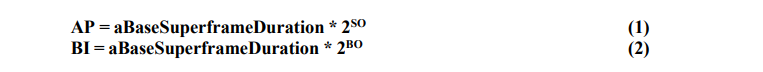IJCNC 08
A Novel Medium Access Control Strategy for Heterogeneous Traffic in Wireless Body Area Networks
Nabila Azdad and Mohamed Elboukhari
MATSI Laboratory. ESTO, Mohammed First University, 60000 Oujda, Morocco
ABSTRACT
So far, Wireless Body Area Networks (WBANs) have played a pivotal role in driving the development of intelligent healthcare systems with broad applicability across various domains. Each WBAN consists of one or more types of sensors that can be embedded in clothing, attached directly to the body, or even implanted beneath an individual’s skin. These sensors typically serve a single application. However, the traffic generated by each sensor may have distinct requirements. This diversity necessitates a dual approach: tailored treatment based on the specific needs of each traffic type and the fulfillment of application requirements, such as reliability and timeliness. Nevertheless, the presence of energy constraints and the unreliable nature of wireless communications make QoS provisioning under such networks a non-trivial task. In this context, the current paper introduces a novel Medium Access Control (MAC) strategy for the regular traffic applications of WBANs, designed to significantly enhance efficiency when compared to the established MAC protocols IEEE 802.15.4 and IEEE 802.15.6, with a particular focus on improving reliability, timeliness, and energy efficiency.
KEYWORDS
WBAN, Requirements, tailored treatment, MAC strategy, enhanced efficiency
1. INTRODUCTION
In recent years, Wireless Body Area Networks have garnered worldwide attention due to their immense potential to improve healthcare quality [1], [2]. This class of networks operates within, on, or near to the human body, utilizing one or more types of miniaturized body sensors and a single body central unit. Each sensor collects essential health data and wirelessly transmits it to the central unit, which can then display the corresponding information on a user interface or transmit the gathered data to off-site medical centers for further processing using a long-range wireless network [3].
The WBAN traffic is categorized into Normal, Emergency, and On-demand [4]. Normal traffic comprises data generated periodically or at regular intervals without any unexpected events. Emergency traffic is initiated by nodes when they exceed a predefined threshold, while Ondemand traffic is initiated by authorized personnel to acquire specific health status information.
In the overall architecture of WBANs, two levels of communications can be distinguished: intraWBAN communications taking place between sensors and the central unit, and extra-WBAN communications that allow sensory data to be transmitted to remote destinations.
Based on the literature, the great majority of the MAC protocols proposed for intra-WBAN communications are primarily derived from the beacon-enabled mode with superframe of the IEEE norms 802.15.4 and 802.15.6 [5][6]. According to our literature review, all these works try to differentiate the channel access of nodes based on their data priority or traffic category and enhance the overall network performance at the expense of some specific nodes within the regular traffic category.
In the current paper, we propose a new Fairness-oriented MAC protocol (F-MAC) for the regular traffic applications of WBAN, derived from the beacon-enabled operation of the standardized protocol IEEE 802.15.4-MAC. The main aim of our proposal is to ensure equitable access configuration among the different categories of the accommodated traffic by configuring the access of each traffic category in a way that suits it for better performance
The remainder of this paper is organized as follows. In section 2, we explain briefly the beaconenabled operation of IEEE 802.15.4. Some related works are presented in section 3. In section 4, we describe and evaluate our new protocol. Finally, section 5 concludes the paper.
2. THE BEACON-ENABLED OPERATION OF IEEE802.15.4
In the beacon-enable mode of IEEE 802.15.4 [7], [8], the channel time is divided into periodic superframe structures, at the beginning of which, the coordinator node sends a beacon frame to sensor nodes. At the reception of this frame, each body sensor gets knowledge of two important events, which are, superframe duration, and when it can transmit its data to the coordinator. This is done through two MAC parameters included in the beacon, the Beacon Order (BO) and the Superframe Order (SO).
Each superframe consists of two parts: the active part during which sensors transmit their data to the coordinator node, and the inactive part where sensors turntheir radios off and go into powersaving mode (sleep). The active period consists of 16 equally spaced slots and can be divided in turn into two sub-parts: Contention Access Period (CAP) where node contend for channel access using Slotted CSMA/CA mechanism, and an optional Contention Free Period (CFP) where up to 7 Guaranteed Time Slots (GTS) may be reserved for some specific sensor to access the channel without contention.
The duration of the active period (AP), as well as the beacon interval (BI) of IEEE 802.15.4 superframes, are respectively determined through SO and BO parameters as follows:
Where a Base Superframe Duration is the minimum superframe duration, and 0 ≤ SO ≤ BO ≤ 14
Within superframes [9], all transmissions should be synchronized with the beacon frame to take place between the superframe limits and end before the arrival of the next beacon. Furthermore, The Slotted CSMA/CA mechanism uses a basic time unit called Backoff Period (BP), the BP boundaries of every node must be aligned with the superframe slot boundaries, andeach operation of Slotted CSMA/CA can only occur at the boundary of a BP.
The contention-based mechanism Slotted CSMA/CA mainly depends on three parameters:
BE (Backoff-Exponent): Determines the duration for which a node has to wait before attempting a frame transmission (backoff). The value of BE is initialized to a variable of the CSMA/CA algorithm, namely macMinBE.
macMaxFrameRetries: This represents the maximum number of retransmissions that a node can perform before dropping a frame if no acknowledgment is received.
macMaxCSMABackoffs: This represents the maximum number of times the node will check if the channel is busy before dropping a frame.
Using this mechanism [10], whenever a node has a packet to transmit, it waits for a random value of backoff period (BP) chosen in the range of [0, 2BE–1]. At the end of this period, it performs a clear channel assessment (CCA) to sense the channel status. If the channel is continuously detected idle for CW = 2 times, it transmits one packet and waits for the acknowledgment (ack). If no ACK is received, it should repeat the process of packet transmission (up to macMaxFrameRetries times). However, if the channel is sensed busy, it increments its BE(up to macMaxBE) and repeats the CSMA/CA wait as well as the CCA execution. If the channel is detected busy even after macMaxCSMABackoffs re-attempts, no further attempt is made to send the packet.
3. RELATED WORKS
Based on the literature, the beacon-enabled mode of the IEEE 802.15.4 standard has attracted increasing interest over the last two decades, and several researchers have tried to make it more suitable for WBANs using different techniques. Some of these techniques have exploited the MAC parameters to improve the performance of the standard while remaining within the same operating logic, whereas others have changed its overall logic. The improvement(s) adopted in each technique are either static by defining new parameter settings of MAC parameters or/and a novel communication strategy, or dynamic through dynamically adapting the protocol operation according to traffic conditions. For example in [11], IEEE 802.15.4 MAC was modified bysetting the minBE parameter of some nodes to a lower value and changing it based on the traffic conditions. Due to this enhancement, the modified nodes will have more chances to transmit their data as compared to the non-modified nodes, which results in a higher throughput performance for them. In [12], a new solution is proposed to dynamically adjust the backoff exponent value depending on the buffer state of each node and to vary the number of clear channel assessments according to traffic conditions. This solution can reduce backoff delay, the probability of collision as well as the number of retransmissions in the deployed networks. In [13], a dynamic technique that adapts the size of the Contention Access Period according to the actual traffic load is proposed in combination with a new policy that avoids collisions and access congestion problem. In [14], A new adaptation is proposed for IEEE 802.15.4 MAC parameters to ensure an improved QoS for time-critical messages. In this solution, instead of having the same CSMA/CA parameters for high-priority traffic related to command frames and low-priority traffic related to data frames, authors have assigned each traffic class its own BE and CW. To achieve high energyefficiency and high performance simultaneously under IEEE 802.15.4-based networks, The authors in [15] have proposed a new algorithm that increases the active duty cycle in high traffic conditions for higher packet delivery and throughput and decreases it in low traffic conditions to save more energy. TaMAC protocol [16] is a Traffic-adaptive MAC protocol that dynamicallyadjusts the duty cycle of the sensor nodes according to their traffic patterns and data volume. It uses a configurable CAP period dedicated to transmitting short data using the Slotted Aloha access scheme while the CFP slots are used for actual data transmission. Furthermore, The TaMAC protocol uses two wakeup mechanisms: a t raffic-based wakeup mechanism for normal traffic, and a wakeup radiomechanism for emergency and on-demand traffic. PA-MAC [17] protocol prioritizes the traffic according to different data classes and divides the CAP period into four sub-phases for each priority level. Furthermore, it implements two different channels: a dedicated beacon channel (BC) and a data channel (DC). The first one is available for control information exchange. While the rest of the communication is done through the second. ATLAS protocol [18] adapts the superframe structure of IEEE 802.15.4 according to the estimated traffic load. And to avoid
energy loss associated with long-range transmission, the proposed design uses a multi-hop communication pattern. LDTA-MAC protocol [19] proposes a revised superframe structure, where the CFP and the inactive periods vary according to the dynamic allocation of GTS. The CAP is used only for sending GTS requests, while the CFP period is dedicated to data transmissions. To schedule GTS allocation time slots, the coordinator node serves at first the preexisting GTSs, and then it broadcasts a notification frame for informing nodes about an extended CFP period that will be used to serve the current allocation requests. U MAC (Urgency MAC) [20] is a contention-based MAC protocol that allows the transmission of higher priority information by reducing the number of retransmissions of non-prioritized data.
4. F-MAC:ANEW MAC PROTOCOL FOR WBAN
Based on our performance analysis of IEEE 802.15.4 presented in [9], we have noticed that although increasing the values of Slotted CSMA/CA parameters can significantly improve the performance of WBAN under low traffic conditions, it degrades the performance of networks under moderate to high traffic loads. Thus, a single choice for the values of the CSMA/CA parameters does not achieve optimum performance in all traffic conditions. On the other hand, we have noted that the manipulation of superframe parameters may enhance the QoS whatever the traffic conditions.
In this section, we propose a new Fairness-oriented MAC protocol (F-MAC) with the primary goal of ensuring equitable access to the channel among the different categories of the accommodated traffic. This is achieved by configuring the access of each category in a way that optimizes its performance. To serve this purpose, F-MAC distinguishes between two classes of traffic:
1. Light-periodic traffic: In this class, all nodes generate data at low rates (< 1000 bits/second).
2. Heavy-periodic traffic: In this class, all nodes generate data at moderate to high rates (≥ 1000 bits/second).
To implement our new protocol using the same frames of the IEEE 802.15.4 standard withoutthe need to add another frame, we have exploited the three reserved bits of the “frame control field” in the association request for transmitting the traffic class of each sensor. The value of thisfield is set to 0 if the traffic rate of the node is inferior to 1000 bits/second, and 1 if the sensor node has a packet rate superior to 1000 bits/second. The detailed operation of our protocol is discussed below
4.1. Superframe Structure of F-MAC
As illustrated in Figure 1, the structure of the first superframe in F-MAC is similar to that of the IEEE 802.15.4 and consists of two parts: a contention access period (CAP1) where nodes contend for channel access using Slotted CSMA/CA, and an inactive period. Then, each superframe is further divided into two periods: CAP1 and CAP2. CAP1 handles light traffic, while CAP2 is designed for heavy traffic. Light traffic is not allowed to access the CAP2 period,during which it should enter into sleep mode to conserve energy, and vice versa. Figure 2 shows the procedure adopted by F-MAC for communicating sensory data to the coordinator node.”
Figure 1. Transmission channel in F-MAC
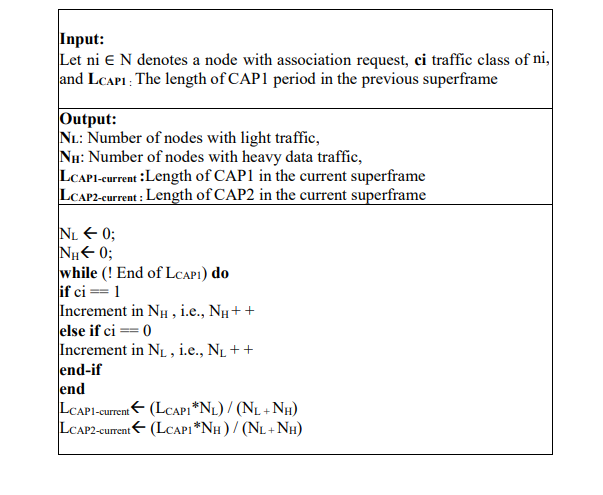
At the beginning of each superframe, the coordinator node determines the lengths of its subperiods based on the number of nodes in each traffic category. When receiving an association request from a new sensor node, it extracts the traffic class from the ‘reserved field’ of the received frame. If the field value is 0 (indicating the sensor has light data traffic), it increments NL; if the field value is 1 (indicating the sensor has heavy traffic), it increments NH (cf. Algorithm 1).”
Figure 2. F-MAC data transfer
Algorithm1: Computing the lengths of CAP1 and CAP2
4.2. Channel Access Schemes
Using Slotted CSMA/CA, sensor nodes must wait for a period of time (backoff period) before monitoring the channel status and attempting each transmission. This period is selected randomly within a range determined by the value of BE. If a node detects the channel as busy, it increments the value of this parameter and hence, its next backoff period will expand. Based on our analyses presented in [9], choosing a high value for this parameter in low traffic conditions will decrease the probability of nodes to finishing their backoff periods during the transmission process of other nodes, which improves the reliability of the deployed networks. However, when contending nodes require high data rates, the number of transmissions becomes significant, and increasing the BE value after each transmission failure will, on one hand, increase the competition time between packets. On the other hand, it will decrease the chances of nodes accessing as compared to those that did not expand their backoff periods, which increases their buffer overflow probabilities.
Based on these analyses and to achieve more reliable and fair communications, we have decided to adopt two versions of Slotted CSMA/CA in our proposal: the traditional profile of Slotted CSMA/CA for light traffic. And for heavy traffic, we have proposed a new version of slotted CSMA/CA, namely Fast-CSMA/CA (F-CSMA/CA). In F-CSMA/CA, the contending nodes will use the same value of BE during all steps of the algorithm without increasing it if the channel is sensed busy. This new version can decrease buffer overflow probabilities as well as contention time under the mentioned conditions.
4.3. Performance Analysis
4.3.1. Simulation setting
For evaluating the performance of our proposal, we have used Castalia Simulator. And we considered different network configurations, where several sensor nodes are deployed with the coordinator node (Node #0) in a star topology.
To take into consideration the rapidly changing environments of WBANs (body moving), we have used the temporal variation model provided by Castalia Simulator.
The considered performance metrics are:
- Delivery reliability (measured in terms of packets reception rate (PDR)): which reflectsthe percentage of data packets that have reached the coordinator node.
- Timeliness (measured in terms of the average transmission delay (AD)): this presents the average of the end-to-end delays of all the packets received by the coordinator node. For every packet received by the coordinator node, the end-to-end delay is defined by computing the difference between its generation and arrival times.
- Energy efficiency (EE): this presents the global cost (nJ) involving the transmission of a single bit.
Our simulations were performed under two scenarios:
- In scenario A, we set the number of nodes with heavy traffic to 10 and varied the numberof nodes with light traffic from 5 to 40. Nodes with light traffic generate 60 bits/s (5 packets/s with a payload of 1.5 bytes), while those with heavy traffic generate 18000bits / s (25 packets/s with a payload of 90 bytes).
- In scenario B, we fixed the number of nodes with light traffic at 10 and varied the number of nodes with heavy traffic from 5 to 40. Nodes with light traffic generate 80bits/s (5 packets/s with a payload of 2 bytes), while heavy traffic ones generate 20000bits/s (25 packets/s with a payload of 100 bytes).
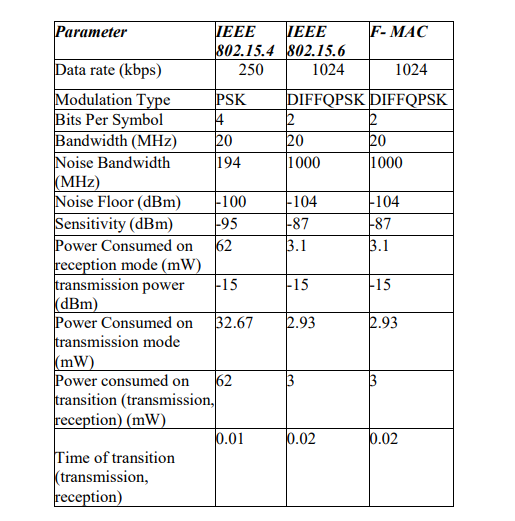
Tables 1 and 2 list the considered simulation parameters.
Table I. Radio Parameters
Table II. Simulation Parameters
For the remaining parameters, we took the default values proposed by Castalia simulator.
4.3.2. Performance Results
a) Delivery reliability
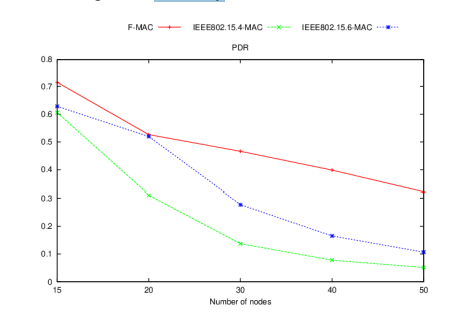
Figures 3 and 4 illustrate the evaluation results of F-MAC under the scenarios A and B in terms of PDR.
Figure 3. Reliability results under scenario A
Figure 4. Reliability results under scenario B
We can observe that our protocol ensures a significant performance improvement over the IEEE standards, reaching up to 351.85% improvement over IEEE 802.15.4 and 359.1% improvement over IEEE 802.15.6. For instance, in a WBAN consisting of 40 sensors with light traffic and 10 sensors generating heavy traffic, F-MAC achieves a Packet Delivery Ratio (PDR) of 79%, whereas the two standards do not exceed 22%.
In F-MAC, the channel access is restricted according to the traffic category. Indeed, the access during CAP1 is limited to light traffic, while the access during CAP2 is limited to heavy traffic. This restriction will, on one hand, reduce the number of collisions and, on the other hand, offer fair channel access to the different traffic categories, thus improving the deployed network reliability. However, the performance degradation observed in the topologies consisting of 10 sensors in each traffic category is due to the inefficient use of the bandwidth under such conditions. Since the number of nodes in the two categories of traffic is equal under this configuration, the period lengths of CAP1 and CAP2 will be equal, although the traffic of CAP2 is more important than that of CAP1, which degrades the efficiency of the deployed network and increases the rate of packets loss.
b) Timeliness
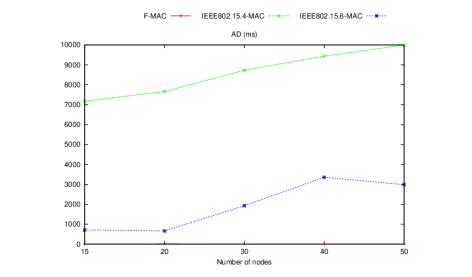
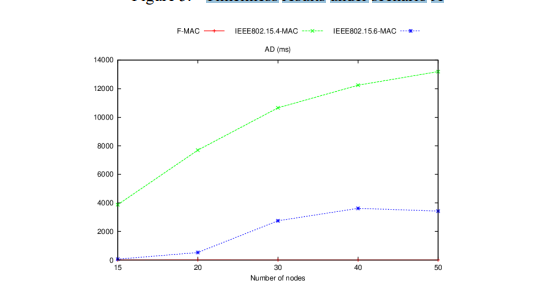
Figures 5 and 6 illustrate the delays observed in scenarios A and B.
Figure 5. Timeliness results under scenario A
Figure 6. Timeliness results under scenario B
The results obtained under the two scenarios show that our protocol provides negligible delays compared to the two IEEE standards and performs better regardless of the traffic conditions. This improvement can be attributed to the revised superframe structure, which decreases the waiting time of packets in the buffers (Queuing Delay). In addition, the fair and rapid nature of the access mechanism adopted by F-MAC under high traffic conditions strongly justifies these results.
c) Energy efficiency
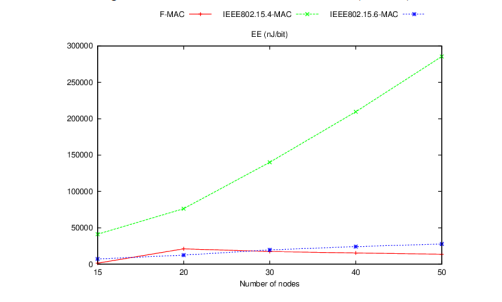
Figures 7 and 8 illustrate the performance results of F-MAC under scenarios A and B in terms of energy efficiency.
Figure 7. Energy efficiency results under scenario A
Figure 8. Energy efficiency results under scenario B
F-MAC proves to be more economical than the IEEE 802.15.4 standard and demonstrates lower power consumption than IEEE 802.15.6 in the vast majority of cases. However, the degradation observed over IEEE 802.15.6-MAC when the number of nodes with light traffic equals that of nodes with heavy traffic indicates that inefficient bandwidth utilization under suchconditions can hurt the energy efficiency of the protocol. As nodes would consume more energy while transmitting their packets. Nevertheless, this degradation is still negligible compared to the overall improvement in terms of QoS.
5. CONCLUSION
In this research, we have introduced a novel MAC protocol for the periodic heterogeneous traffic of Wireless Body Area Networks, namely, F-MAC. This protocol uses a fairness-oriented approach that aims, on the one hand, to ensure a fair access configuration among the different traffic categories, and on the other hand, to mitigate high channel contention and collisions. To evaluatethe performance of F-MAC, we have compared it with the original versions of the IEEE standards 802.15.4 and 802.15.6 under different traffic patterns using the latest version of the Castalia Simulator (3.3). Overall, the simulation results show that F-MAC performs more efficiently, regardless of the traffic conditions, and achieves significant improvements over the two norms in terms of delivery reliability, timeliness, and energy efficiency. For our future work, we plan to evaluate the performance of our protocol under other scenarios and adapt it to further traffic patterns.
CONFLICTS OF INTERESTS
The authors declare no conflict of interest.
REFERENCES
[1] V. O. Nyangaresi, “Privacy Preserving Three-factor Authentication Protocol for Secure Message Forwarding in Wireless Body Area Networks,” Ad Hoc Networks, vol. 142, p. 103117, 2023.
[2] C. A. Tavera, J. H. Ortiz, O. I. Khalaf, D. F. Saavedra, and T. H. Aldhyani, “Wearable Wireless Body Area Networks for Medical Applications,” Computational and Mathematical Methods in Medicine, vol. 2021, 2021.
[3] R. S. Pawar and D. R. Kalbande, “Optimization of quality of service using ECEBA protocol in wireless body area network,” International Journal of Information Technology, vol. 15, no. 2, pp. 595–610, 2023.
[4] N. Bradai, L. C. Fourati, and L. Kamoun, “WBAN data scheduling and aggregation under WBAN/WLAN healthcare network,” Ad Hoc Networks, vol. 25, pp. 251–262, 2015.
[5] A. Nabila, “A QoS based comparative analysis of the IEEE standards 802.15. 4 & 802.15. 6 in WBAN based healthcare monitoring systems,” presented at the 2019 International Conference on Wireless Technologies, Embedded and Intelligent Systems (WITS), IEEE, 2019, pp. 1–5.
[6] A. Nabila, “MAC Protocols for WBAN healthcare applications,” presented at the 2019 International Conference on Wireless Technologies, Embedded and Intelligent Systems (WITS), IEEE, 2019, pp.
1–8.
[7] A. M. O. Alawadhi, M. H. Omar, and N. Nordin, “IEEE 802.15. 4 MAC protocol optimisation in body sensor networks: a survey, outlook and open issues,” International Journal of Communication Networks and Distributed Systems, vol. 29, no. 3, pp. 315–340, 2023.
[8] I. Howitt and J. A. Gutierrez, “IEEE 802.15. 4 low rate-wireless personal area network coexistence issues,” presented at the 2003 IEEE Wireless Communications and Networking, 2003. WCNC 2003., IEEE, 2003, pp. 1481–1486.
[9] N. Azdad and M. el Boukhari, “Performance analysis of the beacon-enabled operation of IEEE 802.15. 4 under WBANs,” presented at the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), IEEE, 2019, pp. 1–5.
[10] A. Nabila and E. Mohamed, “An enhanced backoff strategy for fair channel access in WBAN- based health monitoring systems,” presented at the 2020 International Conference on Intelligent Systems and Computer Vision (ISCV), IEEE, 2020, pp. 1–4.
[11] J. Ko, Y. Cho, and H. Kim, “1Performance Evaluation of IEEE 802.15.4 MAC with Different Backoff Ranges in Wireless Sensor Networks,” in 2006 10th IEEE Singapore International Conference on Communication Systems, Singapore: IEEE, 2006, pp. 1–5. doi: 10.1109/ICCS.2006.301525.
[12] J. Bhar, “2A Mac Protocol Implementation for Wireless Sensor Network,” Journal of Computer Networks and Communications, vol. 2015, pp. 1–12, 2015, doi: 10.1155/2015/697153.
[13] J. Hurtado-López and E. Casilari, “3An adaptive algorithm to optimize the dynamics of IEEE 802.15. 4 networks,” presented at the International Conference on Mobile Networks and Management, Springer, 2013, pp. 136–148.
[14] A. Koubaa, M. Alves, B. Nefzi, and Y.-Q. Song, “4Improving the IEEE 802.15. 4 slotted CSMA/CA MAC for time-critical events in wireless sensor networks,” 2006.
[15] Y. Kwon and Y. Chae, “5Traffic adaptive IEEE 802.15. 4 MAC for wireless sensor networks,” presented at the International Conference on Embedded and Ubiquitous Computing, Springer, 2006, pp. 864–873.
[16] S. Ullah and K. S. Kwak, “An ultra low-power and traffic-adaptive medium access control protocol for wireless body area network,” Journal of medical systems, vol. 36, no. 3, pp. 1021–1030, 2012.
[17] S. Bhandari and S. Moh, “A priority-based adaptive MAC protocol for wireless body area networks,” Sensors, vol. 16, no. 3, p. 401, 2016.
[18] M. Rahman, C. S. Hong, S. Lee, and Y.-C. Bang, “ATLAS: A traffic load aware sensor MAC design for collaborative body area sensor networks,” Sensors, vol. 11, no. 12, pp. 11560–11580, 2011.
[19] C. Li, B. Hao, K. Zhang, Y. Liu, and J. Li, “A novel medium access control protocol with low delay and traffic adaptivity for wireless body area networks,” Journal of medical systems, vol. 35, no. 5, pp. 1265–1275, 2011.
[20] K. A. Ali, J. H. Sarker, and H. T. Mouftah, “Urgency-based MAC protocol for wireless sensor body area networks,” presented at the 2010 IEEE international conference on communications workshops, IEEE, 2010, pp. 1–6.
AUTHORS
Nabila Azdad received a Master’s degree in “Intelligent Systems and Networks” from the Faculty of Sciences and Technologies, Fez, Morocco, in 2016. She is currently a PhD in MATSI Laboratory at Mohammed First University, Oujda, Morocco. Her research interests include wireless sensor networks and
mobile healthcare.
Mohamed Elboukhari received an MSc degree in computer science in 2005 from the University of Science, Oujda, Morocco. He is currently a professor at the University of Oujda in the field of computer science. His research interests include web tracking, and wireless network security.