve the optimization problem which occurs during the time of allocation resources among IoT networks. IRSA employs the methodology of levy flight and cross-over to update the candidate position and enhance the search speed in a single iteration. The proposed method consumes less energy and has low latency during data transmission from User equipment (UE) to the base station.IRSA has been compared with the existing Scalable Resource Allocation Framework (SRAF) and Improved Chaotic Firefly Algorithm (ICFA). The obtained experimental results show that the proposed IRSA attained better performance with an allocation rate of 96.40% which is comparatively higher than SRAF and ICFA with 92.40% and 91.67% respectively.
KEYWORDS
Crossover, Improved Reptile Search Algorithm, Internet of Things, Levy flight, Resource Allocation
1. INTRODUCTION
In recent days, the Internet of Things is developed as an essential part of the daily life of an individual. The usage of IoT in real-time applications includes medical, automation, smart building, etc [1-4]. The networks of IoT are multi-hop ad hoc networks that are created using more sensor nodes deployed in a supervised region. IoT networks are utilized in highly functional applications through the cooperation of nodes [5]. During resource allocation, IoT device needs better Quality of Service (QoS) while implementing it in the node with energy-efficient configurations [6]. The resource allocation leads the physical IoT networks to different types of virtual networks which is considered an advantageous process to ensure better QoS [7]. The lack of efficient resource allocation leads to a major effect on the performance of IoT networks [8]. The resource allocation technique can be accessed using the cost and efficiency of different processing techniques. The resource allocation can be performed based on two methodologies such as scheduling and random access. [9]. The process of scheduling takes place by creating an interaction among the nodes with varying geographical locations and allocating suitable resources to tasks [10].
Energy consumption is a major drawback in the uplink and downlink of IoT networks. This can be reduced by the allocation of channels and sub-channel’s bandwidth [11,12]. Moreover, the resource allocation process serves as an energy saver and helps to improvise the capability of IoT networks [13]. One of the most important study areas is the IoT Resource Allocation Problem (IRAP), which considers how to lower the costs of traffic among gateways, appliances, etc. The performance of wireless communication and foundation devices can both be improved using an efficient resource allocation mechanism [14]. There are numerous optimization issues have aroused while solving the problems related to allocation of resources. These problems can be overwhelmed using evolutionary optimization techniques which make an effort to maximize the probability to obtain solution to challenging problems [15,16,17,18]. This research is motivated by finding an optimal solution for the resource allocation problem with minimum energy consumption and delay. To overcome the fore mentioned problems, this research used an effective heuristics algorithm to enhance the convergence and aids in solving the allocation problem. The major objective of this research is to provide an optimal heuristic algorithm for optimal resource allocation in IoT networks.
The main contributions of this research are listed as follows:
1. The problems in resource allocation of IoT networks are resolved using IRSA which optimized the allocation issues based on latency and energy consumption.
2. Levy and crossover methodologies are employed in the proposed IRSA which updates the position and enhance the search speed in a single iteration.
The remaining paper is organized as follows, Section 2 represents the related works of the paper. The proposed method is discussed in Section.3. The results and discussion are provided in Section.4. Finally, Section.5 represents the overall conclusion of the paper.
2. RELATED WORKS
Jian Jiao et al. [19] have introduced a joint network stability control and Non-Orthogonal Multiple Access (NOMA) based power allocation in the downlink system of Satellite Internet of Things (S-IoT). The two virtual methods such as data queuing and power expenditure were established to evaluate the efficiency of the introduced method. An optimal solution was provided by the particle swarm optimization algorithm for the issues related to joint allocation. The NOMA combined with Karush-Kuhn-Tucker (KKT) to identify a sub-optimal solution using the NOMA-KKT method. However, the NOMA-KKT method consumed more space when the number of user equipment becomes higher.
Xiaolan Liu et al. [20] have introduced an Efficient Channel Allocation Algorithm (ECAA) which has less complexity while grouping the number of users in uplink communication of IoT networks. The ECAA utilized Markov Decision Process (MDP) to predict the energy arrival and the condition of uncertainty for each user. The MDP methodology attained better power allocation for every individual user and improvise the throughput of the network in the specified network frame. The ECCA attained nearest-optimization performance in the allocation of channels with minimal complexity. However, the performance of the ECCA algorithm was recessive when it comes to the multiple numbers of user equipment.
Zafer Al-Makhadmeh and Amr Tolba [21] have introduced Scalable Resource Allocation Framework (SRAF) in user-based IoT utilizing deep learning techniques. The SARF performs allocation by balancing the availed sources and balancing the processed requests. The joint process of SARF was used to decrease the processing time and the probability of failure in allocation. The SARF allocates the resource by solving the complexities in replication and issues in overloading. The SRAF combines the requests from the user and available resources to fulfill the needs of the user and provide support for long-range access. However, the SARF framework took more time to allocate the resource when implemented with the meta-heuristic approaches.
Zhiyong Wang et al. [22] have introduced a resource allocation scheme in IoT networks using an improved chaotic firefly algorithm. This approach creates a multi-objective optimization based on interference of cognitive radio’s operational environment. Protecting the primary user’s usual activities was intended to increase the secondary system’s throughput and the number of users that the secondary base station can serve. The firefly algorithm incorporates the chaos algorithm to increase convergence speed and decrease the likelihood of local optimization. The algorithm can effectively find the best answer while making the issues easier. The algorithm doesn’t focus on the problems related to real-time applications and it was not sensible for the response time.
James Adu Ansere et al. [23] have developed an energy-efficient iterative algorithm using the convex approximation method and Lagrangian dual decomposition technique for optimal resource allocation. A Jointly optimized power allocation, the count of active base stations, and a user selection algorithm were utilized to improvise the energy efficiency in the networks of IoT. The proposed algorithm initiates the base station count and provides better Quality of Service (QoS) in user equipment present in the IoT. The convex approximation method and Lagrangian dual decomposition technique used in the algorithm provide assured convergence with minimal computational complexity. However, the delay time considerably get increased when the user equipment gets increased.
3. OVERVIEW OF IRSA
The issue raised in resource allocation must be defined before describing the proposed algorithm. There are two types of nodes in the IoT network considered in this research, the first one is resources and the second is gateways connected with the networks of IoT. The various parts in the IoT network are connected by gateways and these gateways are responsible to regulate the traffic in resources. Moreover, these resources can be connected with various gateways, and communication cost among them is scheduled. The cost computation is an essential process to be carried out among the gateways and when the computational cost seems to be higher, it leads to connection issues among the gateways. The communication cost gets varied by changing the communication model. The load balancing is the process where the resources get separated among the gateways. Thus, this research focuses on the cost of communication and load balancing in the resource allocation of IoT networks.
Where the total number of the gateway is represented and the cost for transferring the data among the 𝑗th gateway and other resources is denoted as 𝑑𝑗 𝑟. The cost of communication in a gateway has an exponential effect on the cost of communication, so 𝑑𝑗 𝑟 × 𝑑 𝑔 is considered a better equation while computing the maximum cost. The multiplication of is effective while computing the cost involved in communication. The communication cost among the gateway sources can be computed using equation (2) as follows:
The cost involved in communication among the gateways 𝑖 and 𝑗 is denoted as 𝑙𝑖𝑗 and 𝑑𝑗 𝑟 is computed by utilizing the equation (3) as follows:
The communication cost among the 𝑗th gateway is denoted as 𝜀𝑗𝑘 and the connected gateway resources are represented as |𝑣𝑔 𝑗|.
Another parameter in resource allocation is load balancing which is denoted a penalty𝑃. The IRSA minimizes the and the function’s denominator is taken which denotes the penalty and denotes the normal state of the gateway. The resource with a gateway higher than the value of is utilized to improve value. The value of the penalty𝑃 is computed using the equation (4) as follows:
Where the total number of the gateway is denoted as |𝑉𝑔| and the penalty 𝑃𝑖 for each gateway is computed using equation (5) as follows:
The total number of a resource based on the gateway is denoted as the total number of resources and the constant value is denoted as and respectively. The illustration of the network system is represented in Figure 1 as follows:
Figure 1. Representation of network system
3.2. Reptile Search Algorithm (RSA)
The RSA algorithm [24] is a type of metaheuristic algorithm developed by Abuligah et al. in the year 2021. RSA imitates how crocodiles might act while hunting in their native environment. In general, crocodiles are members of the “Crocodylinae” family and prefer to live in areas with access to food and water. They come from the class of animals known as amphibians, which can hunt both in and out of water. The following examples show how crocodiles behave in their daily lives. The RSA is based on the natural social behavior and attacking strategy of the crocodiles. The RSA undergoes two phases as exploration and exploitation phase, the exploration phase is based on the mechanism of encirclement,and the exploitation stage is based on hunting behavior. The metaheuristic algorithm is implemented with the candidate solution before beginning the iterations. The candidate solutions can be created based on equation (6) mentioned as follows:
Where the stochastic value is denoted as,the maximal and minimal limits of the problems in optimization are denoted as.
The distinctive feature of RSA’s worldwide search is encircling behavior. Two behaviors such as aerial and abdominal walks make up the process. Crocodiles are frequently prevented from approaching food by these two acts. The crocodiles perform a search at a global level to get food after numerous tries. Make sure that the meantime of this development stage is adjusted continuously to obtain better results. The crocodile’s encircling behavior is represented using equation (7) as follows:
Where the best position of the crocodile at iteration is denoted as and the stochastic value from 0 to 1 is denoted as 𝑟. The maximum number of iterations is represented as is crocodile’s dimension at the state 𝑟1and the stochastic value between 0 and 1 is denoted as. The operator of the crocodile 𝑖 in dimension 𝑗 denoted as 𝜂𝑖,𝑗 and it is evaluated using equation (8) as follows:
Where 𝑃𝑖,𝑗 is represented as the percent of the variance between the best position and the current state of the crocodile. The reduced function 𝑅𝑖,𝑗 is utilized to lower the explored region is computed using the equation (9) which is represented below,
Where the random value among 1 and 𝑁 is represented as 𝑟2 and the smaller value is denoted as 𝜀. The reducing probability of the arbitrary value is denoted as 𝐸𝑆 which lies in the ratio of 2 and – 2, it is represented in equation (10) as follows:
The integer value lies between -1 to 1 is denoted as 𝑟3. The best crocodile’s position 𝑃𝑖,𝑗 is reorganized using equation (11) as follows:
Where the maximal and minimal limits of 𝑗th dimension are denoted as 𝑢𝑝𝑗 and 𝑙𝑜𝑤𝑗 , the parameter utilized to regulate the accuracy during the search process is denoted as
The crocodile’s average position is denoted as 𝑀(𝑍𝑖)which is represented in equation (12) as follows:
The hunting process is based on two techniques such as coordination and collaboration. The encirclement system has almost locked down the location of the intended prey for the crocodiles, who may now approach the target more easily thanks to their hunting tactics. After multiple rounds, the development phase will frequently discover the nearly ideal candidate solution. The mathematical representation of the developed hunting behavior of the crocodile is represented in equation (13) as follows:
Where the crocodile’s optimal position is defined as an operator for crocodile at 𝑗th dimension is denoted as 𝜂𝑖,𝑗.
3.3. Improved Reptile Search Algorithm (IRSA)
Less latency and energy usage are two fundamental network components for IoT administration. Therefore, this study has concentrated on the RA problem in IoT to attain these goals. As was previously mentioned, the key goals of RA are load balancing and lowering communication costs. Less communication cost results in lower network latency. By load balancing, blockages from the network are neglected and increase the performance of the network. If these limitations are managed, there will be more opportunities for using this technology. This paper proposed a heuristic technique known as IRSA to tackle the issues in RA in IoT networks. The leap out and the enhancement of precision of the candidate solution are improved using the Levy flight method and the technique based on interaction crossover improvises the ability of IRSA.
3.3.1. Levy Flight Method
The following properties of the random numbers produced by the Levy flight method are employed in this paper:
(1) The generated random numbers are frequently small, with larger ones irregularly combined.
(2) The probability density function of the steps has broad tails. With the help of this random number, oscillations may be induced, the area can be quickly searched within one iteration, and a candidate solution can be helped to emerge from the local optimum.
The levy distribution function is represented in equation (14) as follows:
The length of a step in levy flight is computed using equation (15),
Where the Gaussian distribution function is represented as, the value of 𝑢 and 𝑣 is represented in equation (16) as follows:
Where the value of 𝜎𝑢𝑎𝑛𝑑𝜎𝑉 is represented in equations (17) and (18) respectively
Where the gamma function is represented as ϕ and the parameter is denoted as β with fixed 1.5
The encircling mechanism involves high walk and belly walk which takes place using the Levy flight method is used to efficiently increase the search area. To maximize the tractability of the ideal phase of exploitation, the Levy flying approach is used for phases of coordination and collaboration in crocodile behavior for hunting. The method of encircling is based on levy flight and is represented in equation (19) as follows:
Where 𝜆 is the parameter with a value of 0.1
The hunting of the crocodile based on coordination and cooperation using the levy flight method is represented in equation (20):
3.3.2. Interaction crossover method
The information is interchanged among two candidate solutions and the candidate is in an ideal position, the interaction crossover technique aids the candidate in their current position in making adjustments. To enhance the search ability of the candidate solutions, the new position gathers data on the ideal solution and other potential alternatives. The parameter utilized to control the crocodile’s activity for the number of iterations is defined as 𝐶𝐹 which is represented in equation (21) as follows:
Where the current iteration is represented as and the maximum number of iterations is defined as. The crocodile population is classified into two categories as. The upgraded state of the crocodile is represented in equations (22) and (23) as follows:
Where the best position of the crocodile is represented as and the stochastic values lie in the interval 0 to 1 denoted as and. The crocodile lies in the position and is denoted as respectively. After the process of crossover, the crocodiles with poor capabilities are neglected based on the equation (24) represented as follows:
4. RESULTS AND ANALYSIS
This section provides the results and analysis of this research. The result portion is classified into performance analysis and comparative analysis which are represented in the following sections. The simulation of the proposed IRSA is implemented with four gateways and seven resources, the test data is created based on three sizes of the data such as small, medium, and large. Moreover, the total count of gateway gets varied from 4 to 100 and the a total number of resources varies from 100 to 800. The proposed method is designed and implemented for total of eight test samples. Moreover, the proposed method is implemented in MATLAB software with system specifications such as i7 processor at 2.24 GHz and 8GB Random Access Memory (RAM) in Windows 10 operating system.
4.1. Performance Analysis
In this research, the optimization problem is rectified using the IRS optimization algorithm. IRSA is an advancement of RSA where the levy and cross-over methodology is utilized. Here, the performance of IRSA optimization with existing optimization algorithms such as Particle Swarm Optimization (PSO), Ant Colony Optimization (ACO), Fruit fly Optimization algorithm (FOA), RSA, and IRSA are evaluated based on parameters like allocation rate, average delay and consumption of energy. Table 1 represented below provides the performance of various optimization algorithms with the proposed IRSA algorithm.
4.1.1. Allocation rate
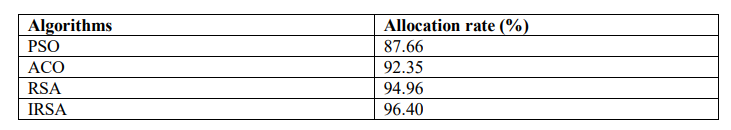
Resource allocation is defined as the rate of assigning resources to the network to minimize latency and power. The allocation rate of PSO, ACO, RSA, and IRSA is 87.66%, 92.35%, 94.96%, and 96.40% respectively. The results from the simulation show that IRSA achieved a maximum allocation rate of 96.40% when compared with existing algorithms. Table 1 shows the allocation rate of the proposed IRSA with the existing algorithms.
Table 1. Performance based on the allocation of resources
The graphical representation of allocation rate of optimization algorithm is represented in figure 2 as follows:
Figure 2. Allocation rate
From Table 1 and Figure 2, it is concluded that the proposed IRSA achieved a better allocation rate of 96.40% which is comparatively higher than the existing algorithms.
4.1.2. Average delay
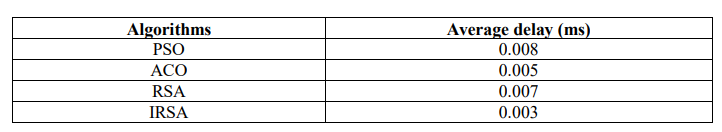
The delay time is represented as the time between the change of component measured at the source point and the destination point of the system. The average delay of PSO, ACO, RSA, and IRSA is 0.008 ms, 0.005 ms, 0,007 ms, and 0.003 ms respectively. Table 2 shows the average delay of the proposed IRSA with existing algorithms.
Table 2. Performance based on average delay
The graphical representation of average delay of optimization algorithm is represented in figure 3 as follows:
Figure 3. Average delay
From Table 2 and Figure 3, it is concluded that the proposed IRSA achieved a minimum delay of 0.003 ms which is comparatively higher than the existing algorithms.
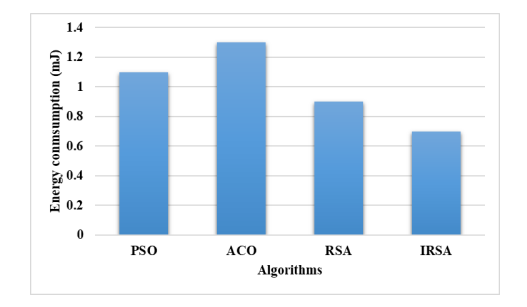
4.1.3. Energy consumption
The consumption of energy in the network is defined as the quantity of consumed energy during the time of receiving and broadcasting packets that contain data. The energy consumption of PSO, ACO, RSA, and IRSA is 1.1 mJ, 1.3 mJ, 0.9 mJ, and 0.7 mJ respectively. From Table 3 and Figure 4, it is concluded that the proposed IRSA consumed minimal energy of 0.7 ms which is comparatively higher than the existing algorithms
Table 3. Performance based on energy consumption
The graphical representation of energy consumption is represented in figure 4:
Figure 4. Energy consumption
From table 1 – table 3, it is shown that the performance of the IRS optimization algorithm is better when compared with other optimization algorithms. This better performance is due to rectifying IoT Resource Allocation Problem (IRAP) effectively using levy and crossover methodology. In the Levy method, a random number will be assisted in updating the state to induce oscillations, perform a quick search in one iteration, and assist in the candidate solution leap out of local optimum and cross – over method to enhance the searchability of the candidate solutions, the new position gathers data on the ideal solution and other potential alternatives. IRSA achieved a better allocation of 96.40 % which is higher than other optimization algorithms.
4.2. Scalability Analysis
The scalability of the simulation depends on the number of iterations and fitness value. In this section, the scalability of the proposed method is sensed based on varying the iteration from 100 to 1000. The figure 5 presents the scalability of the proposed IRSA in an IoT network by varying the number of iteration
Figure 5. Graphical representation for evaluation of fitness
The results from Figure 5 show that the proposed IRSA obtained better fitness value when compared with existing techniques. The better result of the proposed method is due to the levy flight cross – over technique involved in IRSA. The Levy flight outperforms quick search in a single iteration which helps to minimize the cost and the cross – over method improvises the ability to search the ideal position for effective allocation of resources. Figure 6 mentioned below shows the efficiency of the proposed IRSA based on scaling the allocation rate and energy consumption. Moreover, the scalability of the proposed method is compared with the existing optimization techniques. At the time of evaluating the scalability, the proposed IRSA has a higher allocation rate of 96.40% and the energy consumption is 0.7 Mj. This better result is due to incorporating the Levy flight and crossover method in IRSA which provides stability and robustness to the algorithm. The Levy flight method enhances the convergence in a single iteration and the cross – over search ability for an effective allocation of resources.
Figure 6. Graphical representation for evaluating the scalability by means of energy consumption and allocation rate
Table 4. Comparative table
From the above comparative table 2, it is shown that the proposed IRSA achieved better performance measures when compared with the existing SRAF [21] and ICFA [22] for optimizing the problems of resource allocation in the networks of IoT. IRSA utilized Levy and cross-over method which updates the position and enhances the search speed in a single iteration. Thus, IRSA performs to rectify the issues in IoT resource allocation.
5. CONCLUSION
The problems related to resource allocation are a challenging task in the environment of IoT. Resource allocation is a process of allocating an optimum resource to the tasks. The inappropriate utilization of resources leads to the consumption of energy and affects the IoT environment. So, resource allocation in a large network system like IoT is an important topic. In this research, the IRSA algorithm is proposed to minimize energy consumption and reduce latency in the network IoT. As the name indicates, IRSA is an advancement in the RSA where Levy and crossover methodologies are utilized. In the Levy method, the random number will be assisted in updating position to induce oscillations, make a quick search in the area during one iteration, and assist in the candidate solution leap out of the local optimum, and the cross-over method enhances the searchability of the candidate solutions, the new position gathers data on the ideal solution and other potential alternatives. Thus, the IRSA is utilized in solving the optimization problem. Experimental research shows that the proposed IRSA attained a better allocation rate of 96.40% which is comparatively higher than SRAF (92.40 %) and ICFA (91.67 %). In the future, hybridization can be implemented in optimization techniques to improve the performance of resource allocation.
CONFLICT OF INTEREST
The authors declare no conflict of interest
REFERENCES
[1] Mukherjee, Amrit, Pratik Goswami, Ziwei Yan, Lixia Yang & Joel JPC Rodrigues, (2019) “ADAI and adaptive PSO-based resource allocation for wireless sensor networks”, IEEE Access, Vol. 7, pp131163-131171.
[2] Ren, Hong, Cunhua Pan, Yansha Deng, Maged Elkashlan & Arumugam Nallanathan, (2020) “Resource allocation for secure URLLC in mission-critical IoT scenarios”, IEEE Transactions on Communications, Vol. 68, No. 9, pp5793-5807.
[3] Li, Yun, Shichao Xia, Qianying Yang, Guoyin Wang & Weiyi Zhang, (2020) “Lifetime-prioritydriven resource allocation for WNV-based internet of things”, IEEE Internet of Things Journal, Vol. 8, No. 6, pp4514-4525.
[4] Kota, P.N., Chandak, A.S., Patil, B.P. (2023) “ IOT-HML: A hybrid machine learning technique for IoT enabled industrial monitoring and control system” , Concurrency and Computation: Practice and Experiencet,Vol 35, No. 3, pp 1-21
[5] Sun, Huaiying, Huiqun Yu, Guisheng Fan & Liqiong Chen, (2020) “Energy and time efficient task offloading and resource allocation on the generic IoT-fog-cloud architecture”, Peer-to-Peer Networking and Applications, Vol. 13, No. 2, pp548-563.
[6] Raveendran, Neetu, Huaqing Zhang, Lingyang Song, Li-Chun Wang, Choong Seon Hong & Zhu Han, (2022) “Pricing and resource allocation optimization for IoT fog computing and NFV: An EPEC and matching based perspective”, IEEE Transactions on Mobile Computing, Vol. 21, No. 4, pp1349-
1361.
[7] Hu, Han, Qun Wang, Rose Qingyang Hu & Hongbo Zhu, (2021) “Mobility-aware offloading and resource allocation in a MEC-enabled IoT network with energy harvesting”, IEEE Internet of Things Journal, Vol. 8, No. 24, pp17541-17556.
[8] Mukherjee, Amrit, Pratik Goswami, Mohammad Ayoub Khan, Li Manman, Lixia Yang & Prashant Pillai, (2021) “Energy-efficient resource allocation strategy in massive IoT for industrial 6G applications”, IEEE Internet of Things Journal, Vol. 8, No. 7, pp5194-5201.
[9] Li, Xi, Yiming Liu, Hong Ji, Heli Zhang & Victor CM Leung, (2019) “Optimizing resources allocation for fog computing-based internet of things networks”, IEEE Access, Vol. 7, pp64907- 64922.
[10] Chen, Jie, Lin Zhang, Ying-Chang Liang, Xin Kang & Rui Zhang, (2019) “Resource allocation for wireless-powered IoT networks with short packet communication”, IEEE Transactions on Wireless Communications, Vol. 18, No. 2, pp1447-1461.
[11] Fu, Yaru, Xiaolong Yang, Peng Yang, Angus KY Wong, Zheng Shi, Hong Wang & Tony QS Quek, (2021) “Energy-efficient offloading and resource allocation for mobile edge computing enabled mission-critical Internet-of-Things systems”, EURASIP Journal on Wireless Communications and Networking, Vol. 2021, No. 1, p26.
[12] Wang, Jun, Daquan Feng, Shengli Zhang, An Liu & Xiang-Gen Xia, (2021) “Joint computation offloading and resource allocation for MEC-enabled IoT systems with imperfect CSI”, IEEE Interne of Things Journal, Vol. 8, No. 5, pp3462-3475. [13] Jain, Deepak Kumar, Sumarga Kumar Sah Tyagi, Subramani Neelakandan, Mohan Prakash & Lakshmaiya Natrayan, (2022) “Metaheuristic optimization-based resource allocation technique for cyber twin-driven 6G on IoE environment”, IEEE Transactions on Industrial Informatics, Vol. 18, No. 7, pp4884-4892.
[14] Hussain, Fatima, Rasheed Hussain, Alagan Anpalagan & Abderrahim Benslimane, (2020) “A new block-based reinforcement learning approach for distributed resource allocation in clustered IoT networks”, IEEE Transactions on Vehicular Technology, Vol. 69, No. 3, pp2891-2904.
[15] Tsai, Chun-Wei, (2018) “SEIRA: An effective algorithm for IoT resource allocation problem”, Computer Communications, Vol. 119, pp156-166.
[16] Tyagi, Sumarga Kumar Sah, Amrit Mukherjee, Shiva Raj Pokhrel & Kamal Kant Hiran, (2021) “An intelligent and optimal resource allocation approach in sensor networks for smart agri-IoT”, IEEE Sensors Journal, Vol. 21, No. 16, pp17439-17446.
[17] Kota, P.N., Gaikwad, A.N. (2017) “ Fireflies algorithm based optimal scrambling to reduce PAPR in SFBC based MIMO-OFDM”, International Journal on Communications Antenna and Propagation, Vol. 7, No. 7, pp. 626–634.
[18] Reginald Jude Sixtus J and Tamilarasi Muthu (2022) “Particle Swarm Optimization–Long ShortTermMemory based Channel Estimation with Hybrid Beam Forming PowerTransfer in WSN-IoT Applications”, International Journal of Computer Networks & Communications, Vol. 14, No.5, pp 65-79
[19] Jiao, Jian, Yunyu Sun, Shaohua Wu, Ye Wang, and Qinyu Zhang, (2020) “Network utility maximization resource allocation for NOMA in satellite-based Internet of Things”, IEEE Internet of Things Journal, Vol. 7, No. 4, pp3230-3242.
[20] Liu, Xiaolan, Zhijin Qin, Yue Gao & Julie A. McCann, (2019) “Resource allocation in wireless powered IoT networks”, IEEE Internet of Things Journal, Vol. 6, No. 3, pp4935-4945.
[21] Al-Makhadmeh, Zafer & Amr Tolba, (2021) “SRAF: Scalable Resource Allocation Framework using machine learning in user-centric internet of things”, Peer-to-Peer Networking and Applications, Vol. 14, No. 4, pp2340-2350.
[22] Wang, Zhiyong, Dong Liu & Alireza Jolfaei, (2020) “Resource allocation solution for sensor networks using improved chaotic firefly algorithm in IoT environment”, Computer Communications, Vol. 156, pp91-100.
[23] Ansere, James Adu, Guangjie Han, Li Liu, Yan Peng & Mohsin Kamal, (2020) “Optimal resource allocation in energy-efficient Internet-of-Things networks with imperfect CSI”, IEEE Internet of Things Journal, Vol. 7, No. 6, pp5401-5411.
[24] Abualigah, Laith, Mohamed Abd Elaziz, Putra Sumari, Zong Woo Geem & Amir H Gandomi, (2022) “Reptile search algorithm (rsa): a nature-inspired metaheuristic optimizer”, Expert Systems with Applications, Vol. 191, p116158.
AUTHORS
Prabhakar Kota received a Ph.D. degree in Electronics and Telecommunication Engineering from SPPU University, Pune in 2018. He is now an Associate Professor at MES College of Engineering, Pune, India. His research interests include signal processing and wireless Communication systems.
Pravin B Chopade is currently working as an Associate Professor of E&Tc at M. E. S. College of Engineering, Pune-01.He holds BE in Electronics, ME in Electronics ,andPh.D. in Electronics and Telecommunications Engineering and has more than 20 plus publications in reputed national and international journals. He has published a patent based on the superresolution of images using a hardware platform. His research papers have been widely cited, in technical papers and reference books He is a member of IETE and ISTE. His area of interest is image processing and signal processing.
Bhagavat D. Jadhav received the B.E. degree in Electronics engineering from Pune University, Pune India, in 2002, M.Tech. and Ph.D. degrees from Savitribai Phule Pune University, India, in 2008 and 2017 respectively in Electronics and Telecommunication Engineering. Since July 2005, he has been with the Department of Electronics and Telecommunication Engineering and currently he is working as Professor and Dean Controller of Examinations. His current research interests include Signal and Image processing. He is a Life Member of the Indian Society for Technical Education (ISTE). He has filed two patents and published more than twenty papers in various IEEE, Elsevier, Springer conferences and reputed journals.
Prof. Dr.Pravin Marotrao Ghate is a graduate in Electronics & Telecommunication Engineering with a post-graduate degree of Electronics Engineering. For his doctorate, He did research in the area of Speech Processing with the design and development of Speech synthesis Methods for improving the quality of syllables in Marathi Language. Prof. Dr.Pravin Ghate is a Professor at JSPM’s Rajarshi Shahu College of Engineering, Tathwade, Pune ,and a Professor at the Department of E & Tc Engineering. He has 17 technical published papers in National & International Journals and Conferences. His research papers have been widely cited, in technical papers and reference books. He is guiding 2 Doctoral students and 15 postgraduate students and is credited with the establishment of a Project laboratory (Electronics ). He had worked on two major projects sponsored by Matrix Automation and SPPU. His research has led to 02 patents being registered to his credit. He is actively associated with various prestigious Education/Research organizations like Dr. Babasaheb Marathwada Ambedkar University Aurangabad as an External examiner and Matrix Automation in Pune for R&D activities & member of the Purchase Committee. He is also a Member of the Indian Society of Technical Education & Society of Automotive Engineers.
Shankar Dattatray Chavan completed his Ph.D. in Electronics & Telecommunication Engineering from Savitribai Phule Pune University, Pune, and his Master of Engineering in the Electronics from Shivaji University Kolhapur in 2007. Currently working as Associate Professor of Electronics and Telecommunication Engineering Department at Dr. D. Y. Patil Institute of Technology, Pimpri, Pune, with an overall teaching experience of over 23 years at Undergraduate and Postgraduate level and Industrial experience of 5 years. Guided more than 12 students towards post – graduation and currently guiding 02 research scholars toward Ph.D. More than 34 papers published in international conferences and reputed journals. Area of interest includes Wireless Sensor Networks and Power Electronics