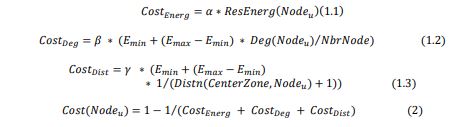IJCNC 05
DELAY AND THROUGHPUT AWARE CROSS LAYER TDMA APPROACH IN
WSN BASED IOT NETWORKS
BOUDI Raid 1 ,GHERBI Chirihane 2 and ALIOUAT Zibouda 2
1 LIRE Laboratory of Constantine 2, Abdelhafid Boussouf University
Center of Mila, 43000, Mila, Algeria.
2 LRSD Laboratory, Ferhat Abbas University of Setif, Setif, Algeria
ABSTRACT
The Internet of Things (IoT) encompasses a wide various of heterogeneous devices that leverage their capabilities in environmental sensing, data processing, and wireless communication. Among these, wireless sensors are one of the most widely used technologies in such networks. However, Wireless Sensor Networks (WSNs) face significant challenges in Medium Access Control (MAC), particularly in power management and network lifetime. To address these issues and enhance network efficiency and reliability, we propose a MAC approach for WSNs based on routing data. This approach, termed TDMA-CADH (TDMA Cross-Layer Approach Aware Delay/Throughput in Heterogeneous WSN), employs a cross-layer strategy to optimize resource utilization by minimizing transmission delay, maximizing channel throughput, and ensuring energy efficiency and extended network lifetime. The primary goal of this work is to design an effective MAC approach for WSNs that adhere to energy consumption and network lifetime constraints while reducing delay and improving channel throughput. To evaluate the performance of TDMA-CADH, we conducted simulations using the Network Simulator (NS-3) and compared it with existing approaches, including Random Leaves Ordering (RAND-LO), Depth Leaves Ordering (DEPTH-LO), Depth Remaining Leaves Ordering (DEPTH-RELO), and our initial version, Close Remaining Leaves Ordering (CLOSERELO). By including CLOSE-RELO in the comparison, we aimed to assess the advancements achieved in our new approach. The results demonstrate that TDMA-CADH significantly improves channel throughput and reduces transmission delay while maintaining energy efficiency and network lifetime. These findings suggest that our proposed method can effectively enhance the performance of Wireless Sensor Networks in IoT applications.
KEYWORDS
WSN, Cross-layer, TDMA, Routing, Transmission delay, Throughput, Latency, Energy.
1. INTRODUCTION
Technological advancements are primarily driven by the need to address societal requirements. Wireless sensor networks (WSNs), a transformative generation of networks, have become a reality and are significantly impact everyday life [1]. The integration of WSN-based solutions is rapidly expanding across various fields [2][3]. For instance, WSNs are critical in survival applications, such as the rapid detection of disasters like gas leaks in factories or forest fires through distributed sensors [4]. Today, we are witnessing the rise of numerous applications based on innovative concepts such as smart grids, smart homes, and intelligent transportation systems. These systems are interconnected infrastructure solutions that are transforming our world in unprecedented ways. These concepts are integral to the Internet of Things (IoT), where sensors
bridge the gap between physical infrastructure and information and communication technologies, enabling intelligent and secure monitoring and management through networked devices [5]
WSNs are considered a revolutionary approach to data collection, enhancing the reliability and efficiency of infrastructure systems. Compared to wired solutions [6], WSNs offer simpler deployment and greater device flexibility. Energy conservation in WSNs has been a primary focus for researchers [7], but this constraint has not overshadowed other critical objectives such as scalability, architecture, delay, routing, and throughput [8]. Several WSN applications are designed to manage critical scenarios where data recovery time is crucial [9–11].
This paper presents a study of key mechanisms to minimize delay in WSNs, particularly in single-hop and multi-hop configurations. Real-time applications often cannot tolerate data delays, making this a critical area of research. Our work begins with the construction of a hierarchical network structure following the random deployment of sensors in a defined area. The network area is subdivided into virtual zones, each managed by a cluster head selected using a proposed formula. Once clusters are formed, we focus on the method of allocating communication channels for intra-cluster communication. This channel access method, implemented through time slots allocated to cluster member nodes, is designed to optimize communication efficiency.
The primary objective of this work is to propose a novel slot allocation approach based on routing information (routing tree). This approach introduces the concept of independence between a node’s packets and those of its children in the routing tree. The significance of this technique lies in its ability to address delays and ensure fair access to the communication channel among cluster members. The proposed approach is evaluated using key performance metrics such as transmission delay, communication latency, TDMA (time division multiple access) length, throughput, and energy consumption. These evaluations are conducted using the widely recognized Network Simulator 3 (NS3).The main contributions of this paper are as follows:
· A new formula is proposed to establish a hierarchical network structure, enabling efficient cluster formation and cluster head selection.
· A novel TDMA scheduling method is introduced, leveraging routing tree information to optimize slot allocation and intra-cluster communication.
· The approach introduces the notion of independence between a node’s packets and those of its children in the routing tree, enhancing delay management and fairness in channel access.
· The proposed approach is evaluated using five key metrics: Transmission delay, Communication latency, TDMA length, Throughput and Energy consumption.
· The performance of the proposed approach is validated using the Network Simulator 3 (NS3), ensuring practical applicability and reliability.
The remainder of the paper is structured as follows: Section 2 reviews related work, Section 3 introduces the network structure, the proposed TDMA-CADH approach, and its modeling, Section 4 discusses the evaluation results, and Section 5 concludes the work with suggestions for future research.
2.LITERATURE REVIEW
Wireless sensor networks (WSNs) are an innovative technology that has permeated various fields, including environmental monitoring, healthcare, and military applications [12, 13]. These networks consist of small devices, known as sensors, equipped with data transmission and processing capabilities. The nodes in a WSN are deployed in a specific environment to collect essential information and collaborate to transmit it to a central sink. Communication within a
WSN is facilitated through a layered model, inspired by the OSI (Open Systems Interconnection) model, where each layer operates independently and is responsible for specific functionalities and optimizations [14–16].
This work focuses on applications that deploy sensor networks for environmental monitoring purposes. In such scenarios, sensors periodically collect data, which is then routed to the sink. Many WSN applications involve reactive assistance through actuators, where sensors and actuators work together, requiring varying degrees of transmission delay. For instance, forest fire monitoring and river water level monitoring are critical applications that demand rapid data delivery to the base station to prevent damage. While we do not address real-time issues directly, we aim to reduce transmission delays in multi-hop communications between sensors. Specifically, we focus on two layers crucial to communication decisions: the Network layer, which determines the path between transmitter and receiver using routing protocols, and the Data Link layer, which organizes access to the communication channel through MAC (Medium Access Control) protocols.
Cross-layering exploits dependencies between protocols across different layers to enhance performance [17]. This approach allows a protocol to utilize information from another protocol to achieve its objectives. Our work emphasizes cross-layer approaches between routing and MAC protocols, aiming to optimize transmission delay and throughput without compromising energy efficiency. At the network level, we consider multi-hop routing, which enables data relaying from a transmitter node to the control node. At the data link level, we focus on contention-free MAC protocols, such as TDMA (Time Division Multiple Access) [18]. In this context, the MAC protocol relies on information from the routing protocol to establish a communication schedule for network nodes.
Cross-layer MAC approaches can be categorized into two types: contention-based [19-20]and contention-free [19]. Contention-based approaches, such as MAC-CROSS [21], R-MAC [22], CL-MAC [23], and AreaCast [24], operate in a distributed manner. For example, MACCROSS reduces energy consumption by minimizing the number of active nodes during data transmission. It modifies RTS (Request To Send) and CTS (Clear To Send) packets by adding fields like “Final Destination Address” and “Next Address” to optimize routing [21]. Similarly, R-MAC uses a single control packet, called a “Pion,” to minimize end-to-end latency [22]. CLMAC improves traffic flow management and reduces delays using a Flow Setup Packet (FSP) [23], while AreaCast enhances routing reliability and energy efficiency by automatically replacing failed nodes [24]. In contrast, contention-free cross-layer MAC approaches, such as CoLaNet [25], Rand-LO, Depth-LO, Depth-ReLO [26–29], and Close-ReLO [30], adopt centralized techniques. CoLaNet, for instance, constructs a routing tree called MinDegree and uses a coloring algorithm to establish a TDMA schedule for each node, optimizing energy use and reducing interference [25]. However, CoLaNet’s initial node coloring process, which starts with the node of the highest degree, may not optimize latency. To address this, Rand-LO randomly selects leaves of the routing tree for time slot allocation [26], while Depth-LO sorts leaves based on their depth in the tree, prioritizing those farthest from the sink [27, 28]. Close-ReLO introduces a different approach by prioritizing nodes closer to the root, regardless of their depth, to optimize resource allocation and improve network performance [30]. Despite their advantages, contention-based MAC protocols using a distributed approach with network layer coordination have limitations [28]. For instance, the routing protocol is not explicitly specified, and sleep/wake periods are only defined for direct neighbors, leaving other nodes unaccounted for. Additionally, simultaneous transmissions are not managed effectively.
Centralized approaches, such as TDMA without contention, also face challenges. For example, in CoLaNet, Rand-LO, Depth-LO, and Depth-ReLO, the initial node selection for coloring may impact latency, and coloring all neighbors of an already colored node may not align with communication directions. Nodes in the middle of the routing tree must wait for their predecessors to complete transmissions before sending their own data, which can introduce delays.
3. MODELING AND METHODOLOGY
3.1. Hierarchical Structure
Routing protocols in wireless sensor networks (WSNs) can be categorized based on network structure into flat routing protocols and hierarchical routing protocols. In flat routing protocols, all nodes generally assume identical roles and functionalities. Conversely, hierarchical routing protocols assign specific roles to certain sensors, granting them privileged functions compared to others. A critical factor in enhancing the lifetime and efficiency of WSNs is the design of the network. In this section, we outline the proposed methodology for constructing an adaptive hierarchical structure, specifically focusing on clustering-based network design. Zone-Based partitioning. The network is initially partitioned into square zones of equal size, determined by the number of deployed nodes. Following this subdivision, each zone is assigned a unique identifier, referred to as the Zone ID, and is characterized by its specific coordinates (x_Zone, y_Zone). This spatial partitioning is illustrated in Fig. 1, which provides a visual representation of the network divided into zones.
Figure 1. Network area partitioning into zones.
Establishing network topology. The initialization phase of wireless sensor networks begins with neighbor discovery, where each node broadcasts a HELLO message containing its details. This process collects essential information about neighboring nodes, enabling the selection of optimal neighbors and forwarders. The phase concludes with the creation of a neighborhood table, which supports efficient communication and routing decisions. Cluster-Head Selection. In clustering networks, selecting cluster heads (CHs) is vital for network efficiency. Clustering organizes nodes into local groups, each comprising a CH and member nodes [31]. CHs manage communication between their members and the base station (BS), while member nodes rely on CHs for data transmission. Since CHs consume more energy, their election is based on metrics like residual energy (ResEnerg(Nodeu)), distance from the zone center (Distn(CenterZone, Nodeu)), and node weight, Deg(Nodeu), representing the number of neighbors. Each node calculates its cost using Equation (2), where NbrNode is the total number of nodes in the network, and α, β, and γ are weighting parameters for the metrics. The node with
the highest score in its zone becomes the CH. This process ensures energy efficiency and extends thenetwork’s lifetime, with Emin and Emax defining the minimum and maximum energy values within the energy interval. Fig. 2 illustrates this phase.
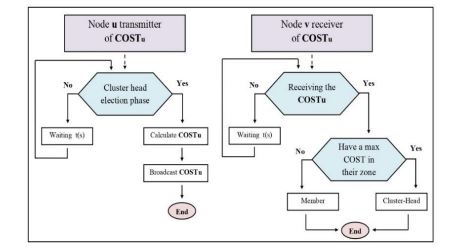
Figure 2. Diagram illustrating the process of selecting a cluster head.
Cluster Creation. In this phase, cluster heads (CHs) broadcast a message to announce available clusters and invite nodes to join. Non-CH nodes receive this message and select the nearest CH based on proximity. They then send a join request to their chosen CH. This process, illustrated in Fig. 3, establishes the cluster structure within the network.
3.2. Proposed Approach
In this section, we will present our proposed approach that is dedicated not only to intra-cluster communications but also to inter-cluster communications. For this purpose, a multi-hop cluster tree must be considered in order to apply this TDMA scheduling approach.
Figure 3. Diagram illustrating the process of cluster formation.
Functioning of TDMA-CADH approach. The principle and objective of the TDMA-CADH approach, not only the minimization of transmission delays but also the fairness in the sharing of the channel between the network nodes is ensured. For each cluster of the network, the scheduling principle is summarized in 4 steps:
- Select an unvisited node in the cluster, giving the priority to a node with the least depth.
- If there is more than one node selected in step 1, a node is designated randomly.
- Find a compatible slot for each selected node by following these steps:
- Define this node as a visited node.
- Find a compatible slot for this node by starting the search from the beginning of TDMA.
- For all successive parents (non-root) of this node, find a slot by applying the bottom-up slot allocation method.
- Repeat from step 1 until all nodes in the cluster are visited. The algorithm 1 (See Fig.4) below
shows the TDMA scheduling process for the TDMA-CADH approach.
The following functions are used in Algorithm 1:
- AddNode(u, N): Adds node u to the vector N.
- ClosestNode(N): Retrieves a node from vector N with the smallest depth in the cluster’s routing tree.
- PathToRootOfNode(u): Returns the path toward the root in the routing tree of node u.
- firstNodeOf(PathToRoot): Retrieves the first node in the path toward the root of the tree.
- compatibleSlotForNode(v, i): Checks if slot i is compatible with node v.
- deleteFirstNodeOf(vector): Removes the first node from the specified vector.
- addNodeInTransmitterVector(v, i): Adds node v to its compatible slot i as a sender.
- addNodeToReceiverVector(w, i): Adds node w to its compatible slot i as a receiver.
- getParentId(A, v): Retrieves the parent node of v.
- lengthVector(vector): Returns the size of the specified vector.
- addNewSlotInTransmitterVector() and addNewSlotInReceiverVector(): Adds a new slot at the end of the TDMA schedule for transmitters and receivers, respectively.
- DeleteNode(u, N): Deletes node u from vector N
Figure 4. Proposed TDMA-CADH Approach (Algorithm 1)
3.3. Notations and Modeling
Network Connectivity.We model a wireless sensor network (WSN) as an undirected graph G=(V,E), where V represents the set of vertices (network nodes) and E represents the set of edges (connections between sensors). In a network of N sensors, each node is identified by an integer i∈[0,N], with node 0 representing the sink (SB). The sink is always positioned at the center of the upper side of the deployment area. Nodes are deployed randomly and remain stationary within the area of interest.
The highest level contains the sink (or cluster head), which connects to nodes at lower levels. These nodes, in turn, may connect to other nodes at even lower levels, forming a routing tree. The purpose of this tree is to identify a relay node (parent node) for each transmitting node, which forwards data toward the sink or cluster head. In our research, the geographic distance is the metric used to construct the tree, resulting in a geographic tree. The sink (or cluster head) serves as the root, and each node selects its nearest neighbor to the sink as its parent. The routing tree is defined by a vector A=[P1,…,Pi,…,Pn], where each element Pi represents the parent identifier of node i in the tree.
Pathway to the Root. In a sensor network, the path P(n,r) represents the route data takes from node n to the root r. Specifically, P(n,r) denotes the sequence of nodes a data packet traverses to reach the root from node n.
Conflicting Nodes List. In wireless networks, including WSNs, shared communication media expose transmissions to interference. In our simplified interference model, each node v maintains a list of nodes that cannot transmit simultaneously with it. Interference is defined by a vector C=[(v1,L1),…,(vi,Li),…,(vn,Ln)], where each element Ci is a pair (vi,Li). Here, vi is the node identifier, and Li is the list of nodes conflicting with vi. A conflict exists between nodes vi and vj if:
- Both nodes are a child and its parent (∀(i,j)∈E).
- An intermediate node connects them, where the intermediate node is the parent of at least
one of the two nodes (∀(i,k),(k,j)∈E such that k=parent(i) or k=parent(j)).
TDMA Modeling. A TDMA schedule consists of numbered slots of varying lengths. During a slot, a node can transmit its own data or data from its children, while other nodes enter sleep mode to conserve energy, except for the parent of the transmitting node, which remains active to receive data. Conflicting nodes cannot share the same time slot. We model TDMA in a sensor network using an allocation matrix Schedulen×L, where n is the number of nodes and L is the TDMA length (number of slots). Each element Frame[i,j] of the matrix is defined as follows:
- Frame[i,j]=node identifier: Node i is in transmission mode during slotj.
- Frame[i,j]=node identifier: Node i is in reception mode, receiving data from its child during slot j.
- Frame[i,j]=0: Node i is in sleep mode during slot j, neither transmitting nor receiving.
3.4. Evaluation Metrics
Numerous MAC approaches leveraging routing information exist in the literature. To evaluate their performance, we define five key metrics: delay, latency, throughput, TDMA length, and energy consumption, which are critical in WSNs. In periodic communication mode, where each sensor transmits a packet per frame, latency is measured from a reference time t0t0 (frame initiation), while transmission delay is measured from the actual time the node transmits its packet. These metrics ensure a comprehensive assessment of performance.
Average transmission delay in the cluster.The transmission delay in a wireless sensor network (WSN) refers to the time between a sensor node sending a data packet and its reception at the destination. It is measured in time units (UT), where each UT represents the duration of transmitting and receiving a single packet. In a hierarchical network, the cluster head (CH) establishes the TDMA table and collects data from its cluster members.
For a member node i sending a packet to the CH (nCH) via the path ni→n1→n2→⋯→nk→nCH, the transmission delay for node i is calculated as:
These equations ensure that energy efficiency is maintained while optimizing delay and latency.
3.5. Demonstrative Instance
In this section, we provide an illustrative example to demonstrate our concept (see Fig. 5). The left side of the figure depicts a graph modeling a cluster with 11 nodes, where node 1 serves as the cluster head (CH). The right side of the figure shows the corresponding routing tree for this cluster, with node 1 as the root and the remaining nodes as members. These member nodes transmit captured data to the root in a multi-hop manner. To evaluate the performance of different
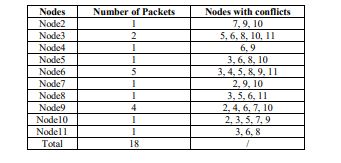
approaches, we compare them using the metrics outlined earlier. Table 1 summarizes, for each member node, the number of packets transmitted in one round and the list of conflicting nodes, determined by applying the two conditions described in Section 3.3.

Figure 5. Examples of a graph representing the topology of a cluster (left) and its routing tree (right).
Table 1. Transmitted Packets vs. Conflict Nodes within the clusterrepresented in Fig.5.
a) Depth-Relo Approach Intra-Cluster
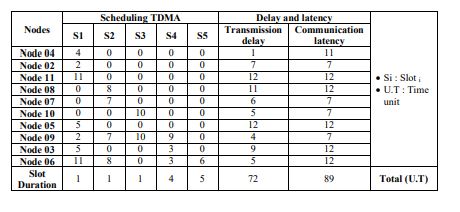
Table 2 represents the TDMA scheduling, delay, and latency by applying the Depth-ReLO approach on the cluster shown in Fig.5.
Table 2. Scheduling, delay, and latency according to the Depth-ReLO approach.
The slot duration is expressed in U.T time units (for example in microseconds) where each U.T represents the duration to send a single packet. From the table 2 we notice that the duration of Slot 4 is equal to 4 U.T where we find only one node (node 9) which is concerned with the transmission of data. So, using the routing tree illustrated in Fig.4 we can see that this node will transmit four packets (it needs four U.T); consequently, 4 U.T is the duration of this slot.
b) Depth-LO Approach Intra-Cluster
The table 3 represents the TDMA scheduling, delay, and latency by applying the Depth-LO approach on the cluster shown in Fig.5.
Table 3. Scheduling, delay and latency according to the Depth-LO approach.
c) Rand-LO Approach Intra-Cluster
The table 4 represents the TDMA scheduling, delay and latency by applying the Rand-LO approach on the cluster shown in Fig.5.
Table 4. Scheduling, delay and latency according to the Rand-LO approach.
d) Close-ReLO Approach Intra-Cluster
The table 5 represents the TDMA scheduling, delay and latency by applying the Close-ReLO approach on the cluster shown in Fig.5.
Table 5. Scheduling, delay and latency according to the Close-ReLO approach.
e) TDMA-CADH Approach Intra-Cluster
The table 6 represents the TDMA scheduling, delay and latency by applying the TDMA-CADH approach on the cluster shown in Fig.5.
Table 6. Scheduling, delay and latency according to theTDMA-CADH approach.
The following table 7 summarizes the results found in each approach.
Table 7. Table summarizing approach results.
4.RESULTS AND DISCUSSION
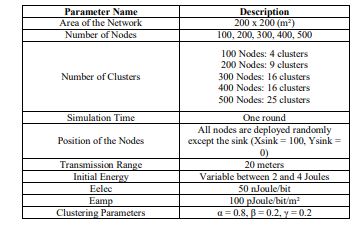
NS-3, a discrete event network simulator for research and teaching, is free software under GNU GPLv2. We used version 27 on Ubuntu 16.04 for our simulations. Table 8 lists the simulation parameters. To highlight the contribution of our proposed approach, we provide comparisons based on the evaluation metrics in Section 3.4.
Table 8. Simulation Parameters
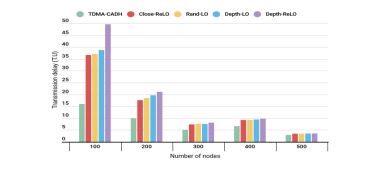
4.1. Comparison by Transmission Delay
The graph in Fig. 6 illustrates the average transmission delay per cluster relative to the number of nodes, revealing that TDMA-CADH achieves the lowest delay by decoupling a node’s packets from those of its children, enabling immediate data transmission without waiting. In contrast, Close-ReLO, Rand-LO, and Depth-LO exhibit stabilizing delays due to their shared “leaf privilege” scheduling principle, which prioritizes leaf nodes. Depth-ReLO, however, incurs the highest delay as it prioritizes nodes farthest from the root, delaying transmissions for nodes with fewer packets. Notably, the average delay decreases as the number of nodes increases across all approaches, attributed to the consistent depth of nodes in the routing tree and the dynamic nature of cluster sizes and network cluster counts.
Figure 6. Average transmission delay per cluster.
4.2. Comparison by Communication Latency
This graph depicts the average communication latency as a function of the number of nodes, with the results in Fig. 7 aligning closely with those in Fig. 7, as transmission delay directly impacts communication latency. The observed consistency between the two metrics stems from the same underlying factors discussed earlier. Specifically, TDMA-CADH demonstrates the lowest latency due to its efficient packet separation mechanism, while Depth-ReLO exhibits the highest latency, as its prioritization of distant nodes delays transmissions for nodes with fewer packets. These findings reinforce the relationship between transmission delay and communication latency across the evaluated approaches.
Figure 7. Average communication latency per cluster.
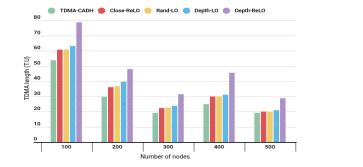
4.3. Comparison by TDMA Length
Fig. 8 illustrates the average intra-cluster TDMA length relative to the number of nodes for the discussed approaches. The results demonstrate that the TDMA-CADH approach achieves the shortest TDMA length, outperforming all other methods, while Depth-ReLO records the longest TDMA length. This highlights the significant improvement offered by TDMA-CADH in minimizing the average TDMA length per cluster. The efficiency of TDMA-CADH stems from its ability to decouple the packets of a node from those of its children, eliminating unnecessary delays. For instance, in traditional approaches, if two nodes share the same slot—one transmitting two packets (2 U.T) and the other four packets (4 U.T)—the slot size expands to 4 U.T, causingthe first node to experience a 2 U.T delay. In contrast, TDMA-CADH avoids such inefficiencies, ensuring optimal slot utilization and minimal TDMA length.
Figure 8. Average length TDMA per cluster.
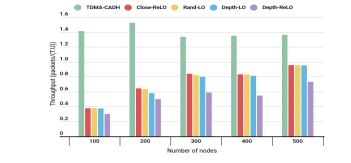
4.4. Comparison by Throughput
Fig. 9 depicts the average throughput in relation to the number of nodes, comparing the performance of different approaches. In this periodic communication mode, where all approaches start with the same number of packets and routing tree, the variation in throughput is directly influenced by the differences in TDMA length. A higher throughput corresponds to a shorter TDMA length, as it allows for more efficient data transmission within the same timeframe. The results from Fig. 8 and Fig. 9 confirm that the TDMA-CADH approach achieves the highest throughput, attributed to its minimal TDMA length. This efficiency underscores the superiority of TDMA-CADH in optimizing throughput by reducing unnecessary delays and maximizing slot utilization.
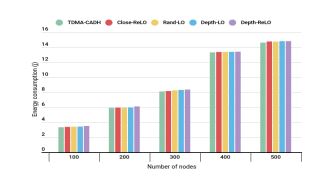
Figure 9. Average energy consumption per cluster.
4.5. Comparison by Total Energy Consumed
The graph illustrates the average energy consumption relative to the number of nodes, comparing the energy efficiency of different approaches during both the setup phase and data transmission for a single frame (See Fig.10). As the primary focus is on modifying TDMA scheduling, the evaluation of average energy consumption per cluster ensures that TDMA-CADH maintains energy efficiency without compromise. The results reveal that all approaches, including TDMA-CADH, exhibit similar energy consumption levels with slight variations, confirming that the proposed modifications do not negatively impact energy usage. This consistency highlights that TDMA-CADH achieves its scheduling improvements without introducing additional energy overhead.
In the following analysis, we evaluate the performance of the approaches by scaling the network under fixed conditions. Specifically, the number of cluster heads is set to 9, while the number of nodes is varied from 100 to 300. This setup allows us to assess the scalability and efficiency of each approach as the network size increases. The evaluation is conducted based on the following performance metrics. The motivation behind this analysis is to understand how the approaches perform in larger networks while maintaining a consistent cluster structure, ensuring that the solutions remain effective and energy-efficient even as the number of nodes grows. This is critical for real-world applications where network scalability and resource optimization are key concerns.
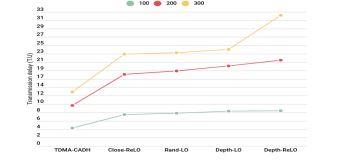
4.6. Comparison by Transmission Delay (Scalability)
The results in Fig. 11 illustrate the relationship between average transmission delay and the number of nodes, confirming earlier findings and demonstrating the scalability of the approaches. As the network density increases with more nodes, clusters become denser, leading to higher transmission delays. Among the evaluated methods, Close-ReLO and TDMA-CADH consistently achieve the shortest delays, proving their effectiveness in handling higher network density. Conversely, Depth-ReLO exhibits the longest delays due to its prioritization mechanism, as previously discussed. These findings, supported by Fig. 11, highlight the influence of network density on transmission delay and underscore the superior performance of Close-ReLO and TDMA-CADH in maintaining efficiency as the network scales.
Figure 11. Average transmission delay per cluster (Scalability).
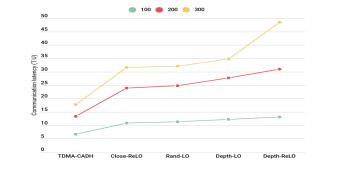
4.7. Comparison by the Latency of Communications (Scalability)
This graph depicts the average communication latency relative to the number of nodes. As shown in Fig. 12, the evolution of average intra-cluster communication latency is presented, revealing that Close-ReLO and TDMA-CADH achieve the lowest delays. These approaches outperform others due to their efficient scheduling mechanisms, which minimize latency. In contrast, the remaining approaches exhibit higher latencies, attributed to the same factors discussed earlier, such as prioritization strategies and network density. These results further emphasize the effectiveness of Close-ReLO and TDMA-CADH in reducing communication latency, even as the network scales.
Figure 12. Average communication latency per cluster (Scalability).
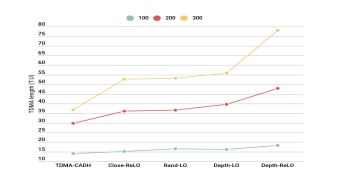
4.8. Comparison by TDMA length (Scalability)
The graph presents the average TDMA length aboutthe number of nodes, comparing the performance of different approaches. As shown in Fig. 13, the average TDMA length per cluster is evaluated for network sizes of 100, 200, and 300 nodes. A clear trend emerges as the number of nodes increases, with cluster size expanding and influencing the TDMA length. The results reveal that our approach achieves a shorter TDMA length compared to other methods, particularly in large-scale networks. This advantage underscores the effectiveness of our approach in optimizing scheduling and maintaining efficiency, even as the network grows in size and complexity
Figure 13. Average length TDMA per cluster (Scalability).
This graph illustrates the average channel throughput in relation to the number of nodes. As demonstrated in Fig. 14, the TDMA-CADH approach achieves the highest average channel operation rate compared to the other methods. This superior performance is directly linked to the TDMA length, as previously explained. When two approaches transmit the same number of packets within a frame, the one with the shorter TDMA length achieves a higher operation rate. The results confirm that TDMA-CADH, with its minimal TDMA length, maximizes throughput, highlighting its efficiency in optimizing channel utilization and enhancing overall network performance
Figure 14. Average throughput per cluster (Scalability).
5. CONCLUSIONS
The Internet of Things (IoT) represents a transformative advancement in connectivity, integrating billions of heterogeneous devices, with wireless sensor networks (WSNs) playing a pivotal role. These networks, composed of sensors with varying computational, storage, and energy capacities, are tasked with collecting and transmitting environmental data to a base station. Addressing the challenges of minimizing transmission delay and ensuring fair channel utilization, this work leverages cross-layer optimization between the network and MAC layers. We propose two novel approaches: Close-ReLO, a TDMA-based MAC protocol that optimizes scheduling using routingtree information to reduce delay, and TDMA-CADH, which extends this by ensuring fairness in channel access while further minimizing latency. Simulations on the NS3 platform demonstrate that both approaches significantly outperform existing methods in terms of delay and latency while maintaining energy efficiency through optimized duty cycles and interference-free simultaneous communications. Additionally, both methods exhibit strong scalability, adapting effectively to larger network sizes.For future work, we propose extending the evaluation of Close-ReLO and TDMA-CADH to inter-cluster communication scenarios to assess their scalability in more complex topologies. Integrating these approaches with advanced clustering techniques could further enhance network efficiency. Additionally, exploring their application in flat network architectures and extending cross-layer optimization to include the physical layer would provide a more holistic framework
for performance improvement. Finally, incorporating greater heterogeneity in sensor communication technologies could address the diverse requirements of emerging IoT applications. These directions aim to build on the strengths of our current contributions and address the evolving challenges in WSNs and IoT systems.
CONFLICTS OF INTEREST
The authors declare no conflict of interest
ACKNOWLEDGEMENTS
The authors would like to thank everyone, just everyone!
REFERENCES
[1] Neelam Srivastava. (2010) “Challenges of next-generation wireless sensor networks and its impact on society,” arXiv preprint arXiv:1002.4680.
[2] Mamoona Majid, Shaista Habib, Abdul Rehman Javed, Muhammad Rizwan, Gautam Srivastava, Thippa Reddy Gadekallu, & Jerry Chun-Wei Lin. (2022) “Applications of wireless sensor networks and internet of things frameworks in the industry revolution 4.0: A systematic literature review,” Sensors, Vol. 22, No. 6, pp. 2087.
[3] Sanaz Sadeghi, Nazi Soltanmohammadlou, & Farnad Nasirzadeh. (2022) “Applications of wireless sensor networks to improve occupational safety and health in underground mines,” Journal of Safety Research.
[4] Imane Benkhelifa, Nadia Nouali-Taboudjemat, & Samira Moussaoui. (2014) “Disaster management projects using wireless sensor networks: An overview,” In 2014 28th International Conference on Advanced Information Networking and Applications Workshops, pp. 605–610. IEEE.
[5] Khalid Haseeb, Ikram Ud Din, Ahmad Almogren, & Naveed Islam. (2020) “An energy efficient and secure IoT-based WSN framework: An application to smart agriculture,” Sensors, Vol. 20, No. 7, pp. 2081.
[6] Orazio Mirabella & Michele Brischetto. (2010) “A hybrid wired/wireless networking infrastructure for greenhouse management,” IEEE Transactions on Instrumentation and Measurement, Vol. 60, No. 2, pp. 398–407.
[7] P.S. Shiju Kumar & A. Ramesh Babu. (2022) “Dolphin echolocation optimized sailfish algorithm for energy efficient and secured routing based on trust management in Zigbee wireless sensor network,” Transactions on Emerging Telecommunications Technologies, Vol. 33, No. 9, pp. e4539.µ
[8] Munuswamy Selvi, P. Velvizhy, Sannasi Ganapathy, H. Khanna Nehemiah, & Arputharaj Kannan.(2019)“A rule-based delay-constrained energy-efficient routing technique for wireless sensornetworks,”Cluster Computing, Vol. 22, pp. 10839–10848.[9] Messaoud Doudou, Djamel Djenouri, Nadjib Badache, & Abdelmadjid Bouabdallah. (2014) “Synchronous contention-based MAC protocols for delay-sensitive wireless sensor networks: A review and taxonomy,” Journal of Network and Computer Applications, Vol. 38, pp. 172–184.
[10] Ying Li & Radim Bartos. (2014) “A survey of protocols for intermittently connected delay-tolerant wireless sensor networks,” Journal of Network and Computer Applications, Vol. 41, pp. 411–423.
[11] Messaoud Doudou, Djamel Djenouri, &NadjibBadache. (2012) “Survey on latency issues of asynchronous MAC protocols in delay-sensitive wireless sensor networks,” IEEE Communications Surveys & Tutorials, Vol. 15, No. 2, pp. 528–550.
[12] Luis M. Borges, Fernando J. Velez, & Antonio S. Lebres. (2014) “Survey on the characterization and classification of wireless sensor network applications,” IEEE Communications Surveys & Tutorials, Vol. 16, No. 4, pp. 1860–1890.
[13] Srinivasa Prasanna & Srinivasa Rao. (2012) “An overview of wireless sensor networks applications and security,” International Journal of Soft Computing and Engineering, Vol. 2, No. 2, pp. 2231– 2307.
[14] Beom-Su Kim, HoSung Park, Kyong Hoon Kim, Daniel Godfrey, & Ki-Il Kim. (2017) “A survey on real time communications in wireless sensor networks,” Wireless Communications and Mobile Computing, Vol. 2017.
[15] Preeti Sinha, V.K. Jha, Amit Kumar Rai, & Bharat Bhushan. (2017) “Security vulnerabilities, attacks, and countermeasures in wireless sensor networks at various layers of OSI reference model: A survey,” In 2017 International Conference on Signal Processing and Communication (ICSPC), pp. 288–293. IEEE.
[16] Michelle Wetterwald, Fatma Hrizi, & Pasquale Cataldi. (2010) “Cross-layer identities management in ITS stations,” In Proc. of the 10th IEEE International Conference on ITS Telecommunications (ITST’10).
[17] Samiya Shimly, David B. Smith, & Samaneh Movassaghi. (2017) “Cross-layer optimized routing with low duty cycle TDMA across multiple wireless body area networks,” In 2017 IEEE International Conference on Communications (ICC), pp. 1–6. IEEE.
[18] ChahrazedBenrebbouh& Lemia Louail. (2021) “Dynamic TDMA for wireless sensor networks,” In 2021 30th Wireless and Optical Communications Conference (WOCC), pp. 204–208. IEEE.
[19] Dietmar Petras, Andreas Kramling, & Andreas Hettich. (1996) “MAC protocol for wireless ATM: Contention-free versus contention-based transmission of reservation requests,” In Proceedings of PIMRC’96-7th International Symposium on Personal, Indoor, and Mobile Communications, Vol. 3, pp. 903 907. IEEE.
[20] Khaled Abid, Hicham Lakhlef, & Abdelmadjid Bouabdallah. (2021) “A survey on recent contention-free MAC protocols for static and mobile wireless decentralized networks in IoT,” Computer Networks, Vol. 201, pp. 108583.
[21] Changsu Suh, Young-Bae Ko, & Dong-Min Son. (2006) “An energy-efficient cross-layer MAC protocol for wireless sensor networks,” In Advanced Web and Network Technologies, and Applications: APWeb 2006 International Workshops, pp. 410–419. Springer.
[22] Shu Du, Amit Kumar Saha, & David B. Johnson. (2007) “RMAC: A routing-enhanced duty-cycle
MAC protocol for wireless sensor networks,” In IEEE INFOCOM 2007-26th IEEE International Conference on Computer Communications, pp. 1478–1486. IEEE.
[23] Mohamed S. Hefeida, Turkmen Canli, & Ashfaq Khokhar. (2013) “CL-MAC: A cross-layer MAC protocol for heterogeneous wireless sensor networks,” Ad Hoc Networks, Vol. 11, No. 1, pp. 213– 225.
[24] Karel Heurtefeux, Florence Maraninchi, & Fabrice Valois. (2011) “Areacast: A cross-layer approach for communication by area in wireless sensor networks,” In 2011 17th IEEE International Conference on Networks, pp. 112–117. IEEE.
[25] Cheng-Fu Chou & Kwang-Ting Chuang. (2005) “Colanet: A cross-layer design of energy-efficient wireless sensor networks,” In 2005 Systems Communications (ICW’05, ICHSN’05, ICMCS’05, SENET’05), pp. 364–369. IEEE.
[26] Lemia Louail& Violeta Felea. (2016) “Routing-aware time slot allocation heuristics in contentionfree sensor networks,” In Wired/Wireless Internet Communications: 14th IFIP WG 6.2 International Conference, WWIC 2016, pp. 271–283. Springer.
[27] Lemia Louail& Violeta Felea. (2016) “Latency optimization through routing-aware time scheduling protocols for wireless sensor networks,” Computers & Electrical Engineering, Vol. 56, pp. 418–440.[28] LemiaLouail. (2016) “Approches cross-layer pour l’optimisation de la latence des communications dans les réseaux de capteurs sans fil,” PhD thesis, Université de Franche-Comté.
[29] Islam Amine Bouchedjera&LemiaLouail. (2020) “Latency and energy-efficient routing-aware TDMA for wireless sensor networks,” International Journal of Informatics and Applied Mathematics, Vol. 3, No. 1, pp. 22–38.
[30] Raid Boudi, ZiboudaAliouat, &Chirihane Gherbi. (2022) “TDMA-CADH cross-layer approach for IoT performance aspects,” In 2022 2nd International Conference on New Technologies of Information and Communication (NTIC), pp. 1–5.
[31] ALAUTHMAN, Almamoon et NIK, Wan NorShuhadah Wan. ANovel CLUSTER HEAD SELECTION ALGORITHM TO MAXIMIZE WIRELESS SENSOR NETWORK LIFESPAN.
[32] Wendi Rabiner Heinzelman, Anantha Chandrakasan, & Hari Balakrishnan. (2000) “Energy-efficient communication protocol for wireless microsensor networks,” In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, pp. 10. IEEE.
AUTHORS
Raid BOUDI achieved his Master’s degree in Network and Distributed Systems from the University of Ferhat Abbas Setif-1, Algeria, in 2020. Currently, he is pursuing his Ph.D. in Computer Science at Abdelhafid BOUSSOUF University, Center of Mila, Algeria. His research interests primarily focus on Network Analysis, Wireless Sensor Networks (WSN), Internet of Things (IoT), and Software-Defined Networking (SDN), aiming to advance the performance and adaptability of next-generation networked systems.
Chirihane Gherbi obtained her PhD in Computer Science from Larbi Ben Mhidi University, OEB, Algeria, in 2017. She is currently an associate professor at the College of Science, Computer Science Department, Ferhat Abbas University, and a member of the Network and Distributed Systems Laboratory (LRSD). Her principal areas of interest in research are wireless sensor networks (WSN), routing protocols in wireless communication, fault tolerance, security in the Internet of Things (IoT), and machine learning.
Zibouda Aliouat obtained her engineer diploma in 1984 and MSc in 1993 from Constantine University. She received her PhD from Setif 1 University of Algeria. She was an assistant professor at Constantine University from 1985 to 1994. Currently, she is a professor in Computer Engineering Department at Setif 1 University of Algeria. Her research interests are in the areas of computer networks and communication modeling and simulation, wireless sensor networks (WSN), fault tolerance of embedded systems and security and privacy in the Internet of Things (IoT), Internet of vehicles (IoV), and Nanonetworks communication. Specifically, it focused on clustering routing protocols in wireless communication and MAC layer.