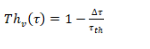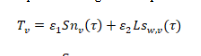IJCNC 03
IOT-BASED MOBILE ADAPTIVE ROUTING ALGORITHM IN A UBIQUITOUS NETWORK
Prasanna Kumar G and Dr. Shankaraiah N
Department of Computer Science and Engineering, Sri Jayachamarajendra College of
Engineering, Mysuru, Karnataka, India
ABSTRACT
Nowadays, there is a rapid increase in the population throughout the globe and causing more urbanization in the landscape. Advanced medical monitoring and disaster relief require more reliable, long-range communication, feasible, and high connectivity with increased accuracy. The Internet of Things (IoT) has revolutionized the way we interact with technology and has led to the emergence of a new class of interconnected devices. These devices rely on efficient and reliable networking to communicate with each other and with the outside world. The proposed work presents an IoT-based mobile adaptive routing algorithm (IOT-MARA) that is designed to work in a ubiquitous network, where a large number of devices are connected and can move around. The proposed algorithm is an adaptive algorithm that can adjust its routing decisions based on the current state of the network and the devices that are connected to it. The algorithm considers the mobility of devices and the dynamic nature of the network to select the most efficient path for data to travel. It also aims to minimize network congestion and improve overall network performance. Simulations are used to evaluate the IOT-MARA algorithm and the results show that it outperforms existing routing algorithms in terms of network throughput, delay, and energy consumption. The proposed algorithm is helpful in the field of ubiquitous networking because it addresses the challenges of mobility and dynamic network conditions during a fire mishap scenario. This research has implications for the design and deployment of Ubiquitous Networks for the development of future communication systems.
KEYWORDS
Wearable Wireless Sensor Secure System, Ubiquitous networks, IoT-based mobile adaptive routing algorithm, Emergency management unit.
INTRODUCTION
Wearable wireless sensor systems (WRWSSS) have shown rapid development in recent years in the application of the Internet of Things (IoT) [1-3]. The firefighter’s biggest enemy in the event of a large-scale fire is not only the fire itself, but also toxic, smoke, harmful gases, and high temperature, which is very difficult for human detection. The fire-fighters may fall into a coma when they came into contact with these dangers. During this time, they may not be able to call for any help and the situation may reach too unexpected. Therefore, it is necessary to have a system to provide early warning to people to save their lives [4]. The needed ubiquitous network for this purpose will not only collect environmental and human information, but it should also provide an early warning signal. In this regard, WRWSSS has the best choice for the purpose.
A traditional WRWSSS structure in a fire scenario is combined with the people movement rule and unreachable range distribution. The ubiquitous network consists of several fire fighters, connectors, and a Base Station [5]. The connector and firefighters both have controller nodes and general sensor nodes. The physiological information, such as blood pressure, electrocardiogram
(ECG), and heart rate of the nodes is monitored using general sensor nodes. The general sensor node information is collected by the controller node [6]. Figure 1 shows the ubiquitous network transmission divided into three processes: 1) the collected data by the controller node is sent to the destination node, 2) the exchange of the data between the controller node and sensor nodes, 3) communication is performed by the connector with the Base Station.
Figure 1. Fire Rescue Scenario Network Structure
In the present study, we constructed a WRWSSS and developed the trust value of the Internet of Things-based mobile adaptive routing algorithm (IoT-MARA) to communicate between controller nodes for fire scenarios. The contributions are as follows:
- The fire scenario routing requirements were analyzed and a suitable structure for WRWSSS was developed with IoT-MARA [16]. The developed algorithm has two stages; route identification and maintenance.
- In the stage of route identification, the different request zones were designed by adopting different transmission distances [17]. To handle routing holes, the processing method was also designed. The algorithm called location-aided routing for multiple request zones (LAR- MRZ) is developed using these two schemes.
- In the stage of routine maintenance, trust values are established using lines and nodes. The stability of the node is calculated according to the state of node movement and neighbour node model, and the stability of the link is calculated based on the link maintenance time between nodes and the quality of wireless propagation [18].
ALGORITHM FOR ROUTING IDENTIFICATION
Route identification and node prediction are done based on location-aided routing, but it has several issues.
- The zone request design is not reasonably processed, and the number of multiple requests in the same routing location divides into circular and rectangular shapes [19]. Initially, it is suitable for middle distance route discovery, and further route discovery for short-distance [20]. But both techniques are not a good choice for the discovery of long-distance.
- The routing holes are not considered in the general scenario, but they are considered in the scenario of fire due to flame exceeding when the unreachable range occurs [21]. In the present work, we have developed an algorithm to address these problems. For a request zone, this algorithm finds a reasonable range and gives the technique for dealing with the routing holes [22]. The notation used in the LAR-MRZ algorithm is shown in Table 1.
2.1. Selection of Request zone
The different request distances such as short, medium, and long are adapted by designing the three-request zone mode, and Algorithm 1 shows the process of selection [23-27]. Figure 2 shows the comparison of three request zones and the distance ratio idea is represented in equation 1 when , less distance between the source and destination nodes, when , expansion of the source node when larger distance between the source and destination [28].
———-Figure 2. Three request zones comparison in ubiquitous network.
Where is represented the node at the middle part of the expected zone, is described the node at the source side and is identified as the expected zone radius.
Table 1.Abbreviations
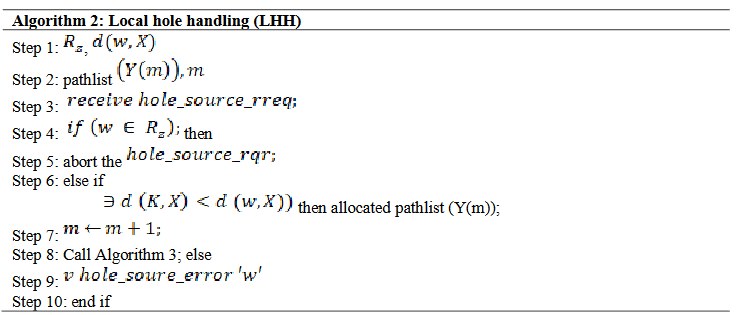
2.2. Handling of Routing Hole
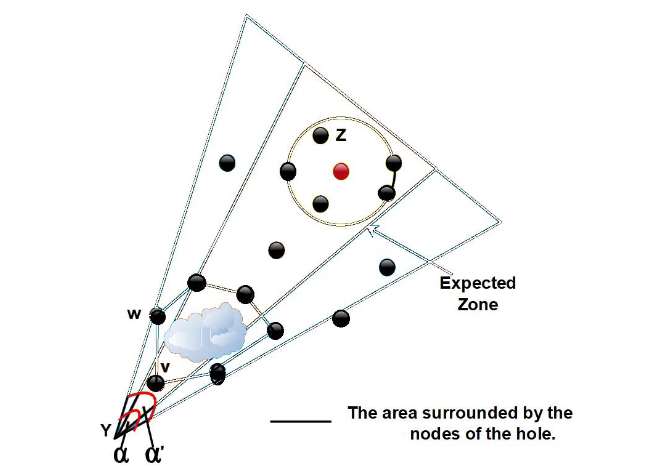
As the flame increases in a fire scenario, the discovery of route repetitions, route setting time, and route overhead create the routing holes [29]. For long-distance transmission, the proposed strategy of the triangular zone is enhancing the probability of routing holes. To solve the routing holes two methods are proposed such as local processing and global processing. Global processing is used when local processing is failed. Even if global processing failed, the ubiquitous network is flooded and the worst-case scenario occurs [30]. Figure 3 shows the basic idea of local processing algorithm. The process of routing holes is represented in Algorithm 2. Where ‘w’ is represented as neighbour node of node ‘v’, is described as data packet request to the nodes and ‘m’ is represented the number of nodes in the zone [31].
Figure 3Process of route discovery in ubiquitous network
2.3. Number of Multiple Requests in the Same Routing Location
It is common for multiple requests to be sent to the same routing location in a network or system, as routing locations are typically designed to handle multiple requests at once. The process is divided into three sections: request of the route, processing of the hole, and route replay [32-35]. The process of the hole is carried out in two ways: local processing and global processing. Initially, the source node starts processing the local hole if it finds the hole during the discovery of routing. If local processing fails, then it switches to global processing. The developed pseudocode for each step is given below.
2.3.1. Number of Multiple Requests in the Same Routing Location Pseudo-code
From steps 1-6 request of the route request (RQR) to the process of route finding. Further from step 7-9 followed by the hole processing, and the last steps 10-12 show the process of route replay (RRP). The request zone of the source node expanding is shown in Figure 4 [36].
The packet RQR in step 3 is described as follows
Table 1. Abbreviations
Figure 4. The request zone of Source node expanding
ALGORITHM FOR ROUTING MAINTENANCE
There are a variety of routine maintenance algorithms that are used in different networking contexts like Link-state routing, Distance-vector routing, Path-vector routing, Hybrid routing, Hierarchical Routing, etc. These are just a few examples of routing maintenance algorithms, and the specific algorithm used will depend on the needs of the network and the devices it is being used on. The nodes in the WRWSSS become disconnected in a fire scenario. Hence, the process of route maintenance must be incorporated. In the present study, we established the trust value between pair nodes [37]. Trust management in a decentralized network is particularly challenging due to the lack of centralized communication infrastructure and the fast varying feature of the node movement in the environment. This has been used to represent the node’s links and trust values. Further, the RMA-TV basis is formed and routing maintenance is done with the trust values. The maintenance of routing has been done at the two stages. The fault pre-processing is done at the first stage and trust value is evaluated between the nodes during the data transmission.
3.1. Stability of Node
The Stability of a node in a network refers to the ability of the node to maintain its connectivity and function properly. A stable node can consistently receive and transmit data and is not vulnerable to frequent disconnections or malfunction. The following points are discussed to understand the proposed method.
3.1.1. Remaining Time
The node lifetime can be improved with the energy consumption speed and remaining energy. Hence, is used to represent the remaining time of the node and defined the remaining lifetime as equation 3.
Where, is represented as residual node energy at a time and is described as a residual node at the initial time. Within the threshold the linear relationship is used to represent the remaining lifetime of the node as given in equation 4 [38].
Where is represented the threshold of linear relationship at time, is described as thethreshold value set for the remaining time and is identified as zero when no node is available.
3.1.2. Neighbor Node Model
There are two neighbor nodes having each control node. The first neighbor nodes are in the body of the other node and one node is a set control node that acts as a reference point [39-41]. The reference point in the ubiquitous network and other nodes are having a close relationship. The neighbor nodes in the second type act as the control nodes on other bodies and it follows the mobility model with random walking.
3.2. Trust Value
The trust value denoted by which is a combination sum of node stability and link stability is represented as given in equation 5 and its operation is represented as shown in Figure 5.
(5)
Where, is defined as node stability, is represented as line stability and the weight coefficients are represented by and .
Figure 5. Nodes relative movement
3.3. Algorithm
The algorithm for data transmission is as follows:
3.3.1. Preprocessing
Once the discovery process of the route is done, the transmission data path assumed to follow the path is shown in Figure 6. Own node stability is maintained to exchange data with the neighbours. The node is set to the latest stability, during the data packet transmitted through the node and it transmitted it to the ubiquitous network. The data packet is sent to the next node, this node finds the trust value and the link stability. The calculated trust value if it is less than the threshold value, the corresponding link is marked as shown in Figure 7. Between the node C and D trust value satisfies the condition < then pre-processing mechanism is started by node D.
The detailed steps for pre-processing at RMA-TV are described below:
1. To maintain node stability Node D has to exchange packets with neighbour nodes periodically.
2. The trust value between nodes D and C is calculated when a packet passes through D.
3. As per the process given in Table 2 between D and C is the trust state St is obtained.
4. The processing goes to step 6 if St = 1, otherwise, go to step 5.
5. D re-establishes a path by disconnecting from C.
6. In the packet header mobile state of C is replaced by D and forwards the packet
Figure 6. Diagram for simplified data transmission
Figure 7.Between C and G case of distrus
3.3.2. Reverse repair
The reverse repair mechanism is used when the link fails while connecting trusted nodes. There may be damage to the ubiquitous network if the link is unidirectional in a fire scenario. Example node D i.e. next hop node will collect the first when previous node C is damaged.
Once a link is disconnected the procedure for the route is repaired and is as follows
Step 1: The process of route repairs starts once node D finds it is disconnected from node C.
Step 2: Local route repairs is started by Node D, it goes to step 3 if the search sues otherwise go
to Step 5.
Step 3: the request packet from node D is received by Node B and the attribute of the packet are
verified.
Step 4: remaining packets send by node D through the founded path to C.
Step 5: the discovery process started by Node D to the source node A.
Step 6: The request packet is received by node A from Node D and checks the attribute of the
packet.
Step 7: node D waits for the packet to time out to declare that the maintenance has failed.
Step 8: End.
ANALYSIS OF SIMULATION RESULTS
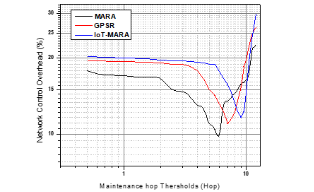
The ubiquitous network simulator tool NS2 is used to validate the proposed method. The area for the simulation is set with a dimension of 1800 m × 840 m. Node 1 is set as Base Station and 50 firefighters are comprised in IoT-MARA. The frequency set for the simulation was 12.5 ms/time and the length of the packet is 50 bytes. The range of 0–12 m/s is selected as the node moving speed. As the increases the number of hopes, the overhead of ubiquitous network control decreases as shown in Figure 8. Further overhead of the ubiquitous network is minimized by limiting the number of hops to 5.
Figure 8. The different hop thresholds for ubiquitous network vs control overhead
The performance of the proposed IoT-MARA algorithm is compared with the location-aided algorithm Greedy Perimeter Stateless Routing (GPSR) and Ad-hoc On-demand Distance Vector routing (AODV). In delivering the packet, the effect on the packet delivery rate is determined by the speed of nodes as shown in Figure 9. The rate of the packet delivery is gradually declined with increasing the speed of moving node. The increase in the moving speed may lead to packet loss and reduces the node’s stability. During the nodes low-speed moving, we can observe the packet delivery rate has increased in MARA. The simulated results show that IoT-MARA is a good choice for WRWSSS low-speed mobile nodes
Figure 9. Nodes moving speed vs packet delivery rate
The three algorithms’ end-to-end delay is observed with the moving speed of the node being increased as shown in Figure 10. This analysis indicates that IoT-MARA provides the better result as compared to other algorithms.
Figure 10. Nodes moving speed vs End-to-end dela
The packet loss rate of the node is depending on the link quality. Figure 11 shows the link quality impact of three algorithms. In the simulation, it is observed that three algorithms are relatively similarly performed when LQI > 120, but IoT-MARA has been shown to provide advantages when LQI < 120. Hence the proposed method is the best option for fire scenarios.
Figure 11. Link quality vs Packet loss rate(%)
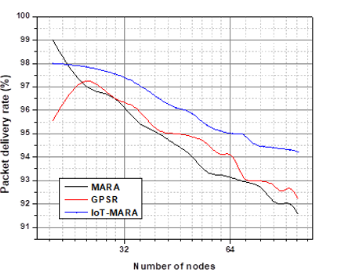
In the simulation, it is observed that as the number of nodes increased the delivery rate of the packet decreased. Figure 12 shows the relationship between the delivery rate of the packet and the number of nodes. The simulation results show that IoT-MARA has performed better as compared to other algorithms.
Figure 12. Representation of number of nodes vs packet delivery rate
The analysis of end-to-end delay in the number of nodes is carried out and corresponding simulation results are shown in Figure 3. In the simulation results it is observed that when the number of nodes increased from 20 to 40, the delay decreased gradually. Similarly, when nodes increased from 60 to 80 density of the node decreased. This result analysis indicates the IoT- MARA provides the better result as compared to other two algorithms.
Figure 13. Numbers of nodes vs End-to-end delay
CONCLUSION
In this paper, the proposed IoT-MARA in ubiquitous wireless sensor network performs effectively in large-scale fire scenarios by utilizing IoT devices and sensors concerning the network control overheads, packet delivery rate, end-to-end delay (ms), and pack loss rate as compared to conventional methods. The performance analysis has been done by considering standard parameters for analysis and comparison purpose. In WRWSSS ubiquitous network, performance analysis has been done on a set with a dimension of 1800m * 840m, frequency set of 12.5 ms/time, packet length 50 bytes, and node moving speed 0 12m/s. By considering the above standard parameters, the simulation and comparative analysis have been done with respect to the network control overhead. From the results, the proposed method shows better performance as compared to MARA and GPSR by 1.1% and 0.8% respectively. With respect to the simulation results, the proposed method shows better performance in packet data delivery of about 0.75% and 0.35% more as compared to conventional methods MARA and GPSR respectively. With respect to the simulation results, the proposed method shows better end-to-end delay (in ms), which is reduced about 0.25% and 0.15% as compared to conventional methods MARA and GPSR respectively. With respect to the simulation results, the proposed method shows better performance by considering packet loss rate (ms) of about 0.123% and 0.1% less as compared to conventional methods MARA and GPSR respectively. So, the proposed IOT- MARA performs better in a ubiquitous network scenario.
Future scope: when more wearable wireless sensor system is adopted in ubiquitous wireless sensor network, then there is fault data injection, abnormal behaviour and increased malicious activities in smart cities. In such conditions, the proposed method can be enhanced for the identification process of the trust value of ubiquitous wireless sensor networks in the huge cloudy region and their classification.
CONFLICTS OF INTEREST
The authors declare no conflict of interest.
ACKNOWLEDGEMENTS
The authors would like to thank everyone, just everyone!
REFERENCES
1] Amar, Mohamed Abdellahi & Khaznaji, Walid & Horchani, Leila., (2020) “PTSP Solution Strategy for Motion Trajectory of UAV in Ubiquitous Sensor Network”. Procedia Computer Science. Vol. 176. pp. 3191 3199.
[2] Chavan, Chandrashekhar & Venkataram, Pallapa., (2022) “Design and implementation of event- based multicast AODV routing protocol for ubiquitous network” Array. Vol. 14. pp100-129.
[3] Ladas, Alexandros & G C, Deepak & Pavlatos, Nikolaos & Politis, Christos., (2018) “A Selective Multipath outing Protocol for Ubiquitous Networks”. Ad Hoc Networks. Vol. 77.
[4] M. Abdujapparova, (2010) “Anti-Net is adaptive agent-based routing algorithm,” 4th International Conference on Application of Information and Communication Technologies, pp1-4.
[5] Kanth, Rajeev, Tuomas Korpi, Arto Toppinen, Kimmo Myllymäki, Jatin Chaudhary, and Jukka Heikkonen.(2019) “Educational Approach to the Internet of Things (IoT) Concepts and Applications.” In 6th International Conference on Computer Science, Engineering and Information Technology (CSEIT-2019). Aircc Publishing Corporation, vol. 11232019, pp. 233-247.
[6] Gurumallu, Prasanna Kumar and Shankaraiah.(2022) “NLADSS: Design of Connectivity as a Service (CaaS) Model using Node-Level Augmentation & Dynamic Sleep Scheduling for Heterogeneous Wireless Network Handoffs.” International Journal of Intelligent Engineering and Systems n. pp1-11.
[7] Kiran Ahuja & Arun Khosla, (2019) “Network selection criterion for ubiquitous communication provisioning in smart cities for smart energy system”, Journal of Network and Computer Applications, Vol. 127 pp82-91.
[8] P. Dahiya & R. Johari, (2014) “VAST: Volume adaptive searching technique for optimized routing in mobile ad-hoc networks”, IEEE International Advance Computing Conference (IACC), pp1-6.
[9] A. Barolli, M. Takizawa, F. Xhafa & L. Barolli, (2010) “Application of Genetic Algorithms for QoS Routing in Mobile Ad Hoc Networks: A Survey”, International Conference on Broadband, Wireless Computing, Communication and Applications, pp250-259.
[10] J. I. De Irigon, “Adaptive Routing in Disruption Tolerant Networks” (2019) IEEE 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), pp1-3.
[11] Shivaji, R., Nataraj, K.R., Mallikarjunaswamy, S., Rekha, K.R., (2022) “Implementation of an Effective Hybrid Partial Transmit Sequence Model for Peak to Average Power Ratio in MIMO OFDM System”, Lecture Notes in Electrical Engineering, Vol. 783.
[12] Q. Li, C. Li & J. Li, (2010) “Data Aggregation Algorithm Based on Grid and Adaptive Genetic Algorithm for Wireless Senor Networks with a Mobile Sink,” 2nd International Workshop on Intelligent Systems and Applications, pp1-4.
[13] S. Liu, T. Fevens & A. E. Abdallah, (2008) “Hybrid Position-Based Routing Algorithms for 3D Mobile Ad Hoc Networks”, The 4th International Conference on Mobile Ad-hoc and Sensor Networks, pp177-186.
[14] R. K. Ambekar & U. D. Kolekar, (2017) “AFL-TOHIP: Adaptive fractional lion optimization to topology-hiding multi-path routing in mobile ad hoc network”, International Conference on I- SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), 2017, pp727-732.
[15] X. Feng, (2011) “A Routing Algorithm for Supporting Soft-QoS in Mobile Ad Hoc Networks”, 7th International Conference on Wireless Communications, Networking and Mobile Computing, 2011, pp1-4.
[16] G.F. Ali Ahammed, Reshma Banu (2010) “Analyzing the Performance of Active Queue Management Algorithms”, International Journal of Computer Networks & Communications, Vol. 2, No. 2, pp 1-19. International Journal of Computer Networks & Communications (IJCNC) Vol.15, No.3, May 2023 49
[17] N. Fathima, A. Ahammed, Rajashekarappa, R. Banu, B. D. Parameshachari and N. M. Naik, “Optimized neighbor discovery in Internet of Things (IoT),” 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), Mysuru, India, 2017, pp. 1-5, doi: 10.1109/ICEECCOT.2017.8284573..
[18] M. Kavalerov, Y. Likhacheva & Y. Shilova, (2017) “A reinforcement learning approach to network routing based on adaptive learning rates and route memory,” SoutheastCon 2017, pp1-6.
[19] W. K. Al-Assadi & S. Mishra, (2019) “Adaptive Routing Algorithm for Offshore Oil Spill Wireless Sensor Networks,” SoutheastCon, 2019, pp1-4.
[20] Islam, M. S., Riaz, M. A., & Tarique, M. (2012). Performance Analysis of the routing protocols for video streaming over mobile Ad Hoc networks. International Journal of Computer Networks & Communications (IJCNC), Vol. 4, No. 3, pp 133-150.
[21] S. Giannoulis, A. Prayati, C. Antonopoulos & G. Papadopoulos, (2009) “A.MO. R: An adaptive routing mechanism for WSN health applications”, 3rd International Conference on Pervasive Computing Technologies for Healthcare, 2009, pp1-4.
[22] S. Ling & W. Wei, (2009) “Feedback Adaptive Routing Algorithm for DTN,” WRI International Conference on Communications and Mobile Computing, 2009, pp267-271.
[23] Y. Shilova, M. Kavalerov & I. Bezukladnikov, (2016) “Full Echo Q-routing with adaptive learning rates: A reinforcement learning approach to network routing”, 2016 IEEE NW Russia Young Researchers in Electrical and Electronic Engineering Conference (EIConRusNW), 2016, pp341- 344.
[24] M. Bui, A. K. Datta, O. Flauzac & D. T. Nguyen, (1999) “Randomized adaptive routing based on mobile agents,” Proceedings Fourth International Symposium on Parallel Architectures, Algorithms, and Networks (I-SPAN’99), 1999, pp. 380-385.
[25] Xin Jin, Hongbo Wang, Yaoxue Zhang & Dong Chang, (2003) “A dynamic self-adaptive routing update algorithm for MANET”, International Conference on Communication Technology Proceedings, 2003. ICCT 2003., pp909-912.
[26] C. He, R. Wang, D. Wu, Z. Tan & N. Dai (2022) “Energy-Aware Virtual Network Migration for Internet of Things Over Fiber Wireless Broadband Access Network,” IEEE Internet of Things Journal, Vol. 9, No. 23, pp. 24492-24505.
[27] (2016) “Ubiquitous green community control network — Control and management”, in ISO/IEC/IEEE 18881 First Edition 2016-04-15 , pp1-65.
[28] S. H. Choi, H. -K. Park, N. H. Kim, S. -H. Kim & Y. Yu, (2008) “Design of A Power-, Delay-, and Emergency-Efficient Protocol of Ubiquitous Sensor Network Systems for Silver Town Applications”, 2008 Second International Conference on Future Generation Communication and Networking, pp. 306-309.
[29] W. Da-peng, F. Si-long, L. Yi & L. Peng-wen, (2012) “Messsage Spreading Estimating Methods in Ubiquitous Networks,” 2012 International Conference on Computer Distributed Control and Intelligent Environmental Monitoring, pp403-406.
[30] Yoon-Sik Yoo and Jae-Doo Huh, (2006) “Bedside Sensor Platform Architecture for UbiSAS in Ubiquitous Sensor Network,” 2006 8th International Conference Advanced Communication Technology, pp. 515-518.
[31] K. B. Letaief,(2009) “Pathways towards Next Generation Cognitive Ubiquitous Networks (Keynote Lecture),” 2009 WRI International Conference on Communications and Mobile Computing, 2009, pp3-3.
[32] Singh, Dhananjay and Singh, Sanjay and Singh, Madhusudan and Kew, Hsein-Ping and Jeoung, Do- Un and Tiwary, U. S. and Lee, Hoon-Jae, (2009) “IP-based ubiquitous sensor network for in-home healthcare monitoring,” 2009 International Multimedia, Signal Processing and Communication Technologies, pp201 204.
[33] M. Marciniak, (2006) “Reliability for Future Ubiquitous Network Societies Challenges and Opportunities,” 2006 International Conference on Transparent Optical Networks, pp130-131.
[34] We-Duke Cho, Sung-Soo Kim & Hong-Jin Yeh, (2004) “Introduction to the “uAuto” project – ubiquitous autonomic computing and network,” Second IEEE Workshop on Software Technologies for Future Embedded and Ubiquitous Systems, 2004. Proceedings., pp24-26.
[35] H. Kemis, N. Bruce, Wang Ping, T. Antonio, Lee Byung Gook & Hoon Jae Lee, (2012) “Healthcare monitoring application in ubiquitous sensor network: Design and implementation based on pulse sensor with arduino,” 2012 6th International Conference on New Trends in Information Science, Service Science and Data Mining (ISSDM2012), pp34-38. International Journal of Computer Networks & Communications (IJCNC) Vol.15, No.3, May 2023 50
[36] V. V. Ayyannavar & L. B. Bhajantri, (2022) “Fault Analysis and Identification in Ubiquitous Networks using Cognitive Agents Approach,” 2022 International Conference on Electronics and Renewable Systems (ICEARS), pp713-719.
[37] S. Kuwano, Y. Suzuki, Y. Yamada & K. Watanabe, (2006) “Digitized Radio-over-Fiber (DROF) System for Wide-Area Ubiquitous Wireless Network,” 2006 International Topical Meeting on Microwave Photonics, pp1 4.
[38] Maleki, Morteza, Karthik Dantu, and Massoud Pedram.(2003) “Lifetime prediction routing in mobile ad hoc networks.” In 2003 IEEE Wireless Communications and Networking, 2003. WCNC 2003., vol. 2, pp. 1185-1190.
[39] H. Park, E. -H. Paik and N. Kim,(2009) “Architecture of Collaboration Platform for Ubiquitous Home Devices,” 2009 Third International Conference on Mobile Ubiquitous Computing, Systems, Services and Technologies, pp. 301-304.
[40] S. Y. Pao, A. J. Reben and A. Rayes, (2011) “MoSS: Mobile Smart Services for ubiquitous network management,” 2011 International Conference on Collaboration Technologies and Systems (CTS), pp. 48-52.
[41] W. Wang, W. Guo & W. Hu, (2018) “Network Service Slicing Supporting Ubiquitous Access in Passive Optical Networks,” 2018 20th International Conference on Transparent Optical Networks (ICTON), pp. 1-3
AUTHORS
Prasanna Kumar G received his Bachelor of Engineering in Computer Science and Engineering from Coorg Institute of Technology, Ponnampet, affiliated to Visvesvaraya Technological University, Belgaum, Karnataka, and obtained his Master’s Degree in the area of Networking and Internet Engineering from Sri Jayachamarajendra College of Engineering, Mysore, autonomous under Visvesvaraya Technological University, Belgaum, Karnataka. He is pursuing his Ph.D. under the guidance of Dr. Shankaraiah in the area of Ubiquitous Networks. His research interests include Computer Network, Mobile Communication and Machine Learning. At present he is working as Assistant Professor in the Department of Information science and Engineering at NIE Institute of Technology, Mysuru, Karnataka, India.
Dr. Shankaraiah N received his B.E. degree in Electronics and Communication Engineering from Mysore University, Mysore, India, in 1994, M.Tech. Degree in Digital Electronics and Communication Systems from Mysore University in 1997.He completed Ph.D. under the guidance of Prof. P.Venkataram, Dept. of ECE, IISc., Bangalore. He has Investigated a transaction based QoS, Resource management schemes for mobile communications environment. He has more than 20 years of teaching experience in Engineering. He has published more than 20 papers in national and international journals and conferences. He is a reviewer and chair for many conferences. His research interest includes bandwidth management, Quality of Service (QoS) management, topology management, and Energy management. He is a student member of IEEE and life member of India Society for Technical Education (LMISTE). He is presently working as Professor and Head, in the Department of E&C at Sri Jayachamarajendra College of Engineering, Mysuru, Karnataka, India.