IJCNC 06
ROUTING PERFORMANCES IN WIRELESS SENSOR
NETWORKS: DETERMINING SHORTEST PATH
ALGORITHMS EFFECTIVENESS
Khine Thazin Min1 and N. Jeyanthi2
1Faculty of Computer System & Technology, Myanmar Institute of Information Technology (MIIT), Mandalay, Myanmar
2 School of Computer Science Engineering and Information Systems,
Vellore Institute of Technology, Vellore, India
ABSTRACT
Wireless Sensor Networks (WSNs) play a pivotal role in a myriad of diverse fields, ranging from crucial healthcare applications to the creation of smart cities and effective environmental monitoring systems. Within the realm of WSNs, the feature of efficient routing assumes paramount importance as it exerts a profound influence on resource utilization and the overall performance of the network. In light of their remarkable efficiency and straightforwardness, shortest-path algorithms have emerged as a prevailing choice for routing mechanisms in WSNs. Hence, the primary objective of this specialized research is to understand a comprehensive investigation into the calculating performance of sensor network routing, with a particular circle on leveraging the potential of shortest-path algorithms. This ambitious effort will involve the establishment of a rigorous evaluation framework encompassing various performance metrics, enabling a meticulous assessment of the routing performance and the efficacy of the carefully selected algorithms. The culmination of this research holds tremendous significance, as it is poised to bestow invaluable insights into the practical implementation of WSNs. To attire with a comprehensive understanding of their performance across various scenarios and metrics, the research community can make informed decisions when choosing the most appropriate routing protocols suited to particular Wireless Sensor Network (WSN) deployments. The potential results of this research promise to not only improve the network’s efficiency, reliability, and lifespan safe but also to pave the way for innovative applications of Wireless Sensor Networks in critical areas of societal significance.
Keywords
Wireless Sensor Networks (WSNs), Routing Protocols, Shortest -path algorithms
- INTRODUCTION
Wireless Sensor Networks (WSNs) have gained significant attention in recent years due to their ability to collect data from the physical environment and facilitate various applications such as environmental monitoring, surveillance, and industrial automation. In Wireless Sensor Networks (WSNs), sensor nodes are deployed in a distributed trend to collect and transmit data wirelessly. Effective routing is crucial for promising the reliable and timely delivery of data within wireless sensor networks.
In WSNs, routing protocols are essential in deciding the route that data packets should follow from source to destination. Shortest-path algorithms have become one of the most popular routing techniques because they are straightforward and efficient in determining the shortest distance between nodes. These algorithms attempt to maximize resource consumption while Minimizing the cost metric, such as hop count or distance. The goal of what is being done is to examine how well shortest-path algorithms in WSNs execute calculations for routing in sensor networks. Insightful recommendations for the choice and improvement of routing protocols in WSNs can be complete.
Objectives
a) To study and evaluate the existing studies on routing protocols, calculation performance,
and wireless sensor networks (WSNs).
b) To understand why shortest direct path algorithm is important.
c) To establish and track performance measures, such as packet loss, throughput and end
then delay, in order determine routing performance.
d) To conduct experiments and collect data to evaluate the computational capabilities of the
specified shortest-path algorithm (Bellman-Ford) in Wireless Sensor Networks (WSNs).
e) To compare and study the effectiveness and efficiency of different routing protocols
regarding their impact on the overall performance of the network.
f) To offer suggestions and insights based on the examination of computation performances
for choosing and improving routing protocols in WSNs
Scope
The scope of this research includes the following key points:
- Comparisons of various performances such as throughput, end-to-end delay, packet loss of DSR, DSDV, AODV routing protocols some of which usages shortest path algorithm in relation to the data from the generated trace files.
- A simulation examining how different routing protocols affect the Quality of Service (QoS) in Wireless Sensor Networks (WSNs).
2.RESEARCH BACKGROUND
2.1. Wireless Sensor Networks
Figure 1. Architecture of a Wireless Sensor Networks
A Wireless Sensor Network (WSN) is a specialized of ad hoc network composed of numerous small, autonomous, and resource-limited in wireless sensor nodes that work together to monitor physical or environmental conditions in the base station. These sensor nodes are displayed with various sensors to gather data on parameters such as temperature, humidity, pressure, light, and other environmental factors. The nodes communicate wirelessly among themselves, forming a self-organizing network that allows data to be relayed to a main base station or sink node. WSNs are exploited in a wide range of applications, including environmental monitoring, agriculture, healthcare, industrial automation, surveillance, and disaster management. Due to their low-power design and ability to operate in exciting environments, WSNs offer benefits such as cost effectiveness, scalability, and real-time data collection. However, their resource constraints and wireless nature pose challenges in terms of energy efficiency, network scalability, data reliability, and security. To address these challenges, researchers and engineers are continuously exploring novel algorithms, protocols, and energy-efficient techniques to enhance the performance and extend the lifespan of Wireless Sensor Networks, making them a vital component in the realm of the Internet of Things (IoT) and smart applications.
Table 1. Shortest Path Algorithms in WSN
2.2. Shortest Path Algorithms
Shortest Path Algorithms are vital in Wireless Sensor Networks (WSNs) because they are key to efficient and reliable data routing. Within WSNs, these algorithms are used to identify the best paths for transmitting data from source nodes to destination nodes, taking into account factors such as connection quality, energy consumption, and network congestion. One widely used algorithm for finding shortest paths in WSNs is Bellman-Ford algorithm.
The Bellman-Ford algorithm is a distance-vector routing protocol applied in Wireless Sensor Networks (WSNs). Bellman-Ford does not require a complete network topology but relies on iterative updates to the distance vectors. Each node maintains its distance vector and exchanges it with its immediate neighbors. The algorithm then iteratively updates the distance vectors until convergence. Bellman-Ford is more suitable for dynamic networks or scenarios where maintaining a complete network view is impractical.
This algorithm plays a critical role in ensuring efficient data routing in WSNs. It enables the nodes to determine the best paths for transmitting data packets, optimizing energy consumption, reducing latency, and enhancing network reliability. As WSNs often operate in resource constrained environments, the choice of the appropriate shortest path algorithm becomes vital to maximize network performance and ensure the longevity of sensor nodes. The current research and optimization of these algorithms enhance the development of Wireless Sensor Networks (WSNs), procedure them reliable and adaptable solutions for various applications, including environmental monitoring, smart agriculture, healthcare, and industrial automation.
3.ROUTING PERFORMANCES IN WIRELESS SENSOR NETWORKS
Data transmission in sensor networks employs two techniques: Flooding and gossiping protocols. Flooding involves broadcasting data packets to all neighbors until they reach their destination or reach the maximum hop limit. Flooding is easy to implement but can lead to resource wastage and overlapping.
Gossiping protocol, a more advanced version of flooding, randomly selects a neighbor to transmit
data and continues this process. Unlike flooding, it avoids implosion issues but introduces delays.
Routing protocols fall into various categories, as shown in a Figure 2.
Figure 2. The Categories of Routing Protocols
3.1. Routing Discovery
Routing protocols are critical in Wireless Sensor Networks (WSNs) because they rule how data is transmitted from source nodes to destination nodes within the network. With resource constrained and energy-limited nodes in WSNs, efficient routing is crucial for optimal performance and network longevity. These protocols can be broadly categorized into Proactive (table-driven) and Reactive (on-demand) types.
Both proactive and reactive protocols have unique advantages and are chosen based on specific WSN requirements. The choice of routing protocol and shortest path algorithm significantly impacts network performance, energy efficiency, and scalability. Efficient routing protocols in WSNs are vital for reliable data transmission and enable applications like environmental monitoring, smart healthcare, and industrial automation, enhancing the overall usability and effectiveness of WSNs.
3.1.1. Proactive Routing
Proactive routing protocols maintain current routing information at all areas by continuously updating routing tables as the network topology changes. This constant maintenance allows for faster data forwarding, making them suitable for applications requiring low-latency communication. Examples of proactive routing protocols include Optimized-Link State Routing (OLSR) and Destination-Sequenced Distance Vector (DSDV).
3.1.2. Reactive Routing
Reactive routing protocols do not maintain routing information proactively but as an alternate establish routes on-demand when a data packet needs to be transmitted. This reduces control overhead and conserves energy in the network. Ad-hoc On-Demand Distance Vector (AODV) is a popular reactive protocol used in WSNs. Reactive protocols, including AODV, employ shortest path algorithms like Bellman-Ford to determine the best paths when needed.
Figure 3. Types and Classifications of Routing Protocols
3.1.3. DSDV (Destination-Sequenced Distance Vector)
DSDV is a proactive (table-driven) routing protocol in which each node maintains a routing table containing information about the shortest paths to all other nodes in the network. These tables are updated either periodically or whenever a network topology change occurs. DSDV is useful for static or slowly changing network topologies.
Example: Suppose a WSN is deployed for monitoring environmental parameters in a remote forest. The nodes in this scenario may not move frequently, making DSDV an appropriate choice for maintaining stable routes.
Table 2. Wireless Sensor Networks in practice
3.1.4. AODV (Ad-hoc On-Demand Distance Vector)
AODV is a reactive (on-demand) routing protocol that establishes routes only when needed. It discovers paths using route request (RREQ) packets and route reply (RREP) packets. AODV is more suitable for dynamic networks, as it minimizes control overhead and conserves energy.
Example: In a mobile WSN for monitoring wildlife, where the sensor nodes frequently change
positions, AODV can efficiently establish and maintain routes as the nodes move.
3.1.5. DSR (Dynamic Source Routing)
DSR is also a reactive protocol that utilizes source routing. When a node wants to transmit data, it includes the entire route in the packet header. In between nodes are required to forward packets only based on the route specified within them. DSR is flexible and works well in dynamic environments.
Example: DSR can be applied in a Wireless Sensor Networks (WSNs) used for surveillance in a crowded event. The nodes need to adapt quickly to changing routes as people move through the part.
3.1.6. Flooding Technique
Flooding in wireless sensor networks is a communication technique where a message is broadcast from one sensor node to all other nodes in the network. While it ensures message delivery to all nodes, it comes with significant drawbacks like redundancy, increased energy consumption, and scalability challenges.
For example, consider a forest monitoring system where sensor nodes need to alert all others about a detected fire. Flooding entails each sensor node broadcasting the fire alert to all of its neighbors who then relay the message to their neighbours, continuing this process until all nodes have been informed. While effective in ensuring everyone knows about the fire, it results in excessive communication, leading to quicker depletion of sensor node batteries and network congestion.
3.2. Bellman Ford Algorithm
Even when a weighted graph has edges with negative weights, Bellman-Ford is a single source shortest path algorithm that determines the shortest path between a given source vertex and every other vertex in a network. In 1958, Lester Ford and Richard Bellman presented it. Both directed and undirected graphs can be efficiently processed using the approach. As a single source shortest path algorithm, Bellman-Ford’s approach determines the shortest path from one source node to every other node in a directed weighted network.
The network’s weights may even be negative figures. It employs a dynamic programming methodology in which all potential solutions are evaluated before the best one is chosen. In the following algorithm, all the edges of the networks are relaxed 𝑛 − 1 times, where n is the number of nodes, and the distance of each edge is calculated in every repetition. Bellman-Ford is useful for negative weight scenarios, like traffic delays. It can’t handle negative cycles. It has O(V*E) time difficulty, less efficient than Dijkstra’s. Still, it’s vital in network routing, traffic engineering, and transportation systems due to its dynamic programming and versatility.
Figure 4. Flow Chart of Bellman- Ford Algorithm
3.3. Dijkastra Algorithm
Dijkstra’s algorithm, named after its inventor Edger W. Dijkstra’s an algorithm for the shortest paths between nodes in a weighted graph. The algorithm is commonly employed in applications like network routing, maps, and transportation systems.
Here’s a brief overview of how Dijkstra’s algorithm works:
Initialization– Start by selecting a source node and set its distance from itself to 0, while all other nodes are initially marked with infinity. You also maintain a list of unvisited nodes, initially containing all nodes in the graph.
Exploration- involves repeatedly selecting the unvisited node with the smallest known distance (from the source node) and marking it as visited.
Update Distances- For the selected node, compute the distance to its unvisited neighbors through the currently explored path. If the newly calculated distance is shorter than the previously known distance, update the distance value accordingly.
Repeat- Continue the process of selecting the unvisited node with the smallest distance and updating distances until you have visited all nodes or until the target node is reached.
Optimal Path Reconstruction- involves reconstructing the shortest path from the source to the target by backtracking from the target node to the source node using the stored information about the optimal path once all nodes have been visited or you have reached the target node. Dijkstra’s algorithm guarantees the shortest path when all edge weights are non-negative; however, it may not work correctly when negative edge weights are present in the graph, in which case you might need to use other algorithms like the Bellman-Ford algorithm.
4.EXPERIMENTAL SYSTEM AND RESULT DISCUSSION
NS2 (Network Simulator 2) is a widely used open-source network simulation tool that allows researchers and network engineers to simulate and examine various network protocols and scenarios. It is commonly used for academic research, performance evaluation, and protocol development in the field of computer networking. It enables researchers and network engineers to study various networking scenarios and protocols and gain valuable insights into network performance and behavior.
4.1. Generating NAM Files and Trace Files
Once NS2 is set up and running on our PC, we can use it to simulate network scenarios and generate trace files. Nam is a network animator that helps visualize the simulation results in a graphical form.
To generate a Nam file and various trace files for energy consumption, throughput, and end-toend delay, we need to modify a TCL script to define your network, nodes, protocols, and parameters.
Run the simulation with NS2, generating trace files for energy, throughput, and delay. Analyze results using Nam to visualize the network and study trace files for metrics.
4.2. Comparison Of Routing Protocols In Wsns
A detailed comparison of WSN routing protocols is given below in tabular form: Table 3 and 4
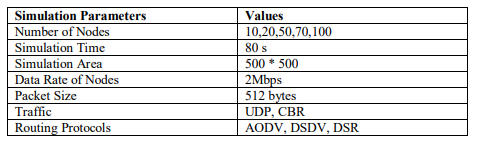
Table.3. Simulation Parameters for Mobile Nodes
Table.4. Simulation Parameters for Fixed Nodes
4.3. Routing Metrics
- Minimum hop: Minimize total cost of data propagation and low end to end delay
- Energy: energy consumed per packet , total reserved energy
- Quality of service: latency(delay), throughput, packet loss, jitter, error rate
- Robustness: link quality, link stability
4.4. Performance Analysis of Routing Protocols
For our simulation, we will be concentrating on Quality of service (QOS) where end-to end Delay measures the time it takes for a packet to travel from the source node to the destination node. It is calculated by subtracting the time the packet was sent from the time it was received at the destination as shown in fig 5.
Network Throughput metric represents the rate at which data packets are successfully delivered from the source to the destination in the network. It’s typically measured in bits per second (bps) or packets per second (pps). To calculate in the network throughput, you can divide the total amount of data successfully transmitted over a specific time period by that time period’s duration.
Packet Loss Rate metric quantifies the percentage of data packets that do not successfully reach
their destination. To calculate the packet loss rate, divide the number of lost packets by the total
number of packets sent.
Figure 5. Simulation Model
5.RESULTS AND ANALYSIS
After running the simulations for the network with parameters details in table.1, the following results is obtained.
5.1. Mobile Nodes – End To End Delay
The end to end delay results as shown in Table 5.
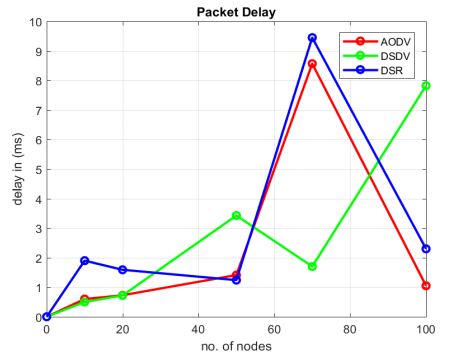
Table.5 . End to End Delay
Figure.6 . Average End to End Delay
AODV performs well with low delay in smaller networks but experiences increased delay as the network size grows, indicating potential routing overhead and congestion issues, as shown in figure 6.DSDV tends to perform well with low delay in smaller networks but experiences increased delay in larger networks due to control packet overhead. The delay may vary as the protocol adapts to network conditions.
DSR routing protocol appears to perform moderately well with low to moderate delay in smaller networks. However, as the network size grows beyond a certain point, “There is a significant rise in average delay.” suggesting potential issues with scalability and congestion management in the network.
5.2. Mobile Nodes – Throughput
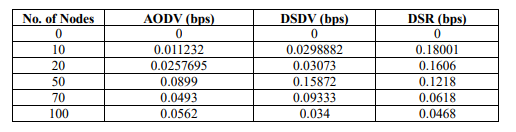
AODV routing protocol demonstrates efficient data transfer with high throughput in smaller networks as shown in table 6.
Table.6 . Throughput
Figure.7 . Average Throughput
“Although there is a reduction in throughput when the network reaches 50 nodes, AODV seems to adapt and sustain stable throughput as the network continues to grow” as shown in figure 7. This suggests reasonable scalability and performance in larger networks.
DSDV routing protocol demonstrates moderate data transfer efficiency in smaller networks. While “there’s been a rise in throughput “at 50 nodes, it appears that DSDV may encounter issues with scalability and stability as the network size further increases.
DSR routing protocol initially demonstrates efficient data transfer with high throughput in smaller and moderately sized networks. However, as the network size increases, “there has been a marked reduction in the average” throughput, likely due to congestion and resource contention. While DSR maintains some degree of stability in larger networks, achieving high throughput becomes more challenging.
5.3. Mobile Nodes – Packet Loss Rate
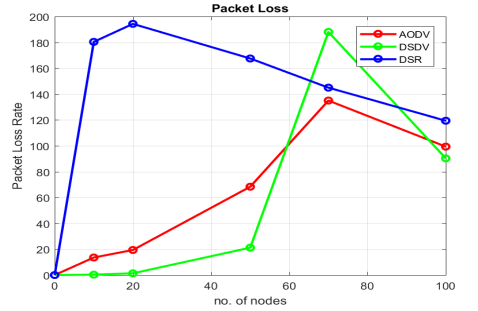
The packet loss rate results as shown in Table.7 and Figure.8
Table.7 . Packet Loss Rate
Figure.8 . Packet Loss
AODV routing protocol initially exhibits good packet delivery with a low packet loss rate in smaller and moderately sized networks. However, as the network size grows beyond a certain point “there is a clear increase” in the average packet loss rate. This behavior suggests that AODV may face scalability challenges and increased packet loss in larger networks.
DSDV routing protocol demonstrates good packet delivery with a low packet loss rate in smaller and moderately sized networks. This behavior suggests that DSDV may face scalability challenges and increased packet loss in larger networks.
DSR routing protocol initially exhibits challenges with high packet loss rates in smaller and moderately sized networks. However, it shows an unexpected improvement in packet delivery at 50 nodes, which is maintained in larger networks. This behavior suggests that DSR may adapt to network conditions and perform reasonably well in larger networks.
5.3. Fixed Nodes
After running the simulations for the network with parameters discussed in table.4, the following results is obtained in table 5 and as shown in figure.9.
Table. 5 . Fixed Node Simulation Results
Figure:9 . Fixed Node Simulation Results
AODV appears to establish a balance between Average, Throughput and Packet Delivery Ratio, making it a robust routing protocol for wireless sensor networks. Its effectiveness can be attributed to the use of the Bellman-Ford Shortest Path Algorithm, which helps in calculating efficient routes on-demand, thereby optimizing data delivery.
DSR demonstrates a higher data transfer rate, but its slightly lower PDR suggests that it might experience occasional packet losses. However, DSR’s adaptability to changing network conditions and source routing approach can contribute to its performance.
In summary, AODV, with the assistance of the Bellman-Ford Shortest Path Algorithm, appears to offer a well-balanced performance in terms of data throughput and packet delivery in wireless sensor networks. DSR, while showing better data transfer rates, may require further optimization for packet delivery reliability.
In terms of Residual Energy
AODV exhibits the highest residual energy levels, indicating good energy efficiency and longer node lifetimes. DSDV follows closely behind AODV in terms of residual energy, suggesting stable energy consumption. DSR lags in terms of residual energy, with some nodes having considerably lower energy levels, potentially impacting its overall network performance. AODV and DSDV appear to be more energy-efficient and suitable for maintaining network connectivity over an extended period, while DSR may require additional energy management strategies to ensure network longevity and reliability. Selecting a routing protocol should consider the specific requirements and limitations of the wireless sensor network.
6.CONCLUSIONS
The results have provided an in-depth analysis of routing protocols, specifically AODV, DSDV, and DSR, in the dynamic realm of wireless sensor networks. These routing protocols are the backbone of data routing, ensuring efficient communication within these networks.
One pivotal aspect that emerged from our study is the utilization of the Bellman-Ford algorithm within the DSDV protocol. This algorithm is instrumental in determining the shortest path between nodes in the network The implication of this approach lies in its ability to effectively handle various graph scenarios, particularly those with negative edge weights.
The Bellman-Ford algorithm, employed by DSDV, calculates the shortest path based on hop counts or other metrics. This results in highly efficient routing decisions, conserving energy and resources in resource-constrained wireless sensor networks. The algorithm incorporates sequence numbers, a crucial feature for preventing routing loops. This enhances the reliability of the routing protocol, particularly in dynamic and ever-changing network topologies. Shortest path algorithms like Bellman-Ford offer deterministic route calculation, ensuring consistent When discussing routing results across nodes. This predictability is advantageous for application developers and network administrators.
The research also observed that the shortest path algorithms have certain limitations. While effective, maintaining routing tables and periodic updates can introduce overhead, especially in networks with rapidly changing topologies. This overhead can consume valuable network resources. Shortest path algorithms may face scalability challenges in large and highly dynamic networks. As the network size increases, the computational complexity of calculating and maintaining routes also grows. Shortest path algorithms, while striving for optimality, may not always account for real-time factors or network conditions. This can lead to increased end-to- end delay, particularly in scenarios with high traffic loads.
7.SUMMARY
This research has provided valuable insights into the behaviour of these routing protocols. Under different conditions and network sizes This emphasizes the critical importance of selecting the most appropriate routing strategy to suit the specific needs of wireless sensor networks.
In summary, my study contributes significant insights into routing protocol performance within wireless sensor networks. The combination of the Bellman-Ford algorithm in DSDV emphasizes the importance of optimized routing decisions for efficient data delivery. While shortest path algorithms offer advantages such as optimized routing and loop prevention, they also present challenges related to overhead, scalability, and latency. These findings are pivotal for network designers, researchers, and practitioners aiming to design and deploy efficient routing protocols in the dynamic landscape of wireless sensor networks.
8.FURTHER RESEARCH
Future research endeavors should focus happening attractive routing protocols to address scalability concerns, reduce overhead, and adapt to dynamic network conditions. Additionally, investigating hybrid routing approaches that combine the strengths of different protocols, including those employing shortest path algorithms, can further optimize routing performance.
ACKNOWLEDGEMENTS
We would like to express our heartfelt gratitude to School of Computer Science Engineering and Information Systems, Vellore Institute of Technology, ASEAN-India Research Training Fellowship scheme of the Department of Science and Technology, Government of India, in collaboration with the Federation of Indian Chambers of Commerce and Industry.
REFERENCES
[1]. Sharma, Shweta, and Tarun Kumar. “Energy Efficient Modified Cluster Routing Algorithm for Maximizing Stability Period of WSN.” International Journal of Innovative Research in Computer and Communication Engineering 3, no. 9 (2015).
[2]. Jayadharshini, P., T. Abirami, S. Santhiya, N. Bhavatharini, and G. Rithanya. “Energy efficient wireless sensors architecture with LSTM based on Machine Learning Technique.” In Intelligent Wireless Sensor Networks and the Internet of Things, pp. 107-125. CRC Press, 2024.
[3]. Hussein, Wael Ali, Borhanuddin M. Ali, M. F. A. Rasid, and Fazirulhisyam Hashim. “Smart geographical routing protocol achieving high QoS and energy efficiency based for wireless multimedia sensor networks.” Egyptian Informatics Journal 23, no. 2 (2022): 225-238.
[4]. Sinduja, M. S., K. R. Rekha, and Raghavendra Manjegowda. “Wireless Sensor Networks: A Methodical Analysis.” In ICDSMLA 2020: Proceedings of the 2nd International Conference on Data Science, Machine Learning and Applications, pp. 1355-1367. Springer Singapore, 2022.
[5]. Sinduja, M. S., K. R. Rekha, and Raghavendra Manjegowda. “Wireless Sensor Networks: A Methodical Analysis.” In ICDSMLA 2020: Proceedings of the 2nd International Conference on Data Science, Machine Learning and Applications, pp. 1355-1367. Springer Singapore, 2022.
[6]. Jayadharshini, P., T. Abirami, S. Santhiya, N. Bhavatharini, and G. Rithanya. “Energy efficient wireless sensors architecture with LSTM based on Machine Learning Technique.” In Intelligent Wireless Sensor Networks and the Internet of Things, pp. 107-125. CRC Press, 2024.
[7]. Yang, Xiaoping, Mengjie Li, Zhihong Qian, and Te Di. “Improvement of GPSR protocol in vehicular ad hoc network.” IEEE Access 6 (2018): 39515-39524.
[8]. Oreku, George S., and Tamara Pazynyuk. Security in wireless sensor networks. Cham, Switzerland: Springer International Publishing, 2016.
[9]. Patel, Nileshkumar R., and Shishir Kumar. “Wireless sensor networks’ challenges and future prospects.” In 2018 International Conference on System Modeling & Advancement in Research Trends (SMART), pp. 60-65. IEEE, 2018.
[10]. Gong, Yadong. “Network-structure-based energy aware routing in wireless sensor networks.” In 2019 IEEE 4th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), pp. 1602-1605. IEEE, 2019.
[11]. Yang, Xiaoping, Mengjie Li, Zhihong Qian, and Te Di. “Improvement of GPSR protocol in vehicular ad hoc network.” IEEE Access 6 (2018): 39515-39524.
[12]. Kandaswamy, Partheepan, James A. Flint, and Vassilios A. Chouliaras. “System on fabrics architecture using distributed computing.” IEEE Sensors Journal 18, no. 14 (2018): 5929-5936.
[13]. Kocher, Idrees S. “A systematical roadmap on various security vulnerabilities and countermeasures in routing algorithms upon wsns.” Academic Journal of Nawroz University (AJNU) 10, no. 4 (2021).
[14]. Aparicio, Joaquín, and Sverre Holm. “Obtaining range measurements from ambient noise crosscorrelations for the self-calibration of nodes.” In CEUR Workshop Proceedings. Technical University of Aachen, 2021.
[15]. Rajani, J., and P. Sriramya. “Artificial neural networks are compared to K-nearest Neighbors in a novel swarm optimization for smart waste management systems employing automated machine learning.” Journal of Survey in Fisheries Sciences 10, no. 1S (2023): 1998-2007.
[16]. Casares-Giner, Vicente, Tatiana Inés Navas, Dolly Smith Flórez, and Tito Raúl Vargas Hernández. “End to end delay and energy consumption in a two tier cluster hierarchical wireless sensor networks.” Information 10, no. 4 (2019): 135.
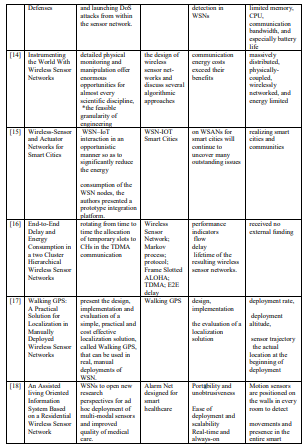
[17]. Stoleru, Radu, Tian He, and John A. Stankovic. “Walking GPS: A practical solution for localization in manually deployed wireless sensor networks.” In 29th annual IEEE international conference on local computer networks, pp. 480-489. IEEE, 2004. International Journal of Computer Networks & Communications (IJCNC) vol 16, No 6, November 2024 106
[18]. Baghezza, Rani, Kévin Bouchard, Abdenour Bouzouane, and Charles Gouin-Vallerand. “From offline to real-time distributed activity recognition in wireless sensor networks for healthcare: A review.” Sensors 21, no. 8 (2021): 2786.
[19]. Whitehouse, Kamin, Chris Karlof, Alec Woo, Fred Jiang, and David Culler. “The effects of ranging noise on multihop localization: an empirical study.” In IPSN 2005. Fourth International Symposium on Information Processing in Sensor Networks, 2005., pp. 73-80. IEEE, 2005.
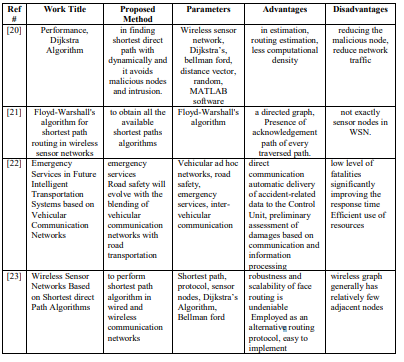
[20]. Goyal, Monika, Vinit Kumar, and Anu Dahiya. “Performance Measurement of Wireless Sensor Network using Dijkstra Algorithm.” International Journal of Computer Science & Management Studies 18, no. 1 (2015).
[21]. Khan, Pritam, Gargi Konar, and Niladri Chakraborty. “Modification of Floyd-Warshall’s algorithm for Shortest Path routing in wireless sensor networks.” In 2014 Annual IEEE India Conference (INDICON), pp. 1-6. IEEE, 2014.
[22]. Gebre, Tewodros Syum, and Leila Hashemi-Beni. “An Integrated Framework of GPT-4 and PINN for Dynamic Traffic Estimation and Support.” In IGARSS 2024-2024 IEEE International Geoscience and Remote Sensing Symposium, pp. 5457-5460. IEEE, 2024.
[23]. Zainlabuddin, M. D., and Neeraj Sharma. “Security Enhancement in Data Propagation for Wireless Network.” REVISTA GEINTEC-GESTAO INOVACAO E TECNOLOGIAS 11, no. 4 (2021): 3110- 3119.
[24]. Jing, Qi. “Searching for economic effects of user specified events based on topic modelling and event reference.” PhD diss., Acadia University, 2014.
[25]. Fotache, Vasile, and Dan Alexandru Stoichescu. “Implementation of Dijkstra and Floyd-Warshall Algorithms in Dynamic Dimensioning and 3D Geospatial Positioning Wireless Sensor Networks.” In 2023 International Symposium on Fundamentals of Electrical Engineering (ISFEE), pp. 1-5. IEEE, 2023.
AUTHORS

Ms. Khaing Thazin Min, in Myanmar University of Information Technology. Mandalay City. She is a Lecturer working in the Faculty of Computer Systems and Technology. Her received a master’s degree in Computer Technology from Computer University (Mandalay) in 2012. In addition, she attended teaching support courses run by the university. Her current areas of interest include Wireless Sensor Networks (WSN), Blockchain, IOT and Network Security. She is currently attending the ASEANIndia Research Training Fellowships (6months) Program in VIT.

Dr. N. Jeyanthi, Professor in VIT, Vellore for School of Computer Science Engineering and Information Sciences, received her PhD in Cloud Security from VIT, Vellore. Her research work was funded by Department of Science and Technology, Govt. of India. She has authored and co-authored over 70 research publications in peerreviewed reputed journals and 40 conference proceedings. She edited books for Springer, Taylor & Francis and IGI. Book chapters were also added to her research contribution. She has served as the program committee member of various international conferences and reviewer for various international journals. She has been honoured by VIT as an active researcher for five consecutive years. Her accomplishments have earned her the Dr.A P J Abdul Kalam, Best Teacher and Researcher Award for 2022. Her current areas of interest include Quantum Cryptography, Information Security, IoT, Cloud, and Big Data security.