A FRAMEWORK FOR SECURING PERSONAL DATASHARED BY USERS ON THE DIGITAL PLATFORMS
Nirjhor Anjum 1 , Lamia Islam 2 , Md Rubel Chowdhury 3 , Ariful Alam 4
1 Researcher, SCIT, University of the Cumberlands, Williamsburg, KY, USA
2 Doctoral Researcher, PPPA, Washington State University, Pullman, WA, USA
3 Researcher, SCDM, London Metropolitan University, London, UK
4 Doctoral Researcher, CGPS, Trine University, Hamtramck, MI
ABSTRACT
Public disclosure of private data such as mobile phone numbers, dates of birth, identity card information, and financial data on social websites represents a significant threat to cybersecurity. Both external and internal intrusions infringe on users’ privacy, and the available security practices are not preventing unauthorized access. Substandard encryption, poor access controls, and weak policy enforcement form the core deficiencies of handling private data in this study. An in-depth analysis, comprising industry surveys, interviews with experts, and case studies of eCommerce and digital service companies, is carried out to assess the prevailing practices and their shortcomings. It is seen that most of the companies do not have adequate policies and technical measures, and user data is extremely susceptible to misuse. To fill this gap, a Citizen Digital Identity Portal (CDIP) is envisioned as an eGovernance project sponsored by the government. This solution combines encryption, access controls, and API-based identity confirmation to enable companies to confirm user identities without revealing or holding personal information. The threat of abuse by both internal and external entities is therefore greatly minimized. The study concludes that
companies cannot guarantee data security alone and that a policy-driven centralized model must be in place. The CDIP model helps bridge the gap between technology and cybersecurity rules. It offers a flexible and powerful way to protect personal information in today’s digital world.
KEYWORDS
Personal Data Security, Cybersecurity Framework, e-Governance and Data Protection, Data Privacy
Regulations, Secure Digital Identity
1. INTRODUCTION
Personal data security poses a significant challenge in today’s technological landscape, with hundreds of incidents occurring globally each day involving the leakage, disclosure, alteration, destruction, tampering, and misuse of personal information. The main reason for these problems is that there are no clear rules for how this data is collected, stored, and used. Both public and private entities, whether registered or not, embark on projects that involve extensive sharing of personal data, often neglecting the security of customer information. This paper aims to establish a technological framework that safeguards personal data from widespread misuse by public-private ventures and projects. The framework will be developed
within the realms of e-Governance and Cybersecurity, with a specific focus on Data Security. In the initial part of this paper, the research objectives, background, and methodology will be discussed. The next part of this paper will involve an empirical study shedding light on how data is leaked, distorted, and misused. This study will also explore efforts made by certain companies
5.1.1. Source of the Data
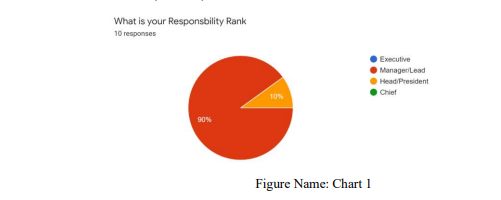
Figure 1.Chart 1
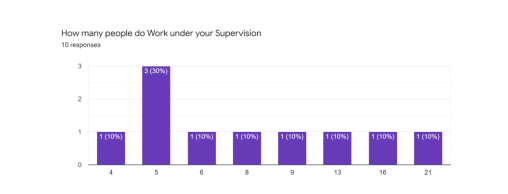
Figure 2.Chart 2
AUTHORS
Nirjhor Anjum is a cybersecurity expert, eGovernance strategist, and digital services specialist with a strong academic and industry background. As a National Cybersecurity Consultant for Ministry of Planning (BD), he contributed to the eGovernance projects. As an Assistant Professor at DIU and active researcher, he has contributed to cybersecurity, AI-driven automation, and software engineering through peer-reviewed publications. He has taught more than 2,300 students as an academician. In executive roles in the IT industry as CTO, CBO, and CAO, he led Cybersecurity, eGovernance, FinTech, Enterprise Automation, Business Intelligence, and various other enterprise digital transformation projects. With expertise in large-scale IT infrastructures, SaaS solutions, and public-sector digitalization, he is a thought leader connecting research with real-world innovation.