IJCNC 02
ENHANCING CYBERSECURITY DEFENSES: A MULTICRITERIA DECISION-MAKING APPROACH TO MITRE ATT&CK MITIGATION STRATEGY
Ihab Mohamed1, Hesham A. Hefny2, and Nagy R. Darwish1, Cairo University, Egypt
ABSTRACT
Cybersecurity is a big challenge as hackers are always trying to find new methods to attack and exploit system vulnerabilities. Cybersecurity threats and risks have increased in recent years, due to the increasing number of devices and networks connected. This has led to the development of new cyberattack patterns, such as ransomware, data breaches, and advanced persistent threats (APT). Consequently, defending such complicated attacks needs to stay up to date with the latest system vulnerabilities and weaknesses to set a proper cybersecurity defensestrategy. This paper aims to propose a defense strategy for the presented security threats by determining and prioritizing which security control to put in place based on combining the MITRE ATT&CK framework with multi-criteria decision-making (MCDM) techniques. This approach helps organizations achieve a more robust and resilient cybersecurity posture.
KEYWORDS
Cybersecurity, MITRE, APT, MCDM, Threat, Attack, Vulnerabilities.
1. INTRODUCTION
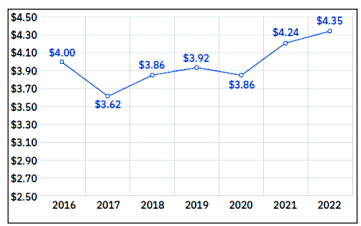
A cybersecurity risk assessment is an important tool that enables system stakeholders to assess the threats to their systems and take appropriate steps to mitigate those risks [1]. Cyber-attacks are becoming more common so most businesses need to be prepared to face them. To achieve this target, it is necessary to follow up security standards, to use and practice the best security tools for knowing what needs to be done to make systems more secure. However, such security plans are based on the knowledge of domain experts. It is hard to figure out how dangerous a vulnerability is in the context of security and risk management. Avulnerability refers to defects or weaknesses in a system’s design, operation, or implementation that could be used against the system to gain access to damage or to compromise sensitive data. Advanced persistent threats (APTs) are mainly complex attacks that are composed of several elementary attacks with no previous knowledge about what tactics they use. Inadequate cybersecurity strategies can lead to data breaches, identity theft, and other forms of cybercrime. Surveys show that organizations remain hesitant to implement effective cyber countermeasures despite the estimated cybercrime cost of $945 billion worldwide in 2020 [2]. According to an IBM study, 83% of organizations have had at least one data breach, and the average cost of a breach is $4.35 million in 2022, a 2.6% increase from 2021 [3]. The UnitedStates ranks first in terms of the average cost of a data breach, with an average cost of $9.44 million, followed by the Middle East, with an average cost of $7.46 million, Canada, with an average cost of $5.64 million, and the United Kingdom, with an average cost of $5.05 million, and Germany, with an average cost of $4.85 million. Figure. 1 shows the average total cost of data breaches in million USD all over the world [3]. Also, according to the Allianz Risk Barometer, the top concerns for businesses globally in 2022 were: 44% for cyber incidents, 42% for business interruptions, and 25% for natural disasters. [4]. The significance of analyzing attack action correlations and forecasting hostile behavior, which enables proactive intrusion investigation and prevention, is an aspect that business solutions miss.
Figure 1. The average total cost of data breach [3]
In an endeavor to mitigate this problem and overcome cyber threats and attacks, organizations are interested in developing plans to improve their security operations. This includes implementing security measures for monitoring, protecting, and applying policies and procedures to defend systems and data. To predict the strategies, techniques, and tactics of the adversary’s behavior, the scientific community has been focusing on modeling cybersecurity attack patterns and methodologies based on reported incidents [5]. The Center of Threat Informed Defense (CID) builds on MITER ATT & CK® (which stands for Adversarial Tactics, Techniques, and Common Knowledge) and is considered an important threat-informed defense foundation used by security teams and vendors in their enterprise security operations. They have a map that shows how different controls and threat techniques work [6]. The adversary framework put forth by MITRE’s ATT&CK framework is probably the most well-known defense strategy based on actual cybersecurity threat observations. The paper introduces an improved strategy to counter sophisticated cyber-security threats by formulating a prioritized response plan derived from the top ten recognized cybersecurity attack methods. This method is deemed highly efficient in leveraging common system vulnerabilities and weaknesses that are often exploited in significant cyber-attacks. The proposed approach allows combining Multi-Criteria Decision-Making Methods (MCDM) with MITRE ATT&CK framework to provide an ordered list of mitigation methods based on the priority ranking for each possible attack. This provides quick response and great flexibility for security management in establishing an effective defense at a low cost against any potential attack. The rest of the paper is organized as follows: Section 2 basic concepts about vulnerabilities and cyberattack risks. Information security frameworks are presented in section 3. Section 4 presents the MITRE ATT&CK framework. MCDM methods are discussed in section 5. Related work found in the literature is given in section 6. Section 7 presents the proposed mitigation strategy based on the MCDM method. The formulation of the proposed MCDM method is given in section 8. An illustrative case study is demonstrated in section 9. Section 10 gives the conclusion and the future work.
2. VULNERABILITIES, THREATS, CYBERATTACKS
As per the National Institute of Standards and Technology (NIST), vulnerability is defined as a weakness in the computational logic (e.g., code) found in software and hardware components that, when exploited, results in a negative impact on confidentiality, integrity, or availability [7]. Threats are actions taken to gain a benefit from security breaches in a system and negatively affect it [8]. Cyberattacks are any kind of malicious activity that attempts to collect, disrupt, deny, degrade, or destroy information system resources or the information itself [9]. Risk is a function of threats exploiting vulnerabilities to impact operations and damage or destroy assets, see Figure. 2. A quantification of the risk factor is computed as follows [10]: Risk factor = (probability of threat) × (probability of vulnerability) × (impact of vulnerability) Therefore, any defense strategy should address the above four issues. Numerous sources offer information about quantifiable metrics and scoring measures on known vulnerabilities and exploitations. Such information can be used to guide defenders in targeting and prioritizing solutions. The following subsections give a brief overview of different vulnerability databases.
Figure 2. Risk factors [10]
2.1. National Vulnerability Database
National Vulnerability Database (NVD) is a U.S. government repository for standards-based vulnerability management. NVD was launched by the NIST in 2005 [11].
2.2. Common Vulnerabilities and Exposures
Common Vulnerabilities and Exposures (CVE) is a comprehensive cyber security vulnerability database that integrates all publicly available U.S. government vulnerability resources. It also provides references to industry resources [12]. The CVE list was launched by MITRE as a community effort in 1999.
2.3. Common Vulnerability Scoring System
Common Vulnerability Scoring System (CVSS) provides a means to “capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity” [13]. A quantification of the Exploitability metric is computed as follows [14]:Exploitability Metric = 8.22 × Attack Vector × Attack Complexity × PrivilegesRequired × User Interaction.
2.4. Common Weakness Scoring System
Common Weakness Scoring System (CWSS) provided by MITRE is a mechanism for prioritizing software weaknesses that are present within software applications in a consistent and flexible manner [15][16]. The Centre for Threat-Informed Defence (CTID) has developed a methodology to use the adversary behaviors described in MITRE ATT&CK® to characterize the impact of vulnerabilities from CVE. This information can help defenders better assess the true risk posed by specific vulnerabilities in their environment [17].
3. INFORMATION SECURITY FRAMEWORKS
Security is defined as the absence of danger or threat [18]. To protect its operations, an organization has to maintain multiple layers of security in place, including physical security, personnel security, communications security, network security, and information security. The main pillars of information security are Confidentiality, Integrity, and Availability. Confidentiality ensures that authorized users only have access to the information they are authorized to [19]. Integrity ensures that the data is not modified or destroyed improperly and that it is available when needed [20]. Availability ensures that data is accessible and usable in a timely fashion. Information security standards provide the best practices and guidelines to ensure that data within the enterprise is protected from unauthorized access [19]. The following subsections present standards and frameworks of information security management that are essential for planning defense strategy.
3.1. ISO 27001 Framework
The International Organization for Standardization (ISO) launched the ISO 27001 standard as a model for setting up, running, and improving an information security management system (ISMS) by providing a framework for organizations to keep their data safe [20]. Adopting an ISO 27001 system is a strategic decision that affects the way a company operates and its relationships with other organizations. The ISMS system must balance the needs of the company with the security risks that must be managed.
3.2. NIST Cybersecurity Framework
According to NIST, Cybersecurity has multiple definitions [21]. The following are two common definitions: The first is “It is the process of protecting information by preventing, detecting, and responding to attacks”. The second definition is: “It is the measures and controls that ensure confidentiality, integrity, and availability of the information processed and stored by a computer”. The NIST Cybersecurity Framework is based on existing standards, guidelines, and practices and consists of three main components: the Framework Core, Implementation Tiers, and Profile [22].
3.3. Critical Security Controls (CIS)
CIS, by Sans Institute, provides a set of prioritized safeguards designed to lessen the most frequent cyber-attacks on systems and networks. These safeguards are based on legal, governmental, and policy frameworks, and are mapped to them so that they can be used as references. The update to CIS Controls v8 was prompted by the transition to cloud computing, virtualization, mobility, outsourcing, work-from-home policies, and evolving attacker strategies. This improved enterprise security by utilizing both full cloud and hybrid environments [23].
4. MITRE ATT&CK FRAMEWORK MODELLING APPROACH
The ATT&CK framework was developed by MITRE in 2013. It has a comprehensive, accessible database of attacks, techniques, and mitigation measures for enterprise, mobile, and industrial control systems (ICS) [5]. A structured taxonomy is provided by ATT&CK to define a variety of adversary activities. Formally, it is divided into three technical domains [23]:
- Enterprise, which describes behaviors on standard IT systems (e.g., Linux, Windows).
- Mobile, which focuses on mobile devices (e.g., Android, iOS).
- ICS, which relate more generally to cyber-physical systems.
Figure 3 is a diagram that outlines the MITRE ATT&CK relationships between an intrusion set, attack patterns, techniques, mitigations, and courses of action. The terms are arranged in a hierarchy, with intrusion sets at the top and courses of action at the bottom. Arrows depict various relationships between these terms. Overall, the MITRE ATT&CK framework provides a structured way to understand attacker behavior and helps defenders develop appropriate mitigation and response strategies [24]. The tactic describes the adversaries’ overall goal, while the technique describes how they will achieve the goals. The procedure details the specific steps that need to be taken to carry out the technique [25]. By understanding the tactic, technique, and procedure (TTPs) of an attack, one can better predict how it will be performed and how to defend against it accordingly. The tactic and method abstraction in the model gives a way to identify adversary actions using both defensive and offensive cyber security [26]. To support relevancy and maximize impact on defenders, MITER ATT & regularly develops the framework by adding major new structures, features, and technologies[27]. The MITRE enterprise release in 2023 of ATT&CK for Enterprise (version 13) contains 14 tactics, 196 techniques, and 411 subtechniques, [28][29].
Figure 3. MITRE ATT&CK relationships [24]
5. MULTI-CRITERIA DECISION MAKING
Multi-criteria decision-making (MCDM) is one of the main decision-making tools that aims to decide the best alternative by considering more than one criterion in the selection process [29]. The weighting of criteria is a crucial component of multi-criteria decision analysis. There are several methods for determining weights, which can be done manually based on the preferences and judgment of the decision-makers or automatically using developed methods and functions [30]. MCDM methods can be used to prioritize vulnerabilities or defense strategies based on their effectiveness against the TTPs listed in the ATT&CK matrix. Some examples of MCDM methods that have been used with MITRE ATT&CK in cybersecurity include [30], [31]:
- Technique for Order Preference by Similarity to Ideal Solution (TOPSIS): TOPSIS has been used to rank security controls based on their ability to mitigate specific TTPs in the ATT&CK matrix.
- Analytic Hierarchy Process (AHP): AHP has been used to prioritize defense strategies against the TTPs listed in the ATT&CK matrix based on their effectiveness, cost, and ease of implementation.
- Preference Ranking Organization Method for Enrichment Evaluation (PROMETHEE): PROMETHEE has been used to rank software vulnerabilities based on their criticality and potential impact on the organization’s systems and processes.
- Multi-Objective Optimization based on Ration Analysis (MOORA): MOORA has been used to rank software vulnerabilities based on their criticality and the potential damage they could cause if exploited by an attacker.
- Other very common MCDM methods are: Weighted Sum Model (WSM) and Weighted Product Model (WPM) [32].
Adopting MCDM methods can help security teams prioritize their efforts and resources to address the most critical vulnerabilities or defense strategies based on the TTPs listed in the MITRE ATT&CK matrix.
6. RELATED WORK
As cybersecurity threats continue to evolve, researchers have been developing various methods to help mitigate these threats. V. Kumar et al., (2023) explored ways to prioritize software vulnerabilities and found that code execution vulnerabilities are more severe than authentication errors. This framework is then used to assess the severity of a vulnerability in a real-world case [33].
Mashima D. (2023) showed that recent attacks against critical infrastructure have been increasing in severity and stealth, and attackers may be hiding in the system after penetrating it to collect system information. To combat this, in-network deception technology is being used to create “apparent” but dummy devices that are deployed throughout the infrastructure to capture the attackers’ reconnaissance activities. The effectiveness of this technology is studied based on the MITRE ATT&CK Matrix for industrial control systems. It has been found that it can effectively counter high-profile attacks that have recently been seen in the real world [34].
Heejung et al., (2022) illustrated how cyber threat intelligence (CTI) is the process of quickly collecting and analyzing data about potential security threats to find the nature and possible actions of a threat. A recent standard for doing this is the MITRE ATT&CK framework, but using this approach is time consuming and often unsuccessful. The authors have developed a new way for classifying threats using easy data argumentation (EDA), and the authors found that it improved performance by 60–80% compared to using the standard method [35].
Octavian et al., (2022) introduced a dataset of 1813 CVEs and proposed models to automatically link a CVE to one or more techniques that can be used by cyber-security professionals to help mitigate attacks. The MITRE ATT&CK Framework The models are based on the text description from the CVE metadata. The paper also performs a qualitative analysis of the CVE descriptions [36].
Wenjun et al. (2022) proposed a threat modeling language specifically designed to help organizations analyze and protect their enterprise systems against cyber-attacks. The language is based on the MITRE Enterprise ATT&CK Matrix, and it focuses on describing system assets, attack steps, defenses, and asset associations. Testing has shown that the language is effective in describing real-world cyberattacks [37].
Liu Yet et al.,(2022) illustrated how defense models against adversarial attacks have grown significantly, but the lack of practical evaluation methods has hindered progress.Evaluation can be defined as looking for a defense model’s lower bound of robustness given a budget number of iterations and a test dataset. The authors proposed a parameter-free adaptive attack evaluation method that addresses efficiency and reliability in a test-time-training fashion. By observing those adversarial examples to select a specific defense model, some regularities in their starting points and evaluation are observed. Furthermore, to approach the lower bound of robustness under the budget number of iterations, the author proposed an online statistics-based discarding strategy that automatically identifies and abandons hard-to-attack images. Notably, the author won first place out of 1681 teams in the CVPR 2021 white-box adversarial attacks on defense model competitions with this method [38].
An empirical study with expert cyber risk assessment practitioners was conducted to evaluate the adversary cost framework’s validity and utility. However, focus is often put on the latter two components of cyber risk, vulnerability, and impact, due to the assessor being able to gather data about them reliably. Furthermore, many cyber risk assessment outputs are delivered in a qualitative or semi-quantitative format, which is incongruous with the output of other business functions, particularly at the board level [39].
Pell R et al., (2021) discussed how the gap between early 5G network threat assessments and an adversarial TTPs knowledge base for future use in the MITRE ATT&CK threat modeling framework can be bridged. The author identified knowledge gaps in the existing framework for key 5G technology enablers such as SDN, NFV, and 5G-specific signalling protocols of the core network. The authors studied how the domain-specific technique works and emulated this mapping in a pre-emptive fashion to facilitate a rigorous cyber risk assessment to support intrusion detection, and to design defenses based on common APT TTPs [40].
Ahmed Met et al., (2021) found that MITRE ATT&CK provides information on the motivations, capabilities, interests, and tactics of threat actors, which can be used to inform cyber risk characterization and assessment. The authors used this information to determine the likelihood of success of an attack against a healthcare organization based on the techniques and procedures of a known threat actor [2]. Choi S el al., (2021) proposed an automatic method for generating attack sequences that are credible and reflective of known cyber-attacks. This method is based on the tactics and techniques of MITRE ATT&CK and is applied to a dataset of industrial control system security [41].
Fang Z el al., (2021) suggested that one way to tackle data breach incidents is to develop a statistical model that can be used to predict data breach incidents for individuals and enterprises. To evaluate this model, the authors applied it to a dataset of enterprise-level breach incidents. The results show that the model is effective in predicting these incidents. Data breaches are a major cybersecurity problem, and they pose a risk to individuals’ privacy. However, there is still much that is not understood about data breach risk, which makes it difficult to model and predict it [42].
Rahman M. et al. (2022) described the research that was conducted to help organizations make informed choices about the security controls to use to resist cyberattacks. The authors found that only a limited number of security controls can mitigate the many diverse types of adversarial techniques used in cyberattacks [43].
Most of the recent work on developing cybersecurity methodologies that adopt MCDM methods is directed toward quantification risk assessment based on subjective estimates of cyberattacks and existing system vulnerabilities. The MCDM approach helps in solving the vulnerabilities prioritization problem to develop a prioritization mitigation plan according to the ranked vulnerabilities [44].
Bhol et al., (2020) proposed a proactive fail-safe attitude based on MCDM, to rank organizations in terms of their security qualification. They used the security metrics: Susceptibility, Protection mechanism, Risk measurement, and Encounters, as the criteria with specific weights. Then they make a ranking comparison between the two MCDM approaches: AHP and ELECTRE III [45].
Horta et al., (2022) were concerned with improving a computer system’s security posture based on the results of Breach Attacks Simulation (BAS). Their method was found to be robust and capable of producing coherent recommendations with a prioritized action plan based on context analysis. The heat maps presented were useful tools for the decision maker to understand which points needed more attention as well as to assess the detection capacity of their environment. According to their research work, to check organization security, a specific cyberattack has to be fabricated through simulation, then the type of symptoms that affected the system was monitored, and then, the required defense plan was determined using the MCDM method based on the ordered list of top 10 attack techniques announced by MITRE ATT&CK V11 [46].
Alain and S. M. Rahman proposed a proactive method to handle cybersecurity due to recent major data breaches. While existing defenses like firewalls and antivirus are helpful, attackers develop new methods. Security professionals must adopt innovative tools and techniques to combat these evolving threats. Our goal is to make infrastructure impenetrable and prevent attacks from any source. Early detection of vulnerabilities is our best defense to minimize damage [47].
A.Subil,andS. Nairintroduces a new way to measure network security, accounting for the fact that vulnerabilities change over time. Existing metrics don’t fully address this dynamic nature, leading to poor risk management decisions. The proposed model considers factors like exploit and patch availability, which can significantly impact security depending on how vulnerabilities are connected and exploited. By incorporating the vulnerability age, the model provides a more realistic view of network security changes. It utilizes the Vulnerability Lifecycle model and CVSS metric to analyze how exploitability and impact evolve [48].
So far, there has not been a global catalogue of mitigation delivery techniques that includes a specific structure and focuses on a specific type of mitigation strategy used by organizations against threat actors. This lack of a specific mitigation strategy leaves the possibility of undetected attacks against an organization’s infrastructure, as well as the identification of monitoring gaps[].
7. THE PROPOSED APPROACH
Based on the above discussion, there are two methods for handling the cybersecurity complex attack. The first is a proactive method that aims to enhance the defensive immunity of the organization using an appropriate cybersecurity framework. This method aims to help organizations improve their cybersecurity strategy by providing a documented set of policies and procedures that can help reduce the unknown vulnerabilities and misconfigurations that exist within an enterprise network. This method of cybersecurity takes a risk management perspective, helping to identify and manage all the risks associated with the network and systems. The second is the reactive method, which is mainly concerned with the defensive procedure that has to be followed in the event of an actual security attack.
Regarding the second method, the traditional procedure followed in realistic situations is that one determines the nature of the attack, determines its causes, and handles each attack pattern separately with its associated counter-mitigation techniques and control. This method is inefficient as it may apply the same mitigation techniques many times, causing overhead in time, effort, and cost.
This paper aims to propose an effective procedure for applying the second method. The following subsections present the main idea of the proposed approach and how to implement it as an MCDM problem.
7.1. Main Idea of the Proposed Approach
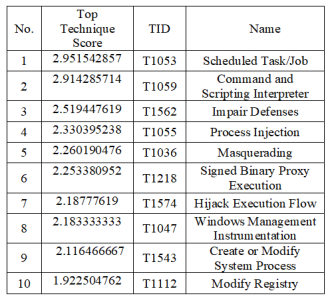
The proposed approach depends on the idea of taking advantage of knowing the relative importance of different security attacks. The importance score of each attack technique is calculated as the relative frequency of appearance of such attack technique in various categories of cyber threats.Table 1 [49], shows the top 10 techniques of attacks ordered by relative importance score.
Table 1. Top 10 ATT&CK techniques score V13[49]
Table 1 shows the following information[50]:
- Rank: This column shows the position (from 1 to 10) of each technique based on the percentage of malware samples exhibiting the behavior.
- Score: This column shows the percentage of malware samples analyzed in 2023 that exhibited the corresponding technique.
- Technique ID: This column displays the unique identifier for each MITRE ATT&CK technique, typically in the format “T1XXX”.
- Name: This column provides a descriptive name for each technique.
Table 2 shows the list of the top 10 MITRE ATT&CK techniques observed in malware samples during 2023, ranked by their prevalence. Each of the attack techniques has in turn its own of security mitigations controls with equal importance within each attack technique [50].
Table 2. MITRE attack and mitigation techniques V13
In Table 2, it is interesting to note that the same security mitigation controls can be adopted with various techniques of attacks. Hence, the novelty of the idea of our proposed approach lies in the fact that it aims to follow an effective procedure to quickly repel the security attack by applying a limited number of effective counter-mitigation steps. This helps to avoid wasting time in analyzing the type of complex cyber-attack and the different categories of threats that compose it. We have a solid fact about the top npossible techniques of attacks that are quite likely to be adopted in any complex cyber-attack with arbitrary multiple combinations of categories of threats. Accordingly, the defense strategy for an arbitrary complex cyber-attack should depend on adopting security mitigation controls based on their prioritization over all the top 10 attack techniques. Thus, this is a direct MCDM problem where the top 10 attack techniques act as criteria and the security mitigation controls act as alternatives.
Therefore, the proposed approach in this paper follows the second method of handling the cybersecurity complex attack by combining MCDM methods with the MITRE Attack cybersecurity framework version 13.0 announced in 2023 with its recent list of top techniques of attacks. The list includes different techniques of attacks that are found to be adopted in each category of cyber threat, e.g. Ransom category or Data Breach category, etc. Also, for each attack, the list of counter-security mitigation controls to be used against it is also declared [51], [49]. It is interesting to mention that the same techniques of attacks are found to be adopted in various categories of cyber threats.
7.2. MCDM Problem Formulation
The following are the steps for formulating our MCDM problem:
Step 1:
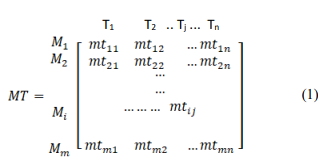
The first step is to construct the decision matrix. The columns and rows of the matrix correspond to the criteria and the alternatives respectively. In our case, the top 10 attack techniques are the criteria, while the security mitigation controls are the alternatives. The decision matrix MT mx nis given in (1).
Where mtij is the performance score of the ithsecurity mitigation control with respect to the jth attack technique, m is the number of mitigation controls and n is the number of techniques of attacks.
Step 2:
The second step is to assign a weight wj to each attack technique Tj to reflect its importance among other techniques.
Step 3:
The third step is to compute the total score for each mitigation control Mi overall attacks Tj as given in (2).
Step 4:
The fourth step is to prioritize the security mitigation controls by ranking the vector from the highest performance score to the lowest one.
Thus, the proposed defense plan against any arbitrary complex attack is to apply the ranked security mitigation controls sequentially. It is likely expected to abort the complex cyber-attack after applying a few of the top prioritized mitigation controls.
A demonstration of the applicability of the proposed approach is given through a case study.Assuming an organization has been subjected to a ransomware cyberattack. To apply the proposed MCDM approach we must select appropriate values for the ncolumns and mrows in (1). In the context of the Enterprise-attack mitigation v13, the decision matrix involves a combination of n=1,2,…up to 1238 attack techniques/sub techniques and m=1,2,…up to 43 mitigation techniques. This implies that there are 1238 criteria (n) and 43 alternatives (m). From a practical point of view, it is adequate to deal with the top 10 attack techniques, i.e. n=10, and the top 18 security mitigation controls, i.e. m=18. The weight wi of each attack technique Tj is given in Table 1. Consider that all mitigation controls that belong to a specific attack technique have equal priority of application. Therefore, we will assign the same value of performance score mtiji=1,2,…,m as follows:
Where, is the number of mitigation controls that belong to attack technique Tjas given in Table 3. Thus, =4, , … , =1.
Applying (2) we get the overall decision matrix as given in Table 3. It is clear that the last column is sorted based on the highest score of the considered mitigation controls.
Table 3. The Final Decision Matrix of Mitigation Techniques Score
Now, considering such a complex cyber-attack, the organization needs to apply the mitigation controls according to their calculated rank sequentially. It is likely expected to abort the complex attack before completing the whole 18 mitigation controls. However, again, values of n and m may be set to larger values if needed under certain circumstances.
8. ILLUSTRATIVE EXPERIMENT
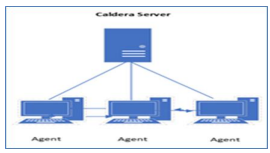
This section presents a simulation experiment to evaluate the effectiveness of cybersecurity defences of the proposed approach against malicious behaviors. The experiment has been conducted using Caldera TM simulator[52]. Caldera is a framework from MITRE that allows for automated adversary emulation. The components of the experiment are as follows:
- Caldera Server: This is the central core of the experiment. It acts as the emulation platform, coordinating the simulated attacks.
- Windows Virtual Machines (Labelled Devices): The three VM Machines connect to devices labeled “DC” (domain controller) and “Client Win 10” (client machine running Windows 10). These represent the target systems under attack in the simulation
- Agents: These agents are installed on the target machines. They relay information between Caldera and the target machines, allowing Caldera to execute commands and monitor system behavior. There are three “Agents” indicating three target machines.
Figure 4 depicts the components of the experiment.
The experiment utilized data from a Breach Attack Simulator (BAS) campaign. This suggests the Caldera platform may be leveraging pre-defined attack scenarios or behaviors during the emulation. MITRE ATT&CK is a knowledge base of adversary tactics and techniques, and the experiment specifically focused on the top 10 techniques of malicious behaviors. This indicates the attackers in the simulation will employ tactics that are commonly used in real-world attacks.
Figure 4. Caldera experiment
Thus, we employ the Caldera2 platform to simulate a virtual complex cybersecurity attack campaign that is composed of top10 attacktechniques. The experiment simulates a two-pronged cybersecurity attack. The first attack is “PowerShell Cmdlet Scheduled Task” which enables adversaries that may abuse the “Windows Task Scheduler” to perform task scheduling for the initial or recurring execution of malicious code. The second attack is “Visual Basic for Applications (VBA) and VBScript”. VBA is an event-driven programming language built into Office applications. VBA enables documents to contain macros used to automate the execution of tasks and other functionalities on the host.
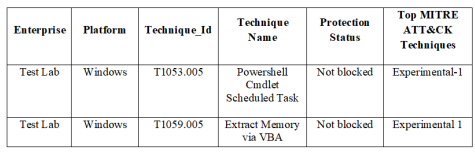
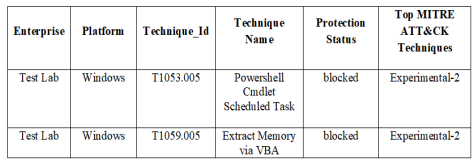
After the simulation of each attack technique, the adopted platform recorded observations in the logs to determine whether each attack was discovered, blocked, or not. Table 4 shows the infection status of the system after applying the simulated cyberattack. It is clear from Table 4 that the virtually generated cyberattack is composed of the top 2 attacks reported in Table 3, i.e T1053 & T1059. The authors manually consolidated all the simulated information resulting in an input spreadsheet. The authors then built an action plan with control items according to preferences that make sense for the tested environment. The control items were correlated based on the top 10 techniques from the MITRE ATT&CK framework found in Table 3. Table 5 shows the result of the simulation experiment after applying the proposed prioritized mitigation techniques. The results ensure the effectiveness of the proposed method to block the mentioned cyber attack. Also, Table 6 shows the advantages of using MCDM methods compared with the traditional manual one.
Table 4. The Experimental Result before applying the proposed approach.
Table 5. The Experimental Result after applying the proposed approach.
Table 6. The manually/randomly – MCDM Comparison
9. CONCLUSION
This paper demonstrates an approach for developing a prioritized mitigation plan to assess powerful cyber security. The proposed approach adopts an effective defense strategy based on MCDM WSM for ranking the security mitigation techniques of the recent top complex cyberattacks declared by MITRE Attack Cyber security Framework V13.0. Once ranking, then a priority list of security mitigation controls is obtained based on their effectiveness and coverage through the top listed cyber-attacks. The security mitigations are applied sequentially according to their priorities. It is quite likely that after the application of a few mitigations of the ranked list, the cyber threat is likely to be eliminated. This proposed defense strategy allows taking quick action to fix security vulnerabilities and reduce time, overhead, and effort. We believe that this strategy is quite effective and least expensive in time and effort against different types of attacks. In future work, we plan to apply the proposed approach using other MCDM methods.
CONFLICT OF INTEREST
The authors declare no conflict of interest.
REFERENCES
[1] H. Binyamini, R. Bitton, M. Inokuchi, T. Yagyu, Y. Elovici, and A. Shabtai,( 2021) “A Framework for Modeling Cyber Attack Techniques from Security Vulnerability Descriptions,” in Proceedings of the 27th ACM SIGKDD Conference on Knowledge Discovery & Data Mining, Aug. , pp. 2574– 2583. doi: 10.1145/3447548.3467159.
[2] M. G. Ahmed, S. Panda, C. Xenakis xenakis, and E. Panaousis, ( 2023 ,Feb) “MITRE ATT&CKdriven Cyber Risk Assessment.”. Available at: https://csrc.nist.gov/publications/detail/sp/800- 30/rev-1/final
[3] “Cost of a Data Breach Report 2022.” Accessed:.( 2023 ,Feb). [Online]. Available:https://www.ibm.com/reports/data-breach
[4] “Allianz_Risk_Barometer_2022_FINAL”, Accessed: (2023 ,Feb)). Available at: https://www.allianz.com/content/dam/onemarketing/azcom/Allianz_com/press/document/Allianz_R isk_Barometer_2022_FINAL.pdf
[5] A. Georgiadou, S. Mouzakitis, and D. Askounis,(2021) “Assessing MITRE ATT&CK Risk Using a Cyber-Security Culture Framework,” Sensors, vol. 21, no. 9, p. 3267, May 2021, doi: 10.3390/s21093267.
[6] Y. Liu, Y. Cheng, L. Gao, X. Liu, Q. Zhang, and J. Song, ( 2023) “Practical Evaluation of Adversarial Robustness via Adaptive Auto Attack,”, http://arxiv.org/abs/2203.05154
[7] N. V. D. Nist, “National Vulnerability Database. accessed. (2023, Feb),.https://nvd.nist.gov/vuln
[8] M. Humayun, M. Niazi, N. Jhanjhi, M. Alshayeb, and S. Mahmood, .( 2020) “Cyber Security Threats and Vulnerabilities: A Systematic Mapping Study,” Arab J Sci Eng, vol. 45, no. 4, pp. 3171–3189, http://doi.rg/10.1007/s13369-019-04319-2
[9] C. S. R. C. Nist, “cyber_attack accessed:.( 2023 ,Feb).” https://csrc.nist.gov/glossary/term/cyber_attack .
[10] S. Mishra, K. Anderson, B. Miller, K. Boyer, and A. Warren,.( 2020)“Microgrid resilience: A holistic approach for assessing threats, identifying vulnerabilities, and designing corresponding mitigation strategies,” Appl Energy, vol. 264,doi: 10.1016/j.apenergy.2020.114726.
[11] I. Iganibo, M. Albanese, M. Mosko, Eric, and A. E. Brito,.( 2021) “Vulnerability metrics for graphbased configuration security,” in Proceedings of the 18th International Conference on Security and Cryptography, SECRYPT 2021, pp. 259–270.
[12] “Common Vulnerabilities and Exposures History”,accessed ( 2023,feb), available at: https://www.cve.org/About/History
[13] “Common Weakness Scoring System (CWSSTM)”, accessed.( 2023,Feb) https://cwe.mitre.org/cwss/cwss_v1.0.1.html
[14] “Common Vulnerability Scoring System version 3.1 Specification Document Revision 1access.( 2023,Feb).” Available at: https://www.first.org/cvss/ [15] “Common Weakness Scoring System (CWSSTM)”, accessed ( 2023,Feb) https://cwe.mitre.org/cwss/cwss_v1.0.1.html
[16] “2022 CWE Top 25 Most Dangerous Software Weaknesses”, accessed ( 2023,Feb). https://cwe.mitre.org/top25/archive/2022/2022_cwe_top25.html
[17] [17] J. E. and R. S.. Jon Baker,( 2021), Available at: https://medium.com/mitreengenuity/cve-mitre-att ck-to-understand-vulnerability- impact-c40165111bf7
[18] “iso:22300,” ISO 22300:2018. accessed ( 2023 ,Feb), Available at: https://www.iso.org/obp/ui#iso:std:iso:22300:ed-2:v1:en
[19] M. G. Cains, L. Flora, D. Taber, Z. King, and D. S. Henshel,(2022) “Defining Cyber Security and Cyber Security Risk within a Multidisciplinary Context using Expert Elicitation,” Risk Analysis, vol. 42, no. 8, pp. 1643–1669, doi: 10.1111/risa.13687.
[20] T. J. Mohammed and N. A. Jasim, (2022) “Designing a model to protect documented information according to the integration of some international standards (ISO 27001: 2013) (ISO 10013: 2021)”, Int J Health Sci (Qassim), pp. 10684–10697, doi: 10.53730/ijhs.v6ns3.8376 .
[21] NIST, “cybersecurity.” accessed. (2023,Feb).Available at https://csrc.nist.gov/glossary/term/cybersecurity
[22] “An Introduction to the Components of the Framework.Accessed, Feb.2023, https://www.nist.gov/cyberframework/online-learning/components-framework .
[23] V. Legoy, M. Caselli, C. Seifert, and A. Peter, (2020) “Automated Retrieval of ATT&CK Tactics and Techniques for Cyber Threat Reports”, Available: http://arxiv.org/abs/2004.14322
[24] M. Tatam, B. Shanmugam, S. Azam, and K. Kannoorpatti, (2021) “A review of threat modelling approaches for APT-style attacks,”, Heliyon, vol. 7, no. 1. Elsevier Ltd, doi:
10.1016/j.heliyon.2021.e05969.
[25] C. S. Johnson, M. L. Badger, D. A. Waltermire, J. Snyder, and C. Skorupka, (2016) “Guide to Cyber Threat Information Sharing,” Gaithersburg, MD, Oct. 2016. Available at: http://dx.doi.org/10.6028/NIST.SP.800-150
[26] H. Manocha, A. Srivastava, C. Verma, R. Gupta, and B. Bansal, (2022) “Security Assessment Rating Framework for Enterprises using MITRE Health Sci (Qassim), pp. 10684–10697, Available at:https://doi.org/10.48550/arXiv.2108.06559
[27] Rahman MR, Hezaveh RM, Williams L. (2023) “What are the attackers doing now? Automatingcyber threat intelligence extraction from the text on pace with the changing threat landscape: A survey”, ACM ComputingSurveys. 55(12):1-36. Available at: https://doi.org/10.1145/3571726.
[28] CISA, “Best Practices for MITRE ATT&CK ® Mapping CHANGE RECORD.” Accessed: (2023,Feb) . Available at: https://www.cisa.gov/uscert/best-practices-mitre-attckr-mapping.
[29] Shapna Sultana Pal, (2022) “MCDM for Selection of Cybersecurity Technologies Used in Cybersecurity Education,” Doctoral dissertation, School of Engineering and Applied Sciences, George Washington University.
[30] S. Greco, M. Ehrgott, and J. R. Figueira, (2016) “Multiple Criteria Decision Analysis State of the Art Surveys”, Volume, 1&2, 2nd edition, Springer.
[31] W. K. M. Brauers, E. K. Zavadskas, Z. Turskis, and T. Vilutiene,(2010) “Multiobjective Contractor’s Ranking by Applying the MOORA Method”, Journal of Business Economics and Management, vol. 9, no. 4, pp. 245-255, Available at: https://doi.org/10.3846/1611- 1699.2008.9.245-255.
[32] S. K. Dwivedi and A. Dwivedi,(2018) “Application of MOORA and WSM method for supplier selection in manufacturing”, International Journal of Advance Research and Development (IJARND), vol. 3, issue 7, pp. 114-117.
[33] V. Kumar, M. Anjum, V. Agarwal, and P. K. Kapur, (2023) “A Hybrid Approach for Evaluation and Prioritization of Software Vulnerabilities,” in Springer Series in Reliability Engineering, Springer Science and Business Media Deutschland GmbH, , pp. 39–51. doi: 10.1007/978-3-031- 05347-4_3.
[34] D. Mashima,(2022)“MITRE ATT&CK Based Evaluation on In-Network Deception Technology for Modernized Electrical Substation Systems,” Sustainability, vol. 14, no. 3, p. 1256, Jan., doi: 10.3390/su14031256.
[35] H. Kim and H. Kim, (2022) “Comparative Experiment on TTP Classification with Class Imbalance Using Oversampling from CTI Dataset,” Security and Communication Networks, vol., pp. 1–11, Oct. 2022, doi: 10.1155/2022/5021125. [36] O. Grigorescu, A. Nica, M. Dascalu, and R. Rughinis,(2022) “CVE2ATT&CK: BERT-Based Mapping of CVEs to MITRE ATT&CK Techniques,” Algorithms, vol. 15, no. 9, Sep. 2022, doi: 10.3390/a15090314.
[37] W. Xiong, E. Legrand, O. Åberg, and R. Lagerström, (2022) “Cyber security threat modeling based on the MITRE Enterprise ATT&CK Matrix,” SoftwSyst Model, vol. 21, no. 1, pp. 157–177, doi: 10.1007/s10270-021-00898-7.
[38] Y. Liu, Y. Cheng, L. Gao, X. Liu, Q. Zhang, and J. Song, (2022)”Practical Evaluation of Adversarial Robustness via Adaptive Auto Attack.” [Online]. Available: https://github.com/liuye6666/adaptive auto attack
[39] Derbyshire, R., (2022)“ Anticipating Adversary Cost: Bridging the Threat-Vulnerability Gap in Cyber Risk Assessment”, Doctoral dissertation, Lancaster University.
[40] R. Pell, S. Moschoyiannis, E. Panaousis, and R. Heartfield, (2021)“Towards Dynamic Threat Modelling in 5G Core Networks Based on MITRE ATT&CK,”. https://doi.org/10.48550/arXiv.2108.11206
[41] S. Choi, J.-H. Yun, and B.-G. Min,(2021)”Probabilistic Attack Sequence Generation and Execution Based on MITRE ATT& CK for ICS Datasets,” in Cyber Security Experimentation and Test Workshop, Aug. , pp. 41–4.,doi:10.1145/3474718.3474722
[42] Z. Fang, M. Xu, S. Xu, and T. Hu, (2021)“A Framework for Predicting Data Breach Risk: Leveraging Dependence to Cope with Sparsity,” IEEE Transactions on Information Forensics and Security, vol. 16, pp. 2186–2201, doi: 10.1109/TIFS.2021.3051804.
[43] M. R. Rahman and L. Williams,(2022)“An investigation of security controls and MITRE ATT\&CK techniques,” .
[44] Gourisetti S. N. G, M. Mylrea and H. Patangia, (2022) “Cybersecurity vulnerability mitigation framework through empirical paradigm: Enhanced prioritized gap analysis”, Future Generation Computer Systems, vol. 105, pp. 410-431.
[45] S. G. Bhol, J. R. Mohanty, and P. K. Pattnaik,(2020) “Cyber Security Metrics Evaluation Using Multi-criteria Decision-Making Approach,” in Smart Innovation, Systems and Technologies, vol. 160, pp. 665–675. doi: 10.1007/978-981-32-9690-9_71.
[46] A. Horta, R. Holanda, and R. Marinho,(2022) “A Multi-criteria Approach to Improve the Cyber Security Visibility Through Breach Attack Simulations.”, Proceedings of the 22nd Brazilian Symposium on Information and Computational Systems Security, pp. 330-343, doi:
https://doi.org/10.5753/sbseg.2022.224454
[47] Alain Loukaka1 and S. M. Rahman,(2017)” Discovering New Cyber Protection Approaches From A Security Professional Prospective”, vol. 9, pp. 13–25. doi: 0.5121/ijcnc.2017.9402
[48] Abraham, Subil, and Suku Nair.(2015) “A predictive framework for cyber security analytics using attack graphs.” International Journal of Computer Networks & Communications (IJCNC)ISSN:0974-9322; 0975-2293. “Calculator”, Access (2023.Feb)” Available at: https://github.com/center-for-threat-informed-defense/top-attack techniques/
[49] “Accessing ATT&CK Data,” (2023). https://attack.mitre.org/resources/working-with-attack/
[50] D. J. Bodeau, R. D. Graubart, R. M. Mcquaid, and J. Woodill, (2018) “Cyber Resiliency Metrics, Measures of Effectiveness, and Scoring,”, MITER Technical Report, Public Release Case number 18-2579.
[51] “MITRE Caldera” ( 2023)., https://github.com/mitre/caldera/