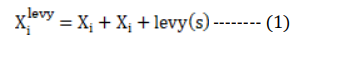IJCNC 08
ENHANCING CYBER DEFENSE AGAINST ZERO-DAY ATTACKS USING ENSEMBLE NEURAL NETWORKS
Swathy Akshaya and Padmavathi
Department of Computer Science, Avinashilingam University, Coimbatore, India
ABSTRACT
Zero-Day Attacks (ZDAs) are a significant concern for cybersecurity as they take advantage of previously unknown vulnerabilities in software systems. This lack of prior knowledge makes ZDAs extremely difficult to detect as they operate in stealth mode, often evolving as new ideas and approaches emerge in the cybersecurity landscape. Herein, we introduce a hybrid deep learning framework comprising four models, including Artificial Neural Network – Auto Encoder (ANN-AE), ResNet50, CNN-LSTM, and Modified BiLSTM with Game Theory (GT), to improve the prediction and detection of ZDAs. Each model is used in a particular manner: ANN-AE for feature compression and anomaly detection, ResNet50 for feature extraction, CNN-LSTM for capturing spatio-temporal patterns, and Bi-LSTM with GT for modelling attacker-defender interactions. To enhance accuracy and model reliability, we applied the Optimised Levy Flight-based Optimisation Algorithm (OLFOA) in hyperparameter optimisation. We empirically evaluated the proposed approach on two publicly available benchmark datasets, achieving favourable results, specifically high detection accuracy, low false alarm rates, and low computational cost. Our results substantiate the proposed approach to facilitate real-time ZDA prediction and detection and denote the potential for future application in cybersecurity.
KEYWORDS
Zero-Day Attack Prediction, Hybrid Game Theory, Transfer Learning, ResNet50, ANN-AE, CNN-LSTM, Bi-LSTM, Ensemble Neural Networks, OLFOA.
1. INTRODUCTION
In the ever-changing field of cybersecurity, there is a threat called a Zero-Day Attack (ZDA). A ZDA takes advantage of vulnerabilities that hardware or software manufacturers didn’t even know existed. The creation of ZDA attacks is particularly critical as they occur before the initial manufacturing patch is released or before an actual signature detection (or Deep Learning (DL)) has any hope of responding [1]. ZDAs become more prevalent and sophisticated, demanding an urgent need for intelligent, adaptive, and innovative detection methods to anticipate ZDA attacks in real-time [2-4]. To address this issue, this research proposes a new deep learning-based ensemble detection framework for predicting ZDAs. The proposed framework consists of four different complementary DL models, where each model has a specific function in detecting ZDAs: The Artificial Neural Net Auto Encoder (ANN-AE) serves as the unsupervised anomaly detection model to compress the feature space, the ResNet50 model performs hierarchical deep feature extraction, the Convolutional Neural Network-Long Short Term Memory (CNN-LSTM) performs the spatio-temporal nature of the attack patterns, and modified Bi-directional LSTM with Game Theory (Bi-LSTM + GT) is used to sequentially predict and model the behavior of the attacker and defenders [5-7]. Multiple models can identify different patterns of behaviour of ZDAs using a raw signal of anomalies, to the more advanced and evolving multi-stage sequences of attacks [8-10]. The
Optimised Levy Flight-Based Optimisation Algorithm (OLFOA) improves the ensemble’s performance. OLFOA is inspired by natural Levy flights’ random and distant movement patterns [11] [12]. This randomness allows for better global exploration and discovering patterns to balance global explorations and local exploitations in the search space [13]. As such, OLFOA can optimise hyperparameters such as learning rates, dropout values, and architecture (network) configurations, improving the accuracy and robustness of the detection model [14] [15]. The algorithm starts with a population of agents with a random initial position. The agents use Levy flight pathways to navigate the solution space [16]. The Levy flight allows for sudden and large value movement improvement in the probability of escaping local optima. As optimisation occurs, the quality/fitness of each solution (i.e., classification accuracy) determined by the detection models is continually assessed. Thus, agents adapt their position based on previous fitness levels. This agent-based structured procedure greatly enhances the model’s ability to detect more subtle and unseen (attack) patterns [17] [18]. While implementing OLFOA, predicting ZDA requires various components. The random search agent population starts the technique by adapting the positions through the achieved performance metrics [19]. The random motion feature of the search procedure enables the agents to discover new solutions by using the Levy flying mechanism for solution space exploration. While improving system specifications and hyperparameters [20] [21], the algorithm upgrades the classifier parameters and position data to achieve maximum effectiveness. Feature selections coupled with cross-validation assessments lead to the maximum performance levels for external assessment. Through this strategy, both search process quality and prediction accuracy during operational use are improved simultaneously. The OLFOA functions as an effective answer to resolve ZDA prediction and mitigation problems. Using FFOA to optimise Levy flight unpredictability results in OLFOA that delivers an affordable and adaptable threat detection method for unknown cyber threats. This enables cybersecurity experts to better imagine upcoming threats through parameter flexibility alongside accurate measurements. Thereby, it is established as an essential complexity attack detection security tool. The significant contributions of this paper are as follows:
- This paper proposes a proactive and multi-faceted approach for the prediction of ZDA. The proposed framework uses an ensemble of deep learning models: ANN-AE, ResNets50, CNN-LSTM, and Modified Bi-LSTM (GT) to model their compressed features, spatial nature, temporal behaviour, and adversary models, respectively.
- The proposed model is optimised using the Optimised Levy Flight-Based Optimisation Algorithm (OLFOA), which tunes the model hyperparameters dynamically to achieve fast convergence and better detection errors, while properly accounting for drifted, evolving ZDA threats.
- The proposed model is evaluated based on accuracy, precision, recall, and F1 score. Its effectiveness in detecting adversarial samples and routing complex ZDA propagation was demonstrated with standard datasets.
- This research recognises the computational cost of ensemble learning and implementation cost and the value generated over time from proactive threat detection postures with actionable results. This paper also recognises paths to future work regarding real-time detections, scalability, and performance in autonomous defence systems and contextual environments.
This work consists of the following sections: Section 2 examines the range of ZDA prediction algorithms reported in several papers. Section 3 includes the preferred model. Section 4 compiles the study findings. Section 5 provides an overview of the results and potential future investigations
2. BACKGROUND STUDY
2.1. Related Works
In response to growing concerns about the IoT security threat landscape, Karimy and Reddy [22] take a new approach by investigating how Federated Learning (FL) and Differential Privacy (DP) can be combined to improve intrusion detection without losing the privacy of user data. FL is a decentralised training method that allows for model creation via multiple edge devices instead of centralised devices, and DP provides usable protection of people’s data while learning. These authors research approach can reduce data exposure risks while addressing more complex cyber threats that threaten the IoT landscape.
Hindy et al. [23] proposed applying DL techniques to detect outliers indicating ZDAs. The purpose was to build an efficient, high-recall Intrusion Detection System (IDS) to detect current and potential future ZDAs while minimizing the system’s impact. Their model’s performance was compared to a baseline established by a One-Class Support Vector Machine (SVM), and their model was superior at recognising previously unseen attacks.
Shruthi and Siddesh [24] presented a trust-based anomaly detection system with a reinforcement learning framework based on Deep Deterministic Policy Gradient (DDPG). The model uses trust metrics and belief networks to assess node behaviour and identify anomalies in dynamic network environments. These authors provided a method for anomaly detection incorporated with realtime detection abilities, especially when the network is decentralised and uncertain.
Sultan et al. [25] built an intrusion detection scheme specifically for MANETs (Mobile Ad-Hoc Networks) with DL-based Artificial Neural Networks (ANNs). The unstructured infrastructure of MANETs makes traditional security ineffective. They used ANNs to identify and categorise malicious activities found through network traffic data. These authors focused on Denial of Service (DoS) attacks, particularly because of their high occurrence rate. Their method can enhance the integrity of the environment of the mobile ad-hoc networks.
By integrating Genetic Algorithm, Fuzzy Logic (GT-Fuzzy-GADS) and Holt-Winters (GTHWDS), De Assis et al. [26] created a set of easily implemented methods in Software-Defined Networking (SDN) systems. The frequency of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks dropped as SDNs were automatically found and identified using a gametheoretically based monitoring system. Like SDN, IP traffic data was gathered to ascertain the system’s effectiveness. Using this data, a Network Anomaly Simulator introduced the aberrant flows into real-world ones to replicate DoS and DDoS attacks.
Pholpol and Sanguankotchakorn [27] proposed a framework based on deep reinforcement learning for predicting traffic congestion in Vehicular Ad-hoc Networks (VANETs). By modelling traffic dynamics as a Markov decision Process (MDP), the framework allows vehicles to make intelligent routing decisions in real-time. In addition, the proposed method can use neural Q-learning to learn optimal vehicle routing policies depending on traffic flow and congestion patterns. The proposed method improved prediction performance and decreased vehicle communication delays in highly dynamic vehicular environments.
Khan et al. [28] developed a game-theoretic-based defence framework to mitigate the Distributed Denial of Service (DDoS) attack in Internet of Things (IoT) operation networks. In their framework, the interaction between attackers and defenders is modelled as a non-cooperative game, allowing the defender to adapt responses based on attack intensity and phase and the state of the network. The framework increases resilience by incorporating trust management, pay-offbased actions, information sharing, and additional mitigations while minimizing false positives. It addresses emergent behaviour in dynamically adapting to attack changes when a resourceconstrained IoT network is attacked.
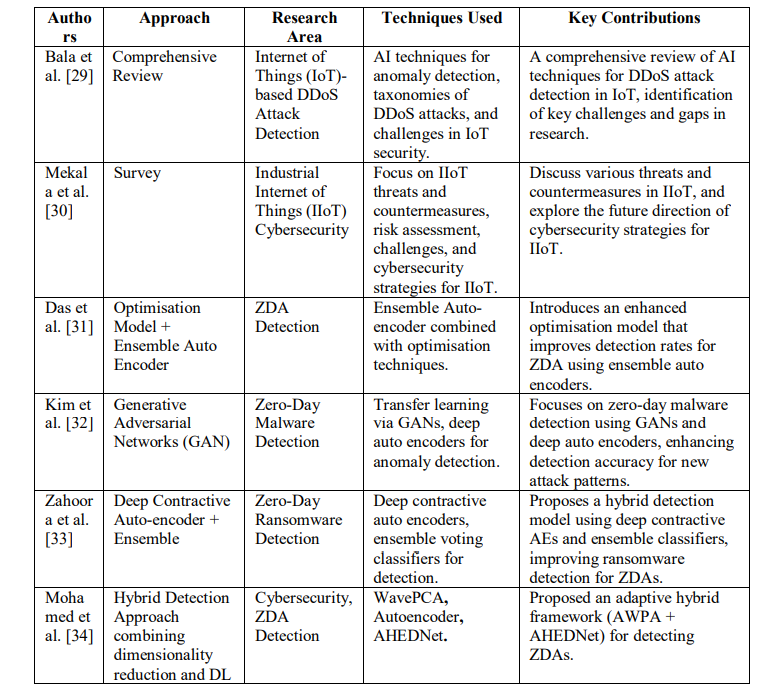
Table 1. Significant Study on Existing Zero-Day Attacks
2.2. Observations of the Existing Work
- Growing Threat of ZDAs: The utility of the previously unknown software flaws entails a significant and escalating risk.
- Existing Technology Limitations: Modern defensive solutions like IDS and firewalls provide limited protection against contemporary threats. Although occasionally beneficial, these strategies are insufficient to counter the complexity of modern threats routinely.
- Problems with Conventional Approaches: Signature-based detection is challenging to follow when the threat features vary rapidly.
- Heuristic algorithms have additional challenges in adapting to dynamic attack strategies.
- Demand for Modern Solutions: To address these concerns appropriately, stronger and more flexible ZDA detection techniques are required.
2.2. Research Gaps and Challenges
- Insufficiently Comprehensive Techniques: Current attempts lack a coordinated and proactive strategy to safeguard against ZDAs appropriately. Zero-day threats are always changing. Hence, a complete strategy is needed.
- Restricted scope of novel strategies: Machine Learning and Game Theory Integration (GTI) are two approaches that focus on certain detection qualities. These approaches do not understand the multiple dimensions involved in an attack terrain.
- Scaling issues: More study is required to ensure the current models are scalable and feasible.
- Developing detection models: Improved detection accuracy and reliability rely on more complex technologies that adapt to various attack scenarios.
- METHODOLOGY
This study presents a hybrid ensemble framework for detecting ZDAs by using the strengths of multiple DL based models to develop better accuracy and generalizability for Zero-Day detection. The architecture consists of an element for unsupervised anomaly detection and dimensionality reduction, an ANN-AE, ResNet50 for deep-level hierarchical feature extraction and a CNN-LSTM model for accurately modelling the spatio-temporal dynamics of network attacks. Another part of the architecture is a modified Bi-LSTM model integrated with GT, intending to predict the next sequence of steps based on the strategic interaction between the network Defenders versus Attackers. An impressive advantage is combining components for the precision of the architecture to improve the accuracy, minimise false positives, and successfully defend against ZDAs.
3.1. Dataset Description
Dataset 1 (D1): Zero-Day Path dataset
The PATH dataset is used in ZDA research, it is a cloud simulation dataset that validates anomaly detection and intrusion detection in realistic attack scenarios. PATH emulates the behavior of a real cloud infrastructure with a variety of services, user interactions, and attack vectors, especially zero-day exploits.
Dataset 2 (D2): Zero-Day Attack Dataset (celosia)
Source: https://www.kaggle.com/code/mkashifn/celosia-zero-day-attack-detection-demo The Celosia Zero-Day Attack dataset is based on IoT Network Traffic sources and is designed to facilitate ZDA prediction and detection research. The dataset consists of time-series CSV files containing features such as packet size, duration, and flow counts. Each row of data is labeled normal or attack for supervised learning. The dataset was designed to assess anomaly detection and ML models. The dataset focuses on actual zero-day threats derived from cloud environments.
- Pre-processing: Both datasets engage in general preprocessing, including missing value imputation, normalising, and feature subset selection to aid dimensionality reduction and model performance. They both share some techniques, such as min-max scaling, andspecific to dataset 1, the collection of noise and reduction of the noise through the ANNAE model.
- Public Accessibility: Dataset 1 is a synthetic dataset designed for this study’s specific purpose. It is available through requests if researchers wish to use it and aid in reproducibility. Dataset 2 is available publicly in Kagle repository.
3.2. Data Preprocessing and Feature Engineering
Through preprocessing, raw network traffic data underwent extensive preprocessing before it could be used to improve model performance and dimensionality. All incomplete or corrupted entries were deleted at the beginning. Then, feature selection was done using correlation-based preparation analysis and knowledge of the domain to keep the most discriminative attributes and reduce the initial high-dimensional feature set. An unsupervised Autoencoder (ANN-AE) was used to achieve even more dimensionality reduction of the feature space by compressing the existing features to the latent representation while only retaining the noise that filtered through. Each feature was scaled to fit between the 0 and 1 range using the Min-Max scaling method to enable model stability. Since class imbalance is normally present in zero-day attack data sets, the Synthetic Minority Over-sampling Technique (SMOTE) overlays anonymous attack data to balance attack samples with benign samples. Finally, we created the splits of our data sets into 70 % training, 15% validation, and 15% testing data sets using stratified sampling to preserve the class proportions.
3.3. The Proposed Framework
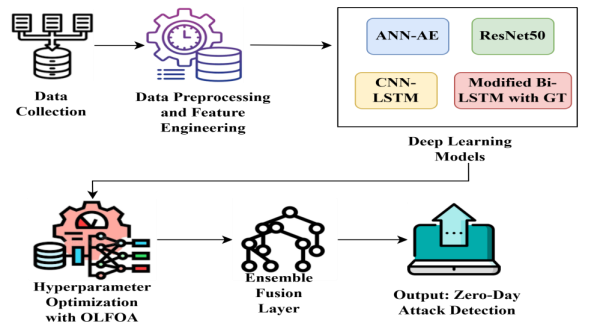
In this proposed research, data is first collected. Then the data goes through a preprocessing and feature engineering module that aims to clean, normalise, and extract the necessary features. This clean data is passed on to the deep learning module. The deep learning module is composed of four models: ANN-AE for feature compression and anomaly detection, ResNet50 for deep feature extraction, CNN-LSTM for learning the spatio-temporal attack patterns, and, lastly, a Modified Bi-LSTM with GT for strategic sequence modelling. Model performance is generated via hyperparameter optimisation that uses OLFOA. Mode ensemble is achieved in the ensemble fusion layer, which combines all outputs to enable maximum prediction power. The system then produces the output, ZDA detection. Fig. 1 shows the overall structure for ZDA detection
Figure 1Figure 1. Framework of the Proposed Zero-Day Attack
3.4. Hybrid Ensemble Architecture
The architecture is implemented in sequential modules, with each component contributing to a specific stage of the ZDA detection process:
3.4.1. The Artificial Neural Network–Autoencoder – Anomaly Detection & Feature Compression
The Artificial Neural Network – Autoencoder (ANN-AE) is an essential part of the proposed hybrid detection architecture for ZDA classification, as it serves as unsupervised anomaly detection and provides feature compression for managing noisy system logs, high-dimensional data, and class imbalance. The ANN-AE reduces the dimensionality of the input by encoding the input into a lower, latent space, reconstructing an output, and minimising the reconstruction loss. By doing this, the ANN-AE denoises and derives exclusionary information on anomalies without any labelled data. The ANN-AE compressed representation of normal activities enhances the performance of downstream models such as ResNet50 and CNN-LSTM. Therefore, it allows the ensemble to detect anomalies more effectively, reducing false positives and promoting better generalisation of unseen attacks.
3.4.2. ResNet50- Deep Hierarchical Feature Extraction
In the proposed framework for ZDA detection, ResNet50 is used for deep hierarchical feature extraction of the compressed and denoised embeddings from the ANN-AE by Akshaya and Padmavathi [35]. ResNet50 is a 50-layer deep residual neural network, and the residual architecture can accommodate the abstract representations often critical for identifying stealthy or subtle attack behaviours, especially when dealing with high-dimensional, imbalanced data. By implementing residual learning, with identity skip connections, ResNet50 ensures gradient flow to prevent distress-vector problems (vanishing gradients), enabling the model to learn strong deep representations. This is a key step for recognising non-linear attack signatures and supporting generalisation to ZDA variants.
Transfer Learning (TL) is incorporated by utilizing the lower convolutional layers of the ResNet50 model pre-trained on the ImageNet dataset. The first layers representing generalpurpose features are kept as frozen weights, while the last layers are trained on traffic data from the domain. Using TL accelerates the convergence of the model and reduces overfitting, which allows it to better adapt to the zero-day domain, especially with limited labelled samples of attacks. TL allowed the network to use previously learned visual representations while customising its cybersecurity application decision space. In addition, its outputs provide a rich, high-level feature space for fusion with sequential models such as CNN-LSTM and Bi-LSTM with GT, further enhancing the framework’s ability to detect complex lifeforms that represent evolving and evasive cyber-attacks.
3.4.3. Convolutional Neural Network-LSTM – Spatio-Temporal Attack Pattern Modeling
Whereas LSTM extracts the temporal information, CNN extracts the spatial data. The model starts with a CNN, which extracts high-level characteristics from large volumes. The CNNLSTM hybrid model is an important element of the ZDA detection architecture since it can take full advantage of the spatial correlations and temporal correlations associated with the cyberattack behavior. In this case, the CNN will draw out localized features from the input, such as packet-level fingerprinting or clusters of system events. At the same time, the LSTM units will take advantage of the temporal relationships of these features to model or encapsulate the sequential flow of the attack. The hybridisation approach is simple, and has a massive potential for grasping morphed attack sequences and detecting progressive multi-staged intrusion events (i.e. reconnaissance → exploitation → exfiltration) since the CNN-LSTM model will be able to characterise the malicious patterns concerning time and the layers of the networks involved. The combination of CNN-LSTM is also very important to capture the essence of dynamic time-series data, and for this study, either through network logs or through CloudSim-generated network paths with time-stamped user events that acted as indicators of attacks. The results for this study correspond with those found in earlier research Swathy Akshaya and Padmavathi [37]. The CNN-LSTM-based detection will lead to higher degrees of accuracy and fewer false positives through the benefits of context. Further, this hybrid architecture also makes a system aware of both the structural elements of attacks and the evolution of the attacks in time, thus providing the rationale for the importance of the CNN-LSTM model for temporal ZDA analysis.
3.4.4. Game Theory Integration with Intrusion Tolerance Concepts
Intrusion Tolerance Systems (ITS) are systems designed to maintain system integrity and availability during attacks by enforcing recovery and adaptive defences. The goal of recognising and modelling ITS within a game theory (GT) framework is to enable the examination of the interaction of an intelligent attacker and a resilient defender. The defender’s options encompass several strategies to enhance resilience, including fault tolerance and adaptive response, while the attacker tries to maximise the effect of the attack or evade detection. Payoff functions can evaluate the trade-offs necessary between security and availability, and the cost and resource expenditures of the defender, and allow derivation of optimal defender strategies (e.g., Nash or Stackelberg Equilibria). Integrating ITS with GT provides a strong theoretical basis for designing robust cyber-defence systems.
3.4.5. Modified Bi-LSTM + Game Theory – Strategic Sequence Modeling
Bi-Long Short Term Memory: Recurrent Neural Networks (RNN) process sequential data; however, they only use weakly supervised representations because of the difficulties with longterm dependencies caused by vanishing gradient or exploding gradient problems or errors. Longshort-term memory (LSTM) networks solve this issue by allowing more selective information storage over time. Moreover, LSTMs can be improved and are generally more effective as Bidirectional LSTMs, which are created by combining two LSTMs. These allow the model to learn input sequences in forward and reverse directions, improving accuracy and overall longterm learning.
Game Theory: Unlike computer smart networks, WSNs lack several resource limitations, including power, memory and processing speed. It is attacked from several angles, including Sybil, Hello Flood, Black Hole, Grey Hole and Zero Day. The sleep attack gives WSNs using cluster-based routing a new security mechanism. It models epidemiologically using an internal attack detection technique. Most of these models overlook the link between the four IDs and the attackers. While the IDS is operating, malicious actors try to access the nodes of the sensor network. Regarding the design of the game, the polar opposite is true. A game-theoretic model is presented for attacking-defense simulation and an attacker-IDS equilibrium solution to solve energy consumption and detection efficiency concerns.
The last stage of the framework uses a Modified Bi-LSTM combined with a Game Theory (GT) layer that considers both forward and backwards dependencies in the events elicited from the timeline, all while modelling the strategic interaction of the attackers and defenders. The BiLSTM operates on either side of an input sequence, allowing for the learning of longer-term dependencies. Also, the contextual relationships in network log files. At the same time, game theory simulates rational decision making by measuring the utility of an attacker and a defender so that an attacker will attempt to maximize their utility and the defender will attempts to minimize their losses. This permits the integrated Bi-LSTM and GT to predict and logically counteract proposed sophisticated ZDAs with planned, misleading deception by allowing the defenders to model these attacks proactively. According to Akshaya and Padmavathi [36], the reasoning weaves together across a complex tapestry that extends beyond detection provided by the adapted Bi-LSTM because modeling the malicious behavior of adversaries facilitates improved reactions to swiftly changing conditions or new threats
3.5. Comparative Analysis of ZDA Prediction using Optimization
This study investigates the role of deep learning in the detection of ZDAs and how optimization has the potential to improve the detector’s accuracy by reducing false positives. We have proposed the Optimized Levy Flight-based Optimization Algorithm (OLFOA) based on animals’ foraging behavior, which is an optimal way of exploiting resources, to optimize model parameters and feature selection. OLFOA significantly increased detection accuracy and latency, making it a robust defence against the ever-evolving threats of ZDAs.
3.5.1. Optimized Levy Flight-based Optimization Algorithm (OLFOA)
Levy’s flying style is unpredictable. This feature aids the algorithm in detecting the world by preventing the whole population from slipping towards the local optimum. The following rule indicates a moving posture
The search agent’s obligations shift after the update. The Levy flight-based update states the i-th particle’s or agent’s updated position . A parameter or factor that influences the behavior of the Levy distribution used for updating the position is s. This technical work introduces the evolutionary ZDA prediction, which uses the OLFOA mechanism and the result of the ZDA prediction. The OLFOA model assists in the adaptive decisions of the two primary hyperparameters for ZDA prediction. The offered framework mainly consists of the internal parameter adjustment and the external examination of classification performance. The fitness function is the correctness of the classification. A classifier’s average accuracy in predicting ZDA is denoted by the acronym ACCi.
The adaptive decision-making process for ZDA prediction continually changes two major hyperparameters: population size and inertia weight. Thus, the proposed OLFOA approach is rather crucial. All of these components aid the algorithm in managing the exploration against exploitation trade-offs during optimization and handling ZDA-specific attack patterns. Furthermore, OLFOA is designed to maximize the fitness function, namely, the classification accuracy of ZDA prediction. The evaluation of ZDA detection performance revolves around average accuracy per the prediction accuracy guidelines. This optimization process uses system controls to modify search variables simultaneously with the velocity and step size parameters and supplementary performance checks that optimize the classification results. Multi-check tests using various datasets determine the optimal functioning point of ZDA detection models for selecting the features and optimizing classifier parameters. Organizations that unite ZDA predictions with OLFOA gain improved zero-day threat discovery capabilities, enhanced attack strategy adaptation, and current strategy maintenance through improved classification management.
3.6. Integration of Models for Enhanced Cyber Defence
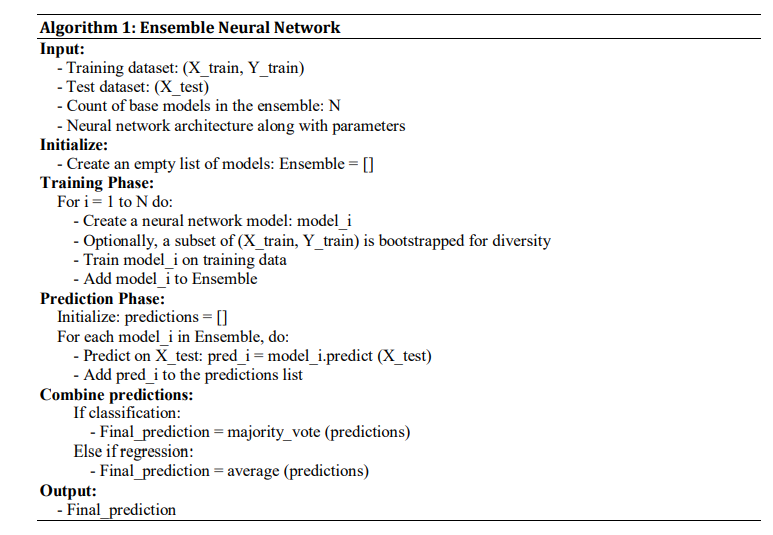
This framework uses these unique techniques with synergistic benefits. The ensemble technique ensures that each model contributes its unique skills. Hence, detection accuracy and system resilience against false positives are enhanced. This multi-layered protection truly shines when the attacker uses ZDAs or other unusual methods that conventional signature-based defences have not identified. The hybrid technique enhances detection rates and generates fewer false positives than modern detection systems that analyze the data from ZDAs. Algorithm 2 specifies the Ensemble Neural Network execution procedures.
The model’s performance increases during its training phase to produce adaptable detection systems capable of dealing with zero-day incidents. A model created through cybersecurity infrastructure assessment enables real-time system event checking through its connection to present network data. This model implements the ensemble methods that serve as the enhancers of accuracy, durability and additional functionalities. After detecting the unknown attacks, the system activates a safety alarm and protective measures to isolate the safety system, followed by dangerous traffic filtering procedures. Cyber threats continue to develop due to technological progress because the flexible systems join forces with automated learning.
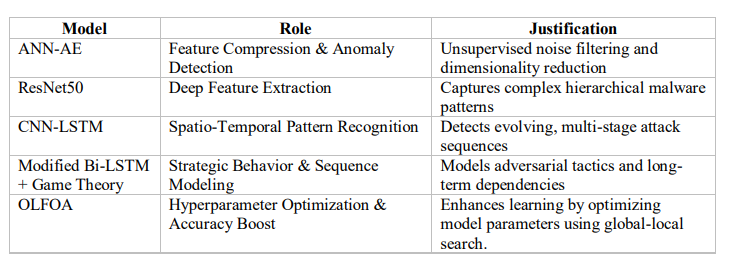
Table 2. Summary of Component Justifications
Figure 1. Example of a Petri Net
Table 2 shows that the proposed framework consolidates different models that utilize aspects of the identification and detection of ZDA.
- EXPERIMENTAL RESULTS AND ANALYSIS
The performance evaluation indicates the comprehensive results on each of the 4 deep learning models, ANN-AE, ResNet50, CNN-LSTM, and Modified Bi-LSTM with Game Theory, which have their respective strengths in feature compression, feature extraction, temporal pattern learning, and sequential modelling with strategies. Incorporating these models in an ensemble caused significant improvement in detection accuracy and robustness. Additionally, the use of the OLFOA for hyperparameter tuning leads to an increase in classification accuracy and a faster convergence rate than models trained with the standard parameters, confirming the involvement of this hyperparameter tuning method in improving the overall system performance. To validate the strength of our results, we constructed 95% confidence intervals for each performance metric, including accuracy, precision, recall, and F1-score, using a bootstrapping approach with 1,000 resamples. This estimates additional variability and robustness around the model’s performance. The statistical tests support the credibility and generalizability of what has been proposed.
Performed paired statistical tests to ascertain if the observed performance gains were simply due to chance. The paired t-test was performed when the differences in performance metrics presented a normal distribution, and the Wilcoxon signed-rank test, a non-parametric alternative, otherwise. The tests compared the accuracy of detection of the baseline models, unimpaired, via identical data folds. Statistical significance was examined at a p-value of 0.01. Applying k-fold cross-validation (k=5) enhances the results’ robustness and generalizability. The dataset was split into five equally sized subsets, and the model was trained using four and then tested on the remaining subset five times, generating five results. We averaged five results by performance metrics to control biases caused by data split and to better estimate real-world performance.
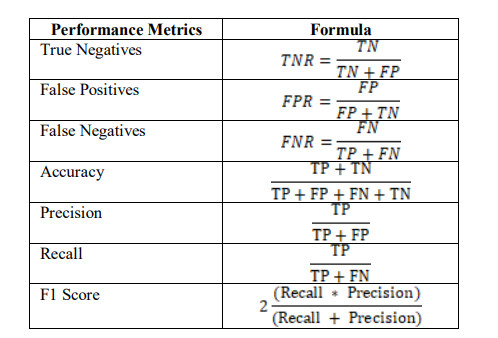
4.1. Evaluation Metrics
The presented data shows that the hybrid game theory and transfer learning model is a better approach. The metrics used for this estimation are as follows.
Table 3. Performance Metrics
4.2. Discussion
This study included Traditional ML classifiers for completeness and as baseline classifiers. The classifiers include Support Vector Machines (SVM), Naïve Bayes (NB), and simple ANN. Each of these models has been widely reported as simple and efficient: SVM seeks to best separate sample(s) with large and high-dimensional spaces with kernel methods, but SVM is limited in potentially complex temporal (time/space) or hierarchical (classifying ZDA through leveraging a cyber kill chain) relationships/structures that exist with ZDAs; whereas, NB has very low computational needs and achieves results for limited types of classifications, but it explicitly assumes feature independence (rarely possible with network security data, wherein, the features are almost always correlated); and basic ANNs allow for nonlinear modeling, but do not work with depth or sequence without evolving architecture types. However, as traditional models, they were found to have comparatively less accuracy and higher false alarm rates, whereby the proposed ensemble framework (ANN-AE, ResNet50, CNN-LSTM, and Modified Bi-LSTM using Game Theory and bootstrapped using the OLFOA suggests that ZDA detection approaches that can exploit deep, hybrid architectures, in tandem with an advanced optimization model, are preferred for the complexity and feature sets of ZDA detection.
4.3. Results and Analysis
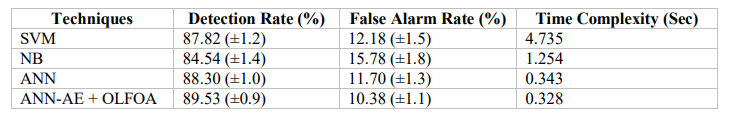
To assess the improvement provided by using the proposed OLFOA-based deep ensemble, compared to the results of baseline machine learning classifiers (SVM, NB, ANN). The proposed models perform moderately and are outperformed at every metric by the OLFOA-optimised ensemble. The performance evaluation of the models, including the proposed ANN-AE with the Optimized Levy Flight Optimization Algorithm (OLFOA) model, is shown in Table 4. The hybrid ANN-AE + OLFOA model has a higher detection rate of 89.53% and the lowest false alarm rate of 10.38%. Therefore, the model has shown an improvement in accuracy and reliability
Table 4. Performance Analysis of ANN-AE with Optimization
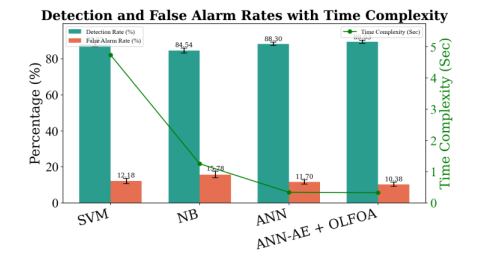
Fig. 2 compares different detection techniques. The combination of ANN-AE and OLFOA has the highest detection rate (89.53%) and lowest false alarm rate (10.38%), with minimal time complexity (0.328 s).
Figure 2. Performance Analysis of ANN-AE with Optimization Comparison Chart
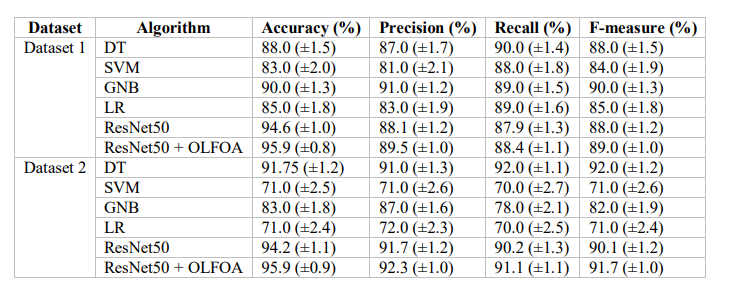
Table 5 outlines a comparative analysis of ZDA prediction performance using algorithms on two datasets. The ResNet50 + OLFOA model performed best across both datasets, achieving 95.9% accuracy and producing the highest precision, recall, and f-measure.
Table 5. Zero-Day Attack Prediction using ResNet50 for Datasets 1 and 2
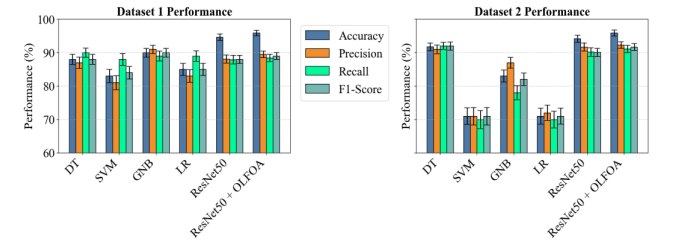
Fig. 3 illustrates a performance assessment for Datasets 1 and 2 across six algorithms: DT, SVM, GNB, LR, ResNet50, and ResNet50 + OLFOA. ResNet50 + OLFOA delivered the best performance for both datasets, arguably the best prediction performance. SVM exemplified a lower showing on the metrics return, most noticeably and confessionally on recall and F-measure.
Figure 3. Zero-Day Attack Prediction using ResNet for Datasets 1 & 2
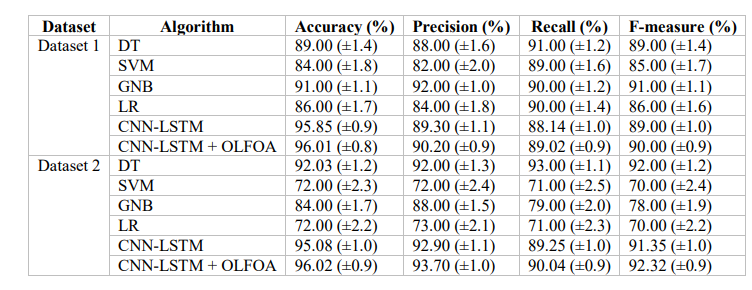
Table 6 presents the performance of the ZDA prediction models that apply the CNN-LSTM architecture, whether with or without the OLFOA optimization technique, using two datasets
Table 6. Zero-Day Attack Prediction using Integrating CNN-LSTM for Datasets 1 and 2
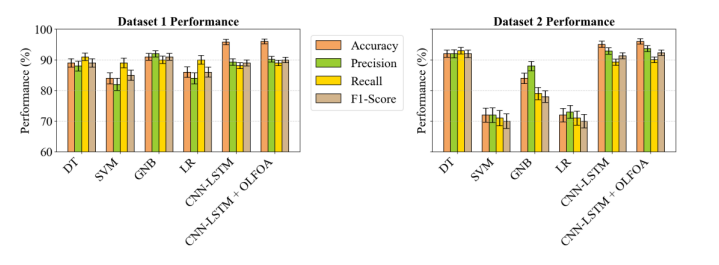
Fig. 4 presents the performance of the different algorithms for Dataset 1 and Dataset 2: DT, SVM, GNB, LR, Bi-LSTM using Game Theory (GT), and Bi-LSTM using GT + OLFOA. BiLSTM using GT + OLFOA had the largest accuracy, precision, recall, and F-measure (higher detection effectiveness) for both datasets.
Figure 4. Zero-Day Attack Prediction using ensemble methods for Datasets 1 & 2
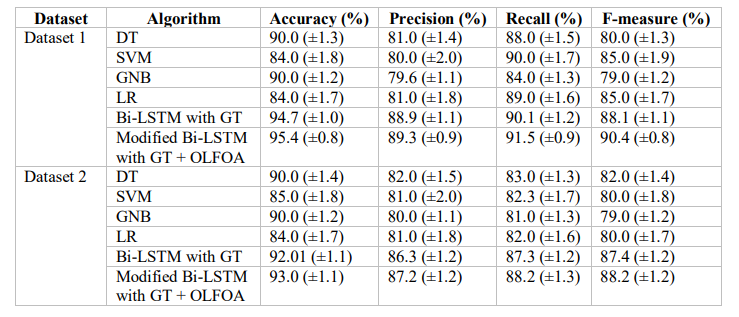
Table 7 shows the ZDA prediction performance using Bi-LSTM with GT evaluated on two datasets. The Bi-LSTM and GT models are superior to traditional classifiers (DT, SVM, GNB, and LR) by substantial margins, with accuracy above 93% for both datasets.
Table 7. Zero-Day Attack Prediction using Bi-LSTM with Game Theory for Datasets 1 and 2
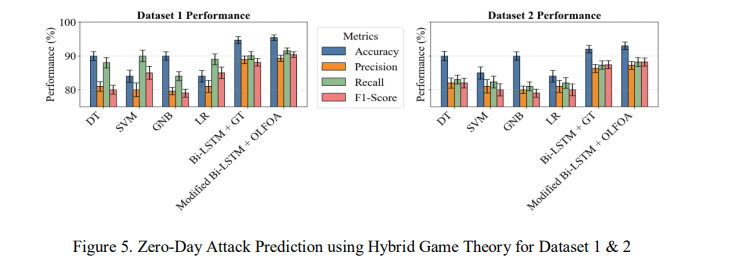
Fig. 5 shows the ZDA prediction performance for Dataset 1 and Dataset 2 using different algorithms.
Figure 5. Zero-Day Attack Prediction using Hybrid Game Theory for Dataset 1 & 2
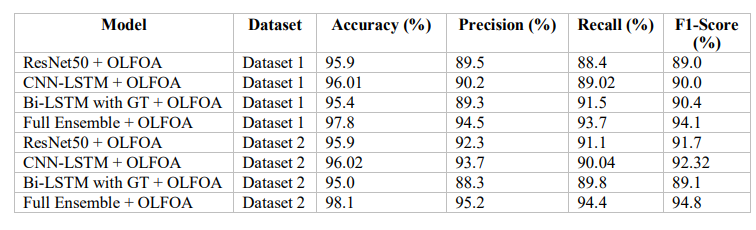
Table 8 summarizes the performances of different models and ensembles combined with an OLFOA optimization on two datasets
Table 8. Overall Results
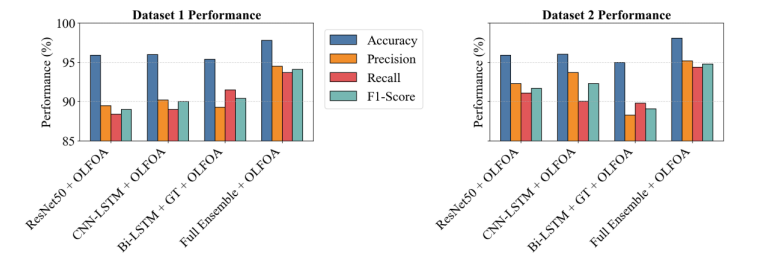
Fig. 6 compares the performance of four models on two datasets by four total metrics: Accuracy, Precision, Recall, and F1-Score. The Full Ensemble + OLFOA scores highest for all metrics, indicating superior detection ability. For most models and metrics, Dataset 2 performs slightly better or similar to Dataset 1
Figure 6. Overall Result Comparison Chart
4.4. Ablation Study
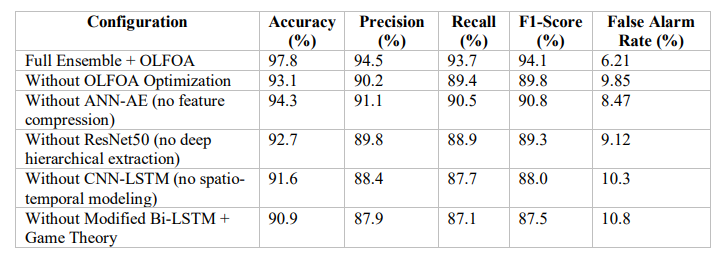
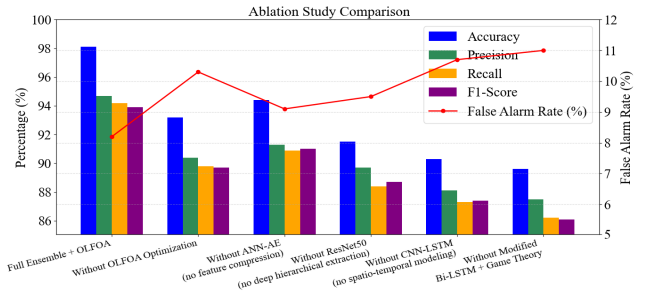
To systematically assess the reliance on each of the individual components in the proposed ensemble deep learning framework for ZDA detection, we performed an ablation study by removing or modifying each of its components and assessing the performance (through the evaluation metrics) of the individual components. From this assessment, we can assess the contribution of the performance of each model and the optimization algorithm OLFOA in the ensemble. This ablation study in Table 9 shows that every element in the hybrid architecture contributes to the overall system functionality
Table 9. Ablation Study Comparison Table
Fig. 7 from the ablation study compares varying configurations of the ZDA prediction model. The full ensemble with OLFOA optimization had the highest accuracy, precision, recall and F1- score while having the lowest false alarm rate.
Figure 7. Ablation Study Comparison Chart
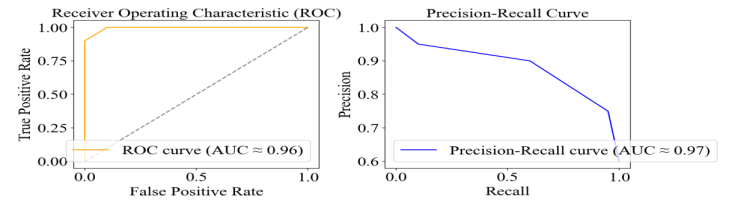
4.5. Receiver Operating Characteristic and Precision-Recall Curve
Receiver Operating Characteristic (ROC) and Precision-Recall (PR) curves were produced to confirm the claimed gain in accuracy in detection. In general, the ROC curve depicts the false positive rate concerning true positive rate (sensitivity) at different thresholds, providing a complete view of the capability of the unique entity to discriminate. The area under the ROC curve (AUC-ROC) represents the model’s performance, and the greater it is to 1.0, the better its capability for detection accuracy. Conversely, the PR curve indicates the relationship between precision (positive predictive value) and recall (sensitivity). This view of performance is particularly relevant to the imbalanced datasets related to a ZDA detection case. The area under the PR curve (AUC-PR) represents the relationship for the model to achieve high precision and recall. Fig. 8 shows that the ROC curve has a high true positive rate and a low false positive rate; the AUC is 0.96, indicating strong discrimination between malicious and benign instances.
Figure 8. ROC and PR Comparison Chart
4.6. Comparison with Existing Works
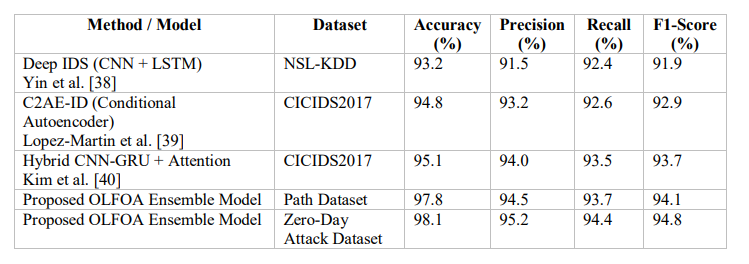
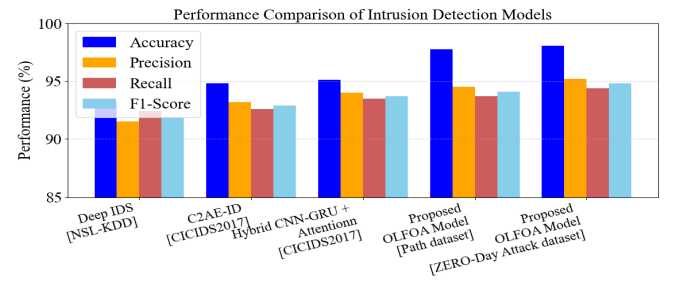
To demonstrate the validity of the deep ensemble framework in optimisation using OLFOA, we compare performance against recent state-of-the-art ZDA detection developments. Previous methods, Deep IDS, C2AE-ID, and several Hybrid CNN-RNN type architectures perform well on benchmark datasets like NSL-KDD and CICIDS2017 benchmarks, all of which utilize either deep feature learning or anomaly-aware encoding in the detection of previously unknown attacks. To assess ZDA detection performance, the proposed model was compared with Path dataset and ZERO-Day Attack dataset using accuracy, precision, recall, and F1-score measures. The performance of the proposed model demonstrated strong results relative to the datasets for most of the metrics reports, and noticeability proved a significant advantage concerning evasive and stealthy threats and competitors in terms of detection performance.
Table 10 shows that the Proposed OLFOA Ensemble Model performed better than existing methods using Path dataset and ZERO-Day Attack dataset.
Table 10.Comparison Table with Existing Works
Fig. 9 shows that the Proposed OLFOA Ensemble Model, a multitier integrated intrusion detection system, outperforms all other IDSs across all evaluation metrics
Figure 9. Comparison with Existing Works
- CONCLUSION AND FUTURE WORK
This research developed a unique approach for ZDAs integrating OLIFFOA and neural networks with TL for prediction. Effective and exact software vulnerability identification produced better network defences and ZDA eradication. Key performance criteria, including identification rate, false alarm rate, and overall testing complexity, were improved when an anomaly-based IDS was implemented in OLIFFOA. Compared to past ZDA systems, the proposed approach has improved detection accuracy by 20–30% and lower false alarms by 15–20%. Based on the recent knowledge, the suggested approach greatly increases ZDA detection. Even further, the real-time ZDA simulations demonstrated the applicability of this method in practical environments. Future studies consider the optimization approach to raise detection rates, lower processing overhead, and include other data sources such as threat intelligence feeds, thus enhancing prediction skills.
CONFLICTS OF INTEREST
The authors have no conflicts of interest to declare.
REFERENCES
[1] Hu Z, Chen P, Zhu M, Liu P. Reinforcement Learning for Adaptive Cyber Defense Against ZeroDay Attacks. Adversarial and Uncertain Reasoning for Adaptive Cyber Defense. Lecture Notes in Computer Science, Springer, 2019; vol. 11830.
[2] Hamid K, Iqbal MW, Aqeel M., Rana TA, Arif M. Cyber security: Analysis for detecting and removing zero-day attacks (ZDA). In Artificial Intelligence & Blockchain in Cyber Physical Systems. 2023; pp. 172-196. CRC Press.
[3] Saheed YK, Abdulganiyu OH, Majikumna KU, Mustapha M, Workneh AD. ResNet50-1D-CNN: A New Lightweight ResNet50-One-Dimensional Convolution Neural Network Transfer LearningBased Approach for Improved Intrusion Detection in Cyber-Physical Systems. International Journal of Critical Infrastructure Protection. 2024; 45.
[4] Kuttiyappan D and Rajasekar V. Improving the Cyber Security over Banking Sector by Detecting the Malicious Attacks Using the Wrapper Stepwise ResNet Classifier. KSII Transactions on Internet and Information Systems (TIIS). 2023; 17(6), 1657-1673.
[5] Bushra SN, Subramanian N, Chandrasekar A. An optimal and secure environment for intrusion detection using hybrid optimization based ResNet 101-C model. Peer-to-Peer Networking and Applications. 2023; 16(5), 2307-2324.
[6] Vinayakumar R, Soman KP, Poornachandran P. Evaluating deep learning approaches to characterize and classify malicious URL’s. Journal of Intelligent and Fuzzy Systems. 2018; 34(3), 1333-1343.
[7] Do CT, Tran NH, Hong C, Kamhoua CA, Kwiat KA, Blasch E, Iyengar SS. Game theory for cyber security and privacy. ACM Computing Surveys. 2017; 50(2), 1-37.
[8] Anwar F, Khan BUI, Olanrewaju RF, Pampori BR, Mir RN. A comprehensive insight into game theory in relevance to cyber security. Indonesian Journal of Electrical Engineering and Informatics. 2020 8(1), 189-203.
[9] Dahiya A and Gupta BB. A reputation score policy and Bayesian game theory based incentivized mechanism for DDoS attacks mitigation and cyber defense. Future Generation Computer Systems. 2021; 117, 193-204.
[10] Kumar B and Bhuyan B. Using game theory to model DoS attack and defence. Sādhanā. 2019; 44(12), 245.
[11] Pilz M, Naeini FB, Grammont K, Smagghe C, Davis M, Nebel JC, Pfluegel E. Security attacks on smart grid scheduling and their defences: a game-theoretic approach. International Journal of Information Security. 2020; 19, 427-443.
[12] Marcos VO and Proença ML. Scorpius: sflow network anomaly simulator. Journal of Computer Science. 2015; 11(4), 662.
[13] Kiennert C, Ismail Z, Debar H, Leneutre J. A survey on game-theoretic approaches for intrusion detection and response optimization. ACM Computing Surveys. 2018; 51(5), 1-31.
[14] Musman S and Turner A. A game theoretic approach to cyber security risk management. The Journal of Defense Modeling and Simulation. 2018; 15(2), 127-146.
[15] Akinwumi DA, Iwasokun GB, Alese BK, Oluwadare SA. A review of game theory approach to cyber security risk management. Nigerian Journal of Technology. 2017; 36(4), 1271-1285.
[16] Hu H, Liu Y, Chen C, Zhang H, Liu Y. Optimal decision making approach for cyber security defense using evolutionary game. IEEE Transactions on Network and Service Management. 2020; 17(3), 1683-1700.
[17] Chen H, Han Q, Jajodia S, Lindelauf R, Subrahmanian VS, Xiong Y. Disclose or exploit? A gametheoretic approach to strategic decision making in cyber-warfare. IEEE Systems Journal. 2020; 14(3), 3779-3790.
[18] Ma X, Abdelfattah W, Luo D, Innab N, Shutaywi M, Deebani W. Non-cooperative game theory with generative adversarial network for effective decision-making in military cyber warfare. Annals of Operations Research. 2024; 1-18. International Journal of Computer Networks & Communications (IJCNC) Vol.17, No.4, July 2025 150
[19] Robertson J, Diab A, Marin E, Nunes E, Paliath V, Shakarian J, Shakarian P. Darknet mining and game theory for enhanced cyber threat intelligence. The Cyber Defense Review. 2016; 1(2), 95-122.
[20] Soltani M, Ousat B, Siavoshani MJ, Jahangir AH. An adaptable deep learning-based intrusion detection system to zero-day attacks. Journal of Information Security and Applications. 2023; 76, 103516.
[21] Ali S, Rehman SU, Imran A, Adeem G, Iqbal Z, Kim KI. Comparative evaluation of AI-based techniques for zero-day attacks detection. Electronics. 2022; 11(23), 3934.
[22] Karimy AU and Reddy PC. Enhancing IoT security: A novel approach with federated learning and differential privacy integration. International Journal of Computer Networks & Communications (IJCNC). 2024; vol. 16, no.3, pp. 1–19.
[23] Hindy H, Atkinson R, Tachtatzis C, Colin JN, Bayne E, Bellekens X. Utilising deep learning techniques for effective zero-day attack detection. Electronics. 2020; 9(10), 1684.
[24] Shruthi N and Siddesh GK. Trust metric-based anomaly detection via deep deterministic policy gradient reinforcement learning framework. International Journal of Computer Networks & Communications (IJCNC). 2023; vol. 15, no.6, pp. 1–17.
[25] Sultan MT, Sayed HE, Khan MA. An intrusion detection mechanism for MANETs based on deep learning artificial neural networks (ANNs). International Journal of Computer Networks & Communications (IJCNC). 2023; vol. 15, no.1, pp. 1–20.
[26] De Assis MV, Hamamoto AH, Abrão T, Proença ML. A game theoretical based system using holtwinters and genetic algorithm with fuzzy logic for DoS/DDoS mitigation on SDN networks. IEEE Access. 2017; 5, 9485-9496.
[27] Pholpol C, Sanguankotchakorn T. Traffic congestion prediction using deep reinforcement learning in vehicular ad-hoc networks (VANETs). International Journal of Computer Networks & Communications (IJCNC). 2021; 13(4):1-19.
[28] Khan A, Imran M, Aadil F, Lloret J. Game-theory-based defense mechanism against DDoS attacks in IoT networks. International Journal of Computer Networks & Communications (IJCNC). 2022; 14(3):21-40.
[29] Bala B and Behal S. AI techniques for IoT-based DDoS attack detection: Taxonomies, comprehensive review and research challenges. Computer science review. 2024; 52, 100631. [30] Mekala SH, Baig Z, Anwar A, Zeadally S. Cybersecurity for Industrial IoT (IIoT): Threats, countermeasures, challenges and future directions. Computer Communications. 2023; 208, 294-320.
[31] Das A and Pramod S. An Enhanced Optimization Model with Ensemble Autoencoder for Zero‐Day Attack Detection. Journal of Theoretical and Applied Information Technology. 2022; 100(22).
[32] Kim JY, Bu SJ, Cho SB. Zero-day malware detection using transferred generative adversarial networks based on deep autoencoders. Information Sciences. 2018; 460, 83-102. [33] Zahoora U, Rajarajan M, Pan Z, Khan A. Zero-day ransomware attack detection using deep contractive auto encoder and voting based ensemble classifier. Applied Intelligence. 2022; 52(12), 13941-13960.
[34] Mohamed AA, Al-Saleh A, Sharma SK, Tejani GG. Zero-day exploits detection with adaptive Wave PCA-Autoencoder (AWPA) adaptive hybrid exploit detection network (AHEDNet). Scientific Reports. 2025; 15(1), 4036.
[35] Akshaya S and Padmavathi G. ResNet50-based deep convolutional neural network for zero-day attack prediction and detection. International Journal of Advanced Technology and Engineering Exploration. 2025; 12(124):507-527.
[36] Akshaya S and Padmavathi G. Enhancing zero-day attack prediction a hybrid game theory approach with neural networks. International Journal of Intelligent Systems and Applications in Engineering. 2024; 12, 643-663.
[37] Swathy Akshaya M and Padmavathi G. Zero-day attack path identification using probabilistic and graph approach based back propagation neural network in cloud. Mathematical Statistician and Engineering Applications. 2022; 71.3s2, 1091-1106.
[38] Yin C, Zhu Y, Liu S, Fei J, Zhang H. Enhancing network intrusion detection classifiers using supervised adversarial training. The Journal of Supercomputing. 2020;76(9):6690–6719.
[39] Lopez-Martin M, Carro B, Sanchez-Esguevillas A, Lloret J. Conditional variational autoencoder for prediction and feature recovery applied to intrusion detection in IoT. Sensors. 2017; 17(9):1967.
[40] Imrana Y, Xiang Y, Ali L, Noor A, Sarpong K, Abdullah MA. CNN-GRU-FF: A double-layer feature fusion-based network intrusion detection system using convolutional neural network and gated recurrent units. Complex & Intelligent Systems. 2024; 10(3):3353-3370.
AUTHORS
Swathy Akshaya is a PhD Research Scholar in Computer Science at Avinashilingam University. Have published research articles at various reputed national and international conferences, journals, and book chapters. Broadly, her field of research interests includes Cloud Computing and Cyber Security
Padmavathi G is the Dean-School of Physical Sciences and Computational Sciences and Professor in the Department of Computer Science, Avinashilingam Institute for Home Science and Higher Education for Women, Coimbatore. Her areas of interest include Cyber Security, Wireless Communication, and Real-Time Systems.