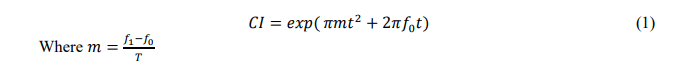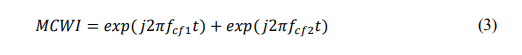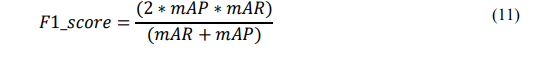IJCNC 02
Radio Frequency Interference Detection and Automatic Modulation Recognition Based on Mask RCNN
Noureddine El-haryqy, Zhour Madini, Younes Zouine
Department Electrical and Telecommunication, Laboratory of Advanced Systems
Engineering (ISA), National School of Applied Sciences (ENSA), Ibn Tofail University,
Kenitra, 14000, Morocco
ABSTRACT
The increasing complexity of wireless communication conditions presents noteworthy obstacles to the adaptability and flexibility of cognitive radio systems. The latter can alleviate the problem of spectrum shortages through proper spectrum management. However, cognitive radio has difficulty distinguishing between signals of interest and interference, which can be a general enemy since it is undesirable because it influences the signal’s quality. Efficient detection and characterization of interference in wireless communication networks is critical for ensuring strong security. However, in this research, we use the Mask R-CNN methodology to present a new concept for automatic modulation recognition and radio frequency interference detection. Moreover, this algorithm can segment, detect, and recognize several types of interference that can affect wireless communication systems, such as chirp interference (CI), continuous wave interference (CWI), and multiple continuous wave interference (MCWI) within the signal of the interest (SOI), as well as the modulation kind present in the SoI. Overall, the combination of these distinct techniques can be very valuable in the field of signal processing, especially in anti-jamming strategies in wireless networks. Moreover, the proposed approach showcases exceptional performance in
the validation dataset. For radio frequency interference detection, it achieves a mean average precision (mAP) of 0.946 and a mean average recall (mAR) of 0.954. For automatic modulation recognition, it attains a mAP of 0.898 and a mAR of 0.916.
KEYWORDS
cognitive radio, deep learning, Mask R-CNN, instance segmentation, automatic modulation recognition, radio frequency interference detection
1. INTRODUCTION
The utilization of available radio frequency spectrum can be used intelligently and adaptably thank to cognitive radio (CR), a wireless communication technique. Cognitive radio seeks to increasethe efficiency and usage of the limited RF spectrum by allowing devices to change their transmission settings based on real-time spectrum sensing and evaluation[1]. It is predicated on the idea that the principal users (PUs) are the licensed spectrum owners who have unrestricted access to the spectrum. Unlicensed users who can opportunistically access the channel (spatially and temporally) without interfering with the PUs are referred to as secondary users (SUs). However, criminal investigations, military surveillance, threat evaluation, electronic countermeasures, and spectrum monitoring are among the many uses of cognitive radio [2],[3]. The numerous applications of cognitive radio technology demonstrate its importance in electronic warfare scenarios from a tactical and strategic viewpoint. In the field of electronic warfare, cognitive radio technology has two uses [4]. It can be employed as an intelligent jammer that can recognize and analyze adversary communication patterns to successfully thwart enemy attacks [5]. In contrast, a cognitive radio that has learned about the behavior of jammers may develop intricate anti-jamming strategies and anticipate and avoid jamming signals with great flexibility [6],[7].Interference is the term used to describe the presence of unwanted signals that disrupt or degrade the performance of a wireless communication system. There is interference between signals when they use the same spectral resources or frequency band, which has a huge impact on the effectiveness of wireless systems. In wireless communications, interference can take numerous forms and have different features, such as adjacent channel interference, selfinterference, co-channel interference, homogeneous technology interference, and heterogeneous technology interference [8]. Additionally, there are situations when intentional interference, which is malevolent interference done on purpose to stop or hinder communication, may occur. Several types of malicious interference exist, including Regular jammers, Delusive jammers, Random jammers, Responsive jammers, Go-next jammers[9].
The use of automatic modulation recognition (AMR) is essential in a variety of tasks, for example, electronic warfare, spectrum management, and spectrum sensing [10]. In this context, identifying the type of modulation utilized by the received signal is critical because it enables adaptive.Communication systems to adjust their parameters and configurations based on the recognized modulation, ensuring optimal signal reception and data demodulation. As wireless communication technologies advance, signal modulation schemes become more intricate and diverse in order to address the requirements of complex communication scenarios [11]. In this dynamic environment, the development of robust AMR models is critical, especially in the presence of interference and jammers. The difficulties posed by harsh radio environments highlight the critical need for adaptive and effective AMR solutions that are capable of accurately identifying modulation schemes under adversarial conditions. However, likelihood-based (LB) and feature-based (FB) approaches are used in classic modulation recognition; the first has a large latency and requires extensive prior knowledge, while the latter is computationally light [12]. Equally traditional interference detection methods include a number of methods, such as the method to suppress narrowband interference in the spread spectrum system [13], the method to suppress broadband noise interference based on time-frequency distributing in the spread spectrum system [14], etc. They do not allow for automatic interference-type identification. In general, traditional interference suppression strategies suffer from three major drawbacks: reliance on domain expertise and interference properties; lack of generalizability; and complexity caused by determining the exact location of the interference [8]. On the other hand, according to a number of recent studies, Deep Learning (DL) approaches have attracted interest and become an alluring replacement for traditional methods in the field of communications[15]. As a case study, consider the fields of spectrum sensing [16], channel modeling and prediction [17], channel estimation [18], signal demodulation [19], and so on. Expressing has proven to have good outcomes.
Despite the initial success of deep learning in image classification, its capabilities have evolvedsignificantly, extending beyond mere categorization. Object localization refines this process by focusing on precisely locating a single primary object. Object detection has emerged, which enables the identification and localization of multiple objects inside an image through bounding boxes. The field has reached new heights with instance segmentation, a sophisticated task that goes beyond detection by providing pixel-level segmentation for each individual object in an image. In semantic segmentation, every pixel in an image is categorized into predetermined groups without making a distinction between different occurrences of the same class. To highlight the unique characteristics of each recognition task, Figure 1 presents a thorough comparison of output from them all[20]. However, this transformation demonstrates the versatility of deep-learning models and their capacity to handle a wide range of challenging visual tasks. This progress has not only transformed the field of computer vision but has also opened up new paths for study and practical applications.
Moreover, numerous deep learning algorithms that were created for object detection have also been successfully applied to signal detection problems, generating impressive results [21], [22]. These algorithms have persuasively demonstrated their appropriateness for signal detection, identification, and characterization [23].However, to the best of our knowledge, there have been few studies on jointly performing radio interference detection and automatic modulation recognition. In addition, the existing methods do not localize interference signals in the signal of interest and recognize various interference shapes. Because this information helps to distinguish between non-intentional and intentional interferences, which are commonly referred to as jamming. Overcoming these obstacles is critical for anti-jamming and cognitive radio decisionmaking applications. However, by utilizing deep learning techniques, specifically object detection and instance segmentation, it is possible to address these limitations at the same time.
Figure 1. : Comparative Output Across Recognition Tasks: (a) Image Classification, (b) Object Bounding Box Localization, (c) Semantic Segmentation, and (d) Instance Segmentation [16].
In this study, Mask R-CNN is the chosen framework because it can detect objects and create precise segmentation masks. It can handle complex shapes, multiple objects, and fine details. It is flexible and can be used in different situations. It is easy to use and has been successful in many computer vision tasks. In this paper, we give a novel concept to radio frequency interference detection by treating Automatic Modulation Recognition (AMR) and Radio Frequency Interference (RFI) detection as both an object detection and segmentation task. Our proposed methodology demonstrates robust performance in addressing key challenges associated with AMR and RFI detection. Specifically, we focus on scenarios characterized by varying signal-tonoise ratios (SNR), modulation complexities, and interference patterns. However, this research sets itself apart from earlier studies by making distinctive and noteworthy contributions in the following ways:
- The classification of received signal types, as well as the segmentation of jamming signals
from the signals of interest. - The multi-label segmentation features of Mask R-CNN are used to simultaneously detect
multiple interference sources and recognize various interference shapes. - Automatic modulation recognition of various digital modulation methods in the presence of
jamming signals, is performed under varying SNR.
The paper is structured as follows: The second section examines previous studies on the topic. Section 3 discusses the proposed approach and the dataset used. Section 4 covers algorithm evaluation and implementation. In Section 5, the results are thoroughly examined. Section 6 contains an in-depth examination of the findings. Section 7 concludes by summarizing the key findings of the research and offering recommendations for future lines of research.
2. RELATED WORKS
With the explosive development of deep learning technology (DL), it has been widely used in the fields of radio frequency interference (RFI) detection and automatic modulation recognition (AMR). However, in this section, we review previous research on AMR and RFI detection in cognitive radio, which is directly related to our research. Various approaches have been developed on the subject of AMR. In the research [24], the authors proposed an RNN (recurrent neural network) for automatic Modulation Classification (AMC) that performs optimally over correlated non-Gaussian noise, white non-Gaussian noise, and white Gaussian noise circumstances. However, The authors of the study [25] presented a CNN model for AMC that performs well in Multipath fading channels. And even more, Fuxin Zhang et. al. [11] examined Deep Learning for AMR techniques in the study. In-depth comparisons were also offered, allowing professionals to assess the various models in light of their applications. As well as discussing the available dataset and looking at the characteristics of comparative models. However, to the best of our understanding, all of this research does not take into account the presence of interference as a parameter, it solely focuses on noise. Notably, interference and noise are two different factors that might affect wireless communication systems. RFI detection has been investigated in numerous studies using various methods. In order to differentiate the astronomical signal from the numerous, intricate RFI characteristics. A revolutionary method for reducing RFI signals in radio data was suggested by Joël Akeret et. al. [26], and it was based on U-Net. This method has been applied to the issue of image segmentation, where each pixel in an input image is given a class label. A set of features that were taken from the input time-ordered data (TOD) from a radio telescope were learned by this U-Net. Moreover, Oyedare et al. [8] performed a comprehensive analysis of various methodologies that utilize deep learning to address interference mitigation. This involves the direct extraction of interference attributes from data, eliminating the reliance on expert systems for the identification of key characteristics. The paper also includes a systematic taxonomy of wireless communication difficulties. The paper covers an extensive variety of strategies that use deep learning to minimize interference. The methods investigated encompass both supervised and unsupervised DL methodologies. On the other hand, The authors [22] combined the cyclostationary detector and the R-CNN (regionbased convolutional neural network ) for signal identification, detection, and characterization, demonstrating that it is powerful under the influence of additive white Gaussian noise (AWGN) and performs better than widely used network designs like AlexNet, GoogLeNet, and VGG 16. In this research [27], the authors present an automatic clutter and interference identification approach in range-doppler spectrum images produced by high-frequency surface wave radar (HFSWR) using Faster R-CNN. However ,the authors of the research [21] employ the FasterRCNN framework to locate and detect wireless RF signals of interest in frequency and time if undesired signals are generating RFI. They take Bluetooth and microwave oven signals into account as RFI and Wi-Fi signals that are of concern. For the multiuser automatic modulation categorization of compound signals, the authors of the research [28] suggested a new deep multilabel learning-based framework (MLAMC). Using the signals used to jam radar as an illustration. Three processingsteps are included in the proposed framework: the extraction of the timefrequency representation image (TFRI) for signal pre-processing, the construction of the multilabel convolutional neural network (MLCNN) for multi-label classification, and the multidecision threshold optimization for output label choice. The researchers in the article [29] studied two unsupervised machine learning algorithms for identifying radio frequency interference (RFI), the SVDD (the support vector data description) approach and the one-classsupport vector machine (SVM) approach, in order to identify abnormal interference signals. They were then compared using the CI, CWI, and MCWI interference signals. They concluded that One-Class SVM is outperformed by SVDD. With the same datasets, The authors of the research [30] used a DL-based approach leveraging transfer learning such as VGG-16, GoogleNet, ResNet-18, and AlexNet. In order to recognize the kind of received signals and the type of modulation utilized in those signals. And they showed that the performance of all the pre-trained
architectures is largely identical.
However, most studies have focused on AMR in the presence of signal-to-noise, with few studies addressing modulation recognition in the presence of jamming signals. Moreover, these studies have used classical classification approaches that require distinct classifiers or models for each type of interference, resulting in increased hardware requirements and computational costs. Additionally, these approaches do not give a deeper understanding of the types of interference required in the cognitive radio system to differentiate between intentional and malevolent interference. In our study, we address these limitations by using the Mask R-CNN algorithm, which allows us to recognize the modulation type of the received signal and detect the type of interference. This provides us with a deeper understanding of the jamming signal and enables us to recognize multiple jammers in the signal of interest with the type of modulation used in the received signal. By using Mask R-CNN, we can simultaneously detect and classify modulated signals and interference sources in radio frequency-based communication systems, without the need for separate models for each type of interference. This reduces hardware requirements and computational costs while improving the accuracy and efficiency of the system.
3. MATERIALS AND METHODS
3.1. System Model
This st udy presents a Deep Learning (DL) approach for radio frequency interference (RFI)detection and automatic modulation recognition (AMR) that takes advantage of object classification, detection, and segmentation strategies. We employ a scalogram dataset. This dataset provides a detailed time-frequency representation of signals, providing valuable insights into signal variations caused by different types of interference. The dataset was carefully labeled to distinguish between the signal of interest (SOI) or modulation kind of the received signal and various interference types, such as continuous wave interference (CWI), multi-continuous wave interference (MCWI), and chirp interference (CI). The Mask R-CNN architecture was used to train models for AMR as well as interference detection. The training process involved leveraging the labeled dataset to teach the models to accurately recognize and localize modulation types and interference patterns. The performance of the trained models was rigorously evaluated. Figure 2 shows an outline of the suggested framework. However, In the first phase of our research, we will only look at the signal of interest (SOI) and the type of interference without paying attention to the modulation utilized. These interferences are known as CWI, MCWI, and CI. Furthermore, in the second part, we will evaluate the suggested method in tree-type interference mixed with the signal of interest (SOI), where each signal of interest correlates to a known form of modulation such as 8 APSK, 16 APSK, 32 APSK, and QPSK.
Figure 2. Block diagram of the suggested AMR and radio interference detection framework.
3.2. Mathematical Descriptions of Signal Jammers
The three forms of interference that are especially addressed in this paper are chirp interference (CI), multi-continuous wave interference (MCWI), and continuous wave interference (CWI). The definition and mathematical representation of each type are as follows:
Chirp Interference (CI): A signal that fluctuates in frequency over time is known as a chirp signal. It can be produced by sweeping the frequency of a sinusoidal signal within a predetermined frequency range. In a wireless communication system, chirp signals that are unintentionally or unwelcomely present and interfere with the desired signals are referred to be CI. The mathematical equation (1) for it is as follows [30]:
IMWhere the signal sweeps from f0 to f1. such that T is the duration of the sweeping period.
Continuous Wave Interference (CWI): is a type of interference that disrupts or interferes with the desired communication signals in wireless communication systems. CWI refers to any narrowband signal that may be properly displayed in the form of sinusoids in the GNSS bands. Ican be produced intentionally by signal producers or jammers, unintentionally by unwanted emissions such as instrument landing system (ILS) harmonics, VHF TV and UHF, VHF omnidirectional radio range (VOR), or by any adjacent electronic equipment [31],[30].However, The CWI can be mathematically represented as follows:
Where 𝑡 and 𝑓𝑐𝑓 indicate the interference duration and center frequency, respectively.
Multi Continuous Wave Interference (MCWI): refers to the interference that arises from several continuous wave transmissions interfering with a wireless communication system at the same time. These interfering signals can also have varied frequencies and power levels, and each interference can be characterized by continuous waveforms as shown by the equation (3).
Where 𝑓𝑐𝑓1and 𝑓𝑐𝑓2 are the center frequencies of each wave.
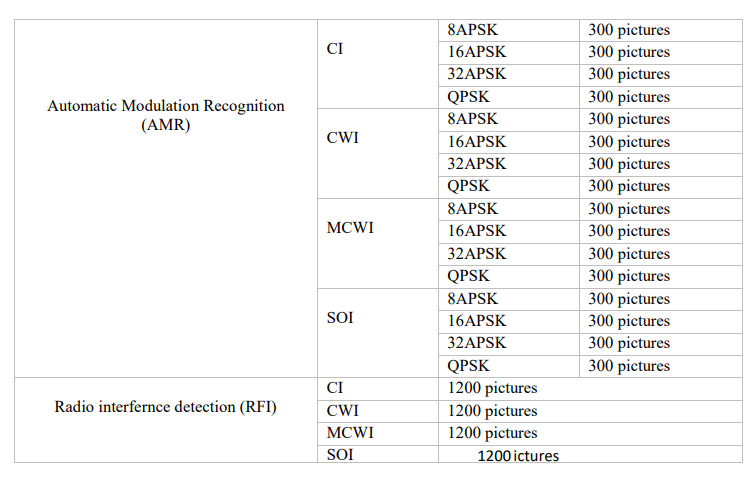
3.3. Datasets
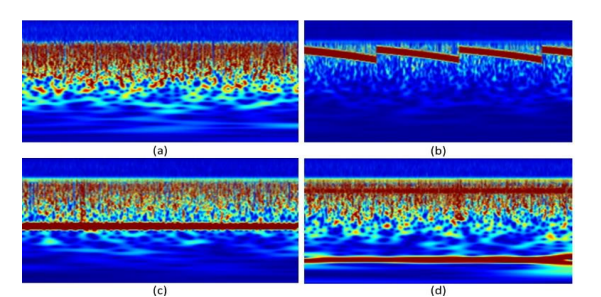
This dataset [30] comprises the scalogram of RFI signals for RFI classification and Modulation recognition applications. SoI is a video stream that is sent using DVB-S2 standards in real-time satellite-to-ground communication. CWI is formed by combining Continuous Wave Interference (CWI) and SOI. MCWI is an abbreviation for Multi-CWI and SoI combined, whereas CI is an abbreviation for SoI mixed with Chirp Interference. Furthermore, SoI has been transmitted utilizing QPSK, 8APSK, 16APSK, and 32APSK modulation patterns, among others. Signal-tonoise ratio (SNR) conditions for the dataset ranged from 5 to 12 dB. Examples of the various scalogram images are displayed in Figure 3. Table 1 displays all dataset characteristics.
Figure 3. Examples of datasets used in this work are as follows: (a) 8APSK (SOI) with no interference, (b) 8APSK(SOI) +CI, (c) 8APSK(SOI) +CWI, and (d) 8APSK(SOI) +MCWI.
Figure 2. Block diagram of the suggested AMR and radio interference detection framework.
3.3.1. Data Set Annotation
Accurate and detailed annotations are essential for training robust models, especially Mask RCNN, which relies on precise instance segmentation. Data annotation entails outlining and labeling objects of interest within images (SOI, CI, CWI, MCWI, 8 APSK, 16 APSK, 32 APSK, and QPSK) thereby providing ground-truth information to the model for learning. In this study, the labeling tool Make Sense [32] is used to annotate the type of modulation and the area of interference for each transmission and generate corresponding JSON files. A sample of this process is shown in figure 4 and in figure 5.
Figure 4. An illustration of the annotation process for “CI” and “32APSK”
Figure 5. An illustration of the annotation process for “CWI” and “16APSK”.
3.4. Mask R-CNN
Mask R-CNN (Region-based Convolutional Neural Network), a multi-task deep neural network built on top of Faster R-CNN, performs tasks including object detection and instance segmentation. It belongs to the class of architectural detectors with two phases, which are renowned for their excellent precision and accuracy [33]. There are multiple phases that can be applied with the Mask R-CNN approach. However, figure 6 depicts the entire architecture of the proposed algorithm.
Figure 6. Illustration of Mask R-CNN architecture
Backbone Network: In deep learning, the backbone network is a form of neural network that acts as the foundation for many other neural networks. A deep learning backbone network is a form of artificial neural network (ANN) made of numerous processing layers linked together. The term backbone often refers to the feature-extracting network that converts input data into a certain feature representation. There are many popular CNN architectures that we can use as a backbone in neural networks, such as ResNet101 [34] and ResNet-50 [35].
Region Proposal Network (RPN): RPN was created to solve the limitations of selective search, an offline method that is computationally expensive [36]. It is critical in the Mask R-CNN approach since it generates a list of recommended places known as regions of Interest (ROIs) where objects may be present. The RPN operates based on the feature map generated from the backbone network. It is also more efficient.
ROI Align: A crucial step in the Mask R-CNN approach is called ROI Align, which aims to match the properties of recommended Regions of Interest (ROIs) with predetermined spatial dimensions. It eliminates the flaws of the past approach recommended Regions of Interest (ROIs) with predetermined spatial dimensions. It eliminates the flaws of the past approach (Faster R_CNN), such as quantization or pooling, which could lead to misalignments and incorrect mask predictions [33].
Classification and Bounding Box Regression: The Mask R-CNN approach continues on to the classification and bounding box regression stages after obtaining aligned features from the ROI Align step. In order to accurately localize the objects, it is necessary to give object class labels to the suggested Regions of Interest (ROI) during this phase and improve the bounding box coordinates. The model can learn and generalize well across many instances of objects thanks to this sharing of parameters, which also enables quick calculations.
Mask Prediction: The final stage in the Mask R-CNN procedure is to predict the pixel-level masks for each occurrence of an item within the indicated ROIs. Each ROI-aligned feature map is fed into the mask head to generate a binary mask for the object. Mask R-CNN extends the capabilities of classic object detection frameworks by adding pixel-level segmentation and mask prediction [33]. This allows for a more in-depth study and analysis of objects contained within an image.
These components work together for object detection and instance segmentation tasks. The backbone network extracts high-level features from the input image. The FPN creates a multiscale feature pyramid, enabling the model to handle objects of various sizes effectively. The RPN generates region proposals, and ROIAlign ensures precise feature extraction for each region proposal, leading to improved segmentation accuracy, particularly for small objects. The mask head generates segmentation masks for each detected object, enabling fine-grained pixel-level boundaries for accurate and detailed instance segmentation.
3.4.1. Interference Detection Mechanisms
The input image is suggested by the backbone network, which is built on a pre-trained deep convolutional neural network. In this study, we used ResNet101 [34] and ResNet50 [35] to extract the high-level features. The region proposal network (RPN) then makes use of these traits to provide candidate object suggestions, which include possible areas of interest (ROIs) where objects can be found. The proposed ROIs are then further refined and classified into distinct object categories through the application of fully connected layers and SoftMax functions. This allows for the precise identification of a variety of signal components, including the signal of interest (SoI), modulation types such as QPSK, 8APSK, 16APSK, and 32APSK, as well as interference sources, including CI, CWI, and MCWI.
3.4.2. Loss Function Components in Mask R-CNN
During training, the mask R-CNN approach establishes the multi-task loss function for each ROI sampled as follows:
4. EXPERIMENT AND ALGORITHM EVALUATION
4.1. Implementation Detail
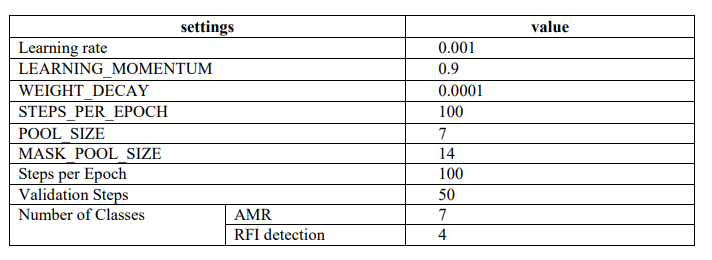
Mask R-CNN with the backbone Resnet101 and Resnet50 architecture was utilized in this work to detect and segment interference as well as recognize signal modulation used by receivers. To realize the algorithm network, this experiment used the Mask R-CNN implementation as provided by Matterport [37]. Python was specifically used for the work experiments through Anaconda, a distribution that combines TensorFlow 2.2 [38] and Keras version 2.3.1 [39] with Python 3.7. Moreover, the transfer learning technique was used to fine-tune the weights of the pre-trained model. This approach leverages pre-existing knowledge from models trained on large datasets to improve performance on our specific task. The dataset was randomly divided into two groups for training and validation: 80% for training and 20% for validation. This partitioning process was used to guarantee that there is enough data for model learning while also retaining a separate set for evaluating the model’s performance on unseen samples. The training set was used to maximize the parameters of the model, while the validation set was used to fine -tune themodel and avoid overfitting. The following Table 2 provides an overview of the training parameters:
Table 2. training settings
5. PERFORMANCE EVALUATION
This section depicts the simulation results of the proposed methodology for RFI recognition as well as AMR. Object detection and image segmentation are critical problems in computer vision with different evaluation parameters. The goal of object detection is to accurately locate and identify items in a picture. However, the accuracy and effectiveness of the models are typically assessed using performance metrics like mean average precision (mAP), mean average recall (mAR), and F1 score in tasks that include object detection and instance segmentation. Furthermore, accuracy defines the frequency with which a model generates accurate predictions. It is determined by dividing the total number of predictions the model makes by the number of accurate predictions.
Tr ue negatives (TN) represent cases where the model accurately predicted the negative category.True positives (TP) occur when the ground truth is positive, and the model correctly predicts it as positive. False positives (FP) correspond to cases where the model predicts the positive category, but the ground truth is negative. False negatives (FN) denote instances where the model predicts the negative category, but the ground truth is positive.
The equation for mAP is as follows:
considering that (𝐴𝑃)𝐽 indicates the average precision of the Jth class, K represents the total of classes being assessed.
The equation formAR:
Where (𝐴𝑅)𝐽 denotes the average precision of the Jth class, K represents the total of classes being assessed.
The equation for F1_score:
These metrics provide a detailed understanding of different aspects of the model’s effectiveness and ensure a robust evaluation of the model’s performance.
6. RESULTS
6.1. Radio Frequency Interference Detection
In this part, we trained our algorithm to detect and segment the various types of interferences present in interest signals, such as MCWI, CWI, and CI, using ResNet101 and ResNet50 with the same hyperparameter values. These experiments were conducted under different AWGN power levels in the range of -168 to -125 dBm, approximately equivalent to Signal-to-Noise Ratios (SNR) of 5 to 12 dB. The models demonstrated their efficacy by providing excellent results across a variety of performance indicators, as shown in Table 3. Furthermore, figure 7 depicts outputs, providing a qualitative perspective on the effectiveness of our method, and provides visual insights into the model’s capabilities.
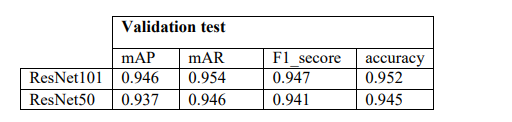
Table 3. .The evaluation values of our model for RFI using ResNet101 and ResNet50
The models precisely detect the objects and give high-quality bounding boxes for the three classes on the test dataset, with a high mAP score of 0.946 for ResNset101 and 0.937 for ResNet50. The high mAP score demonstrates that the models can accurately determine whether objects are there and where they are. Besides, Mask R-CNN architecture with a ResNet101 backbone has a mAR value of 0.954, while ResNet50 has a value of 0.946, indicating good effectiveness in object recall under different scenarios. These mAR scores demonstrate the model’s ability to recall and correctly identify “CWI”, “MCWI” and “CI” objects within the signal of interest. Moreover, the F1scores of 0.947 and 0.941 for Resnet101 and Resnet50, respectively, are balanced statistics that account for both recall and precision. Because they have a high harmonic mean between recall and precision, they are an effective overall measure of the model’s performance. With these values of the F1score, the models appear to have a decent balance between identifying true positives and reducing false positives and false negatives.Moreover, both models demonstrate high accuracy, with ResNet101 achieving 0.952 and ResNet50 reaching 0.945, highlighting their overall correctness in predictions. However, as shown in the table, ResNet101 outperforms ResNet50 due to superior results, which can be attributed to a variety of factors, including its deeper architecture and enhanced ability to capture complex information.
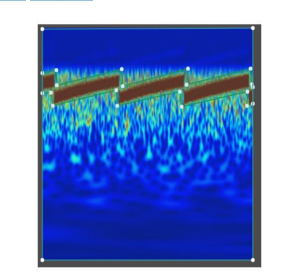
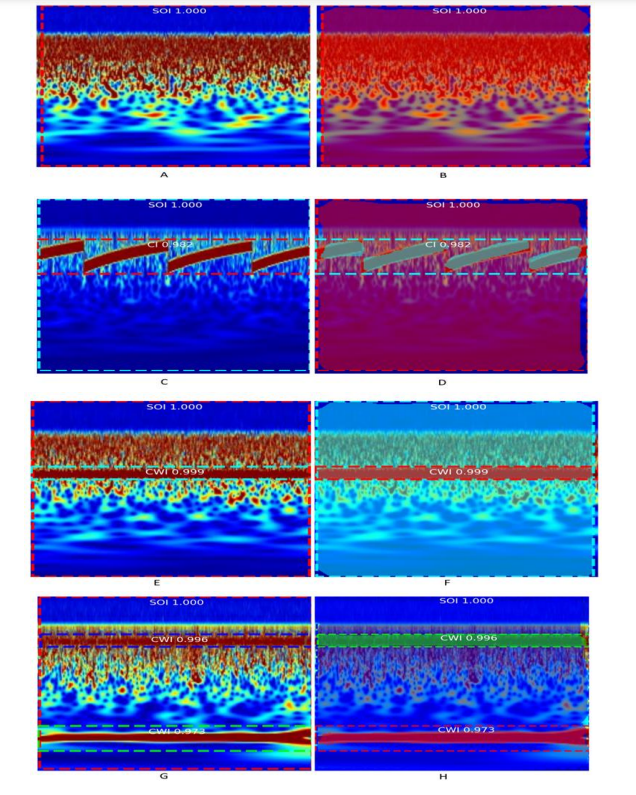
Figure 7. A and B illustrate the results of object detection and instance segmentation, respectively. They were accurately generated from the same input using Mask R-CNN. Both outputs clearly show the presence of ‘SOI’ without any interference. The output pictures C and D, which were generated from the same input using Mask R-CNN, demonstrate the outcomes of object detection and instance segmentation, respectively. They show the existence of ‘CWI’ interference in the SOI. The output pictures E and F, which were generated from the same input using Mask R-CNN, demonstrate the outcomes of object detection and instance segmentation, respectively. They show the existence of multiple continuous wave interference (MCWI) in SOI. The output pictures G and H, which were generated from the same input using Mask RCNN, demonstrate the outcomes of object detection and instance segmentation, respectively. They show the existence of ‘CWI’ interference in the SOI.
6.2. Automatic Modulation Recognition
In this section, we utilized the Mask R-CNN algorithm with two different backbones, ResNet101 and ResNet50, to train and recognize various types of modulation including 8APSK, 16APSK, 32APSK, and QPSK. Additionally, the algorithm was trained to accurately segment different types of interference in signal modulation, such as MCWI, CWI, and CI. The training dataset encompassed a range of Additive White Gaussian Noise (AWGN) power levels from -168 to – 125 dBm, approximately corresponding to Signal-to-Noise Ratios (SNR) ranging from 5 to 12 dB. The results presented in Table 4 demonstrate the effectiveness of the Mask R-CNN model for automatic modulation recognition under diverse interference scenarios, leveraging ResNet101 and ResNet50 architectures. Notably, the performance metrics including mAP, mAR, F1 score, and accuracy values for ResNet50 and ResNet101 reveal a significant performance disparity between the two models. Specifically, the findings indicate that ResNet101 consistently outperformed ResNet50 across all evaluation criteria, highlighting its superior performance in this context.
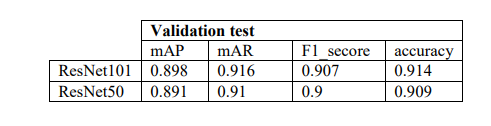
Table 4. The evaluation values of our model for AMRusing ResNet101 and ResNet50
The models demonstrate robust performance across critical parameters, highlighting their proficiency in achieving high mAP, mAR, and accuracy levels. These metrics emphasize the models’ exceptional ability to accurately identify a wide range of modulation schemes and effectively segment interference zones within received signals. The combined capabilities of Mask R-CNN in precise interference detection and AMR establish it as a valuable tool with versatile applications. Figure 8 visually presents the distinct masks generated by our model to pinpoint instances of CWI, MCWI, and CI, alongside the modulation types utilized in the primary signal, such as 8APSK, 16APSK, 32APSK, and QPSK. Each uniquely color-coded mask signifies a specific type of interference present within the signal of interest, enhancing the clarity and accuracy of both interference identification and modulation recognition processes.
7. DISCUSSION
In this study, we have presented a comprehensive analysis of the use of Mask R-CNN for automatic modulation recognition and interference identification in radio frequency-based communication systems. Our results demonstrate that Mask R-CNN is a promising solution for addressing the challenges posed by the coexistence of modulated signals and interference in wireless communications. Despite the different goals of the two models, we achieved notable performance in both tasks. The RFI model achieved high precision and recall by optimizing the labeling strategy with fewer categories, while the AMR model recognized four discrete modulation schemes (8APSK, 16APSK, 32APSK, and QPSK) and three interference classes (CI, CWI, and MCWI). However, the need to differentiate among different background modulation schemes added complexity, which reduced the AMR model’s performance compared to the RFI model. Moreover, our research provides a comprehensive analysis of ResNet101 and ResNet50, revealing a consistent and notable trend: ResNet101 consistently outperforms ResNet50 across all performance metrics in both tasks. The deeper architecture of ResNet101 confers distinct advantages, enabling it to excel in multiple facets of object detection and segmentation. This superiority is evident in its elevated mAP, mAR, and accuracy scores. The persistent dominance of ResNet101 underscores its effectiveness in capturing intricate features and subtle patterns, thereby enhancing its overall performance in the designated tasks. The outcomes have shown the Mask R-CNN’s effectiveness in addressing the difficult issue of interference detection and localization and have offered valuable knowledge that can considerably progress interference analysis, jamming countermeasures, and interference. The segmentation results from Mask RCNN have proven to be a goldmine of information, and the high-resolution segmentation maps offer a visual representation of the interference shapes and strategies used by jammers.
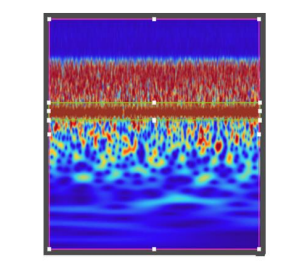
Figure 8. The two images, A and B, illustrate the results of object detection and instance segmentation, respectively. They were accurately generated from the same input using Mask R-CNN. Both outputs clearly show the presence of ‘QPSK’ without any interference. The output pictures, C and D, obtained from the same input using Mask R-CNN, demonstrate the outcomes of object detection and instance segmentation, respectively. These results effectively demonstrate modulation recognition (‘8APSK’) and interference detection (‘CI’). The output pictures, E and F, obtained from the same input using Mask RCNN, demonstrate the outcomes of object detection and instance segmentation, respectively. These results effectively demonstrate automatic modulation recognition (’32APSK’) and interference detection (‘CWI’). The output pictures, A and B, obtained from the same input using Mask R-CNN, demonstrate the outcomes of object detection and instance segmentation, respectively. These results effectively demonstrate automatic modulation recognition (‘8APSK’) and interference detection (‘MCWI’).
Moreover, the Mask R-CNN technique introduces additional parameters not typically available in classification-based methods. Prior studies utilized two unsupervised machine learning algorithms [29] and deep learning models like VGG-16, GoogleNet, ResNet-18, and AlexNet [30] for RFI identification through transfer learning. Table 5 underscores the differences between our approach and existing research. While previous studies focused on training separate models to detect specific interference types within AMR contexts, our method achieves simultaneous detection of multiple interferences and identifies all four modulation types using a unified model, yielding promising outcomes. This advancement not only improves performance but also significantly reduces hardware requirements. Furthermore, this method enhances understanding of jamming mechanisms and reveals previously undetected interference types. This knowledge enables proactive adjustments to enhance countermeasures against evolving interference tactics.
However, notable constraints must be recognized regarding the proposed algorithm, particularly concerning its computational complexity and the time required for model training. The intricate nature of interference detection, coupled with the complexity of the data, demands substantial computational resources. Consequently, the training process can be significantly time-consuming, potentially extending over many hours.
Table 5. A comprehensive comparison of our proposed method to existing method
7.1. Practical Implementation
The trained Mask R-CNN model, meticulously tailored for AMR and RDI Detection applications, finds practical deployment avenues in real-world cognitive radio systems. Its implementation is notably adaptable to FPGA SDR platforms [40] and specialized hardware such as the Xilinx ZCU111 RFSoC platform [41]. These platforms offer the computational power necessary for efficient real-time processing, guaranteeing swift and responsive actions in the face of dynamic radio environments. The inherent compatibility of Mask R-CNN with existing hardware infrastructure further streamlines its integration into cognitive radio systems. This compatibility ensures a seamless fit, providing a cost-effective and practical solution for spectrum management and interference mitigation within wireless communication networks.
By harnessing the capabilities of FPGA SDR platforms and specialized hardware like the Xilinx ZCU111 RFSoC, our proposed model not only aligns with the demanding processing requirements of cognitive radio but also delivers a robust and feasible approach to address realworld challenges in wireless communication scenarios. The parallel processing capabilities of FPGAs facilitate real-time processing, reducing latency and ensuring timely responses to incoming signals. Additionally, FPGAs offer efficient resource utilization, allowing for optimized implementation of complex deep learning models on hardware, which is crucial for real-time processing in cognitive radio systems. Furthermore, FPGA platforms provide flexibility and reconfigurability, enabling easy adaptation to changing modulation types, interference patterns, and system requirements in dynamic radio environments.
8. CONCLUSION AND FUTURE WORK
In this research, we presented a novel approach based on the mask R-CNN algorithm for automatic modulation recognition and radio frequency interference detection. The experimental results in the scalogram of the received signal demonstrate that the proposed method is best suited and effectively enhances the accuracy of interference detection and automatic modulation recognition in radio frequency-based communication systems. Its ability to provide insights into interference patterns, combined with extra characteristics and real-world applicability, makes it a potent and indispensable instrument in the field of cognitive radio and wireless communication, especially for anti-jamming. In addition, these findings highlight the significance of adopting a suitable backbone architecture depending on the task’s individual requirements. While ResNet101 exhibits greater performance, the related computational cost must be considered, making the decision between ResNet50 and ResNet101 dependent on achieving a compromise between performance and resource efficiency.
In the future, we will enrich the datasets of various environments to train our model on all types of jammers in order to predict all jammers and detect and identify dangerous signals in a wide range of communications. As a result, it can be immediately applied to cognitive radio, the Global Navigation Satellite System (GNSS), and generally in the field of signal processing to detect and identify harmful signals, and by doing so, we can increase the quality of our wireless radio network.
CONFLICTS OF INTEREST
The authors declare no conflict of interest.
REFERENCES
[1] M. Khalaf, A. Farhan, and A. Yahya, ‘Sensing Time Improvement using Two Stage Detectors for Cognitive Radio System’, International journal of Computer Networks & Communications, vol. 16, Jan. 2024, doi: 10.5121/ijcnc.2024.16105.
[2] Q. Zheng, P. Zhao, Y. Li, H. Wang, and Y. Yang, ‘Spectrum interference-based two-level data augmentation method in deep learning for automatic modulation classification’, Neural Comput & Applic, vol. 33, no. 13, pp. 7723–7745, Jul. 2021, doi: 10.1007/s00521-020-05514-1.
[3] S. Talekar, S. Banait, and M. Patil, ‘Improved Q-Reinforcement Learning based Optimal Channel Selection in Cognitive Radio Networks’, IJCNC, vol. 15, no. 3, pp. 1–14, May 2023, doi: 10.5121/ijcnc.2023.15301.
[4] M. A. Aref, S. K. Jayaweera, and E. Yepez, ‘Survey on cognitive anti-jamming communications’, IET Communications, vol. 14, no. 18, pp. 3110–3127, 2020, doi: 10.1049/iet-com.2020.0024.
[5] K. Dabcevic, ‘Intelligent jamming and anti-jamming techniques using Cognitive Radios’, PhD Programme in Computational Intelligence University of Genoa, 2015.
[6] S. K. Balam, P. Siddaiah, and S. Nallagonda, ‘Optimization Analysis of Cooperative Spectrum Sensing System over Generalized $$\kappa -\mu $$and $$\eta -\mu $$Fading Channels’, Wireless Pers Commun, vol. 116, no. 4, pp. 3081–3100, Feb. 2021, doi: 10.1007/s11277-020-07836-8.
[7] Y. Gwon, S. Dastangoo, C. Fossa, and H. T. Kung, ‘Competing Mobile Network Game: Embracing antijamming and jamming strategies with reinforcement learning’, in 2013 IEEE Conference on Communications and Network Security (CNS), Oct. 2013, pp. 28–36. doi: 10.1109/CNS.2013.6682689.
[8] T. Oyedare, V. K. Shah, D. J. Jakubisin, and J. H. Reed, ‘Interference Suppression Using Deep Learning: Current Approaches and Open Challenges’, IEEE Access, vol. 10, pp. 66238–66266, 2022, doi: 10.1109/ACCESS.2022.3185124.
[9] Y. Arjoune and S. Faruque, ‘Smart Jamming Attacks in 5G New Radio: A Review’, in 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Jan. 2020, pp. 1010–doi: 10.1109/CCWC47524.2020.9031175.
[10] L. Li, Z. Dong, Z. Zhu, and Q. Jiang, ‘Deep-Learning Hopping Capture Model for Automatic Modulation Classification of Wireless Communication Signals’, IEEE Transactions on Aerospace and Electronic Systems, vol. 59, no. 2, pp. 772–783, Apr. 2023, doi: 10.1109/TAES.2022.3189335.
[11] F. Zhang, C. Luo, J. Xu, Y. Luo, and F.-C. Zheng, ‘Deep learning based automatic modulation recognition: Models, datasets, and challenges’, Digital Signal Processing, vol. 129, p. 103650, Sep. 2022, doi: 10.1016/j.dsp.2022.103650.
[12] O. A. Dobre, A. Abdi, Y. Bar-Ness, and W. Su, ‘Survey of automatic modulation classification techniques: classical approaches and new trends’, IET Communications, vol. 1, no. 2, pp. 137–156, Apr. 2007, doi: 10.1049/iet-com:20050176.
[13] J. W. Choi and N. I. Cho, ‘Suppression of narrow-band interference in DS-spread spectrum systems using adaptive IIR notch filter’, Signal Processing, vol. 82, no. 12, pp. 2003–2013, Dec. 2002, doi: 10.1016/S0165-1684(02)00385-7.
[14] S. R. Lach, M. G. Amin, and A. R. Lindsey, ‘Broadband interference excision for software-radio spread-spectrum communications using time-frequency distribution synthesis’, IEEE Journal on Selected Areas in Communications, vol. 17, no. 4, pp. 704–714, Apr. 1999, doi: 10.1109/49.761046.
[15] P. Sumalatha, D. G. S. Mahalakshmi, D. G. S. M. P Sumalatha, P. Sumalatha, and D. G. S. Mahalakshmi, ‘DEF: Deep Ensemble Neural Network Classifier for Android Malware Detection’, International Journal of Computer Networks & Communications (IJCNC), vol. 16, no. 16, Art. no. 02, Mar. 2024, doi: 10.5121/ijcnc.2024.16204.
[16] H. Ouamna, Z. Madini, and Y. Zouine, ‘Deep Learning Applied for Spectrum Sensing’, in Proceedings of Seventh International Congress on Information and Communication Technology, X.- S. Yang, S. Sherratt, N. Dey, and A. Joshi, Eds., in Lecture Notes in Networks and Systems. Singapore: Springer Nature, 2023, pp. 787–797. doi: 10.1007/978-981-19-2397-5_70.
[17] A. Kulkarni, A. Seetharam, A. Ramesh, and J. D. Herath, ‘DeepChannel: Wireless Channel Quality Prediction Using Deep Learning’, IEEE Transactions on Vehicular Technology, vol. 69, no. 1, pp. 443–456, Jan. 2020, doi: 10.1109/TVT.2019.2949954.
[18] Q. Hu, F. Gao, H. Zhang, S. Jin, and G. Y. Li, ‘Deep Learning for Channel Estimation: Interpretation, Performance, and Comparison’, IEEE Transactions on Wireless Communications, vol. 20, no. 4, pp. 2398–2412, Apr. 2021, doi: 10.1109/TWC.2020.3042074.
[19] A. Kharbouche, Z. Madini, Y. Zouine, and N. El-Haryqy, ‘Signal demodulation with Deep Learning Methods for visible light communication’, in 2023 9th International Conference on Optimization and Applications (ICOA), Oct. 2023, pp. 1–5. doi: 10.1109/ICOA58279.2023.10308822.
[20] T.-Y. Lin et al., ‘Microsoft COCO: Common Objects in Context’, in Computer Vision – ECCV 2014, D. Fleet, T. Pajdla, B. Schiele, and T. Tuytelaars, Eds., in Lecture Notes in Computer Science. Cham: Springer International Publishing, 2014, pp. 740–755. doi: 10.1007/978-3-319-10602-1_48.
[21] K. N. R. S. V. Prasad, K. B. D’souza, and V. K. Bhargava, ‘A Downscaled Faster-RCNN Framework for Signal Detection and Time-Frequency Localization in Wideband RF Systems’, IEEE Transactions on Wireless Communications, vol. 19, no. 7, pp. 4847–4862, Jul. 2020, doi: 10.1109/TWC.2020.2987990.
[22] Z. Xu, I. Petrunin, and A. Tsourdos, ‘Identification of Communication Signals Using Learning Approaches for Cognitive Radio Applications’, IEEE Access, vol. 8, pp. 128930–128941, 2020, doi: 10.1109/ACCESS.2020.3009181.
[23] N. El-Haryqy, Z. Madini, Y. Zouine, and A. Kharbouche, ‘A Survey on Automatic Signal Detection Using Deep Learning’, in 2023 9th International Conference on Optimization and Applications (ICOA), Oct. 2023, pp. 1–6. doi: 10.1109/ICOA58279.2023.10308833.
[24] S. Hu, Y. Pei, P. P. Liang, and Y.-C. Liang, ‘Robust Modulation Classification under Uncertain Noise Condition Using Recurrent Neural Network’, in 2018 IEEE Global Communications Conference (GLOBECOM), Dec. 2018, pp. 1–7. doi: 10.1109/GLOCOM.2018.8647582.
[25] K. Tekbıyık, A. R. Ekti, A. Görçin, G. K. Kurt, and C. Keçeci, ‘Robust and Fast Automatic Modulation Classification with CNN under Multipath Fading Channels’, in 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), May 2020, pp. 1–6. doi: 10.1109/VTC2020- Spring48590.2020.9128408.
[26] ‘Radio frequency interference mitigation using deep convolutional neural networks – ScienceDirect’. Accessed: Aug. 04, 2023. [Online]. Available: https://www.sciencedirect.com/science/article/abs/pii/S2213133716301056
[27] ‘Remote Sensing | Free Full-Text | Deep Learning-Based Automatic Clutter/Interference Detection for HFSWR’. Accessed: Jun. 12, 2023. [Online]. Available: https://www.mdpi.com/2072- 4292/10/10/1517
[28] M. Zhu, Y. Li, Z. Pan, and J. Yang, ‘Automatic modulation recognition of compound signals using a deep multi-label classifier: A case study with radar jamming signals’, Signal Processing, vol. 169, p. 107393, Apr. 2020, doi: 10.1016/j.sigpro.2019.107393.
[29] A. Amache, W. Ajib, and M. Boukadoum, ‘Support Vector-Based Unsupervised Learning Approaches for Radio Frequency Interference Detection’, in 2022 IEEE 95th Vehicular Technolog Conference: (VTC2022-Spring), Jun. 2022, pp. 1–5. doi: 10.1109/VTC2022- Spring54318.2022.9860972.
[30] S. Ujan, N. Navidi, and R. Jr Landry, ‘An Efficient Radio Frequency Interference (RFI) Recognition and Characterization Using End-to-End Transfer Learning’, Applied Sciences, vol. 10, no. 19, Art. no. 19, Jan. 2020, doi: 10.3390/app10196885.
[31] D. Borio, ‘GNSS Acquisition in the Presence of Continuous Wave Interference’, IEEE Transactions on Aerospace and Electronic Systems, vol. 46, no. 1, pp. 47–60, Jan. 2010, doi: 10.1109/TAES.2010.5417147.
[32] ‘Make Sense’. Accessed: Aug. 29, 2023. [Online]. Available: https://www.makesense.ai/
[33] K. He, G. Gkioxari, P. Dollar, and R. Girshick, ‘Mask R-CNN’, presented at the Proceedings of the IEEE International Conference on Computer Vision, 2017, pp. 2961–2969. Accessed: May 18, 2023. [Online]. Available: https://openaccess.thecvf.com/content_iccv_2017/html/He_Mask_RCNN_ICCV_2017_paper.html
[34] ‘He: Deep residual learning for image recognition – Google Scholar’. Accessed: Jul. 13, 2023. [Online]. Available: https://scholar.google.com/scholar_lookup?journal=Proc.+IEEE+Conf.+Comput.+Vis.+Pattern+Reco gnit.&title=Deep+residual+learning+for+image+recognition&pages=770-778&
[35] K. He, X. Zhang, S. Ren, and J. Sun, ‘Deep Residual Learning for Image Recognition’, presented at the Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, 2016, pp. 770–778. Accessed: Jul. 13, 2023. [Online]. Available: https://openaccess.thecvf.com/content_cvpr_2016/html/He_Deep_Residual_Learning_CVPR_2016_paper.html
[36] S. Ren, K. He, R. Girshick, and J. Sun, ‘Faster R-CNN: Towards Real-Time Object Detection with Region Proposal Networks’, in Advances in Neural Information Processing Systems, Curran Associates, Inc., 2015. Accessed: Jul. 14, 2023. [Online]. Available: https://proceedings.neurips.cc/paper_files/paper/2015/hash/14bfa6bb14875e45bba028a21ed38046- Abstract.html
[37] Mask R-CNN for Object Detection and Segmentation. (Jul. 03, 2023). Python. Matterport, Inc. Accessed: Jul. 03, 2023. [Online]. Available: https://github.com/matterport/Mask_RCNN
[38] ‘Keras: Deep Learning for humans’. Accessed: Jul. 03, 2023. [Online]. Available: https://keras.io/
[39] ‘[1603.04467] TensorFlow: Large-Scale Machine Learning on Heterogeneous Distributed Systems’. Accessed: Jul. 03, 2023. [Online]. Available: https://arxiv.org/abs/1603.04467
[40] Z.-L. Tang, S.-M. Li, and L.-J. Yu, ‘Implementation of Deep Learning-Based Automatic Modulation Classifier on FPGA SDR Platform’, Electronics, vol. 7, no. 7, Art. no. 7, Jul. 2018, doi: 10.3390/electronics7070122.
[41] S. Tridgell, D. Boland, P. H. W. Leong, and S. Siddhartha, ‘Real-Time Automatic Modulation Classification’, in 2019 International Conference on Field-Programmable Technology (ICFPT), Dec. 2019, pp. 299–302. doi: 10.1109/ICFPT47387.2019.00052.